TL;DR on CVE-2022-26134
- GreyNoise Research is tracking the critical-rated zero-day vulnerability CVE-2022-26134 in our tag “Atlassian Confluence Server CVE-2022-26134 OGNL Injection Attempt”
- This OGNL injection vulnerability allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance, and Confluence versions as old as 1.0.3 are vulnerable.
- Atlassian released a security advisory for CVE-2022-26134 on 2-Jun-22.
- As of 3-Jun-22, Atlassian has released patches and a temporary workaround to address the issue.
- GreyNoise is currently observing a steady increase in the number of IPs attempting to exploit this vulnerability.
- Due to the nature of disclosure and intensity of ongoing exploitation, GreyNoise advises to assume compromise.
- Download the latest list of IPs trying to exploit this vulnerability here for use in analysis and temporary blocking
UPDATE: 8-Jun-22
Clustered CVE-2022-26134 Payloads as Observed by GreyNoise
GreyNoise has observed a number of variations of CVE-2022-26134 payloads with various intent. Shown below is a visualization of clusters of related payloads.
• IPs are removed from payloads for normalization
• Each node is a unique payload after normalization
• Each connection between nodes is when 2 nodes share a similarity score >85 using ssdeep
• Significantly dynamic payloads will not share similarity with other payloads and do not appear in the visual

If you'd like more detail, we've created a PDF "Clustered CVE-2022-26134 Payloads as Observed by GreyNoise;" click here.
Note, we have also added a list of C2 IPs we've extracted for CVE-2022-26134 to our Datashots API, free to all users: https://api.greynoise.io/datashots/cve-2022-26134/manifest.json which includes:
- A continuously updated list of C2 IPs extracted from payloads
- A PDF containing Clustered IOCs (Indicators of Compromise) of all observed payloads
Vulnerability Overview - CVE-2022-26134
On 2-Jun-22, Atlassian released a security advisory to address a remote code execution vulnerability (CVE-2022-26134) affecting all supported versions of Confluence Server and Data Center products. An unauthenticated, remote attacker could exploit this vulnerability to execute code remotely. Atlassian reports that there is known exploitation of this vulnerability.
The zero-day vulnerability was initially discovered by cybersecurity firm Volexity. In a coordinated disclosure, Volexity explained that the vulnerability was discovered over the Memorial Day weekend while performing incident response. After conducting an investigation, Volexity could reproduce the exploit against the latest Confluence Server version and disclosed it to Atlassian on May 31st.
"After a thorough review of the collected data, Volexity was able to determine the server compromise stemmed from an attacker launching an exploit to achieve remote code execution," explains a blog post by Volexity. "We were subsequently able to recreate that exploit and identify a zero-day vulnerability impacting fully up-to-date versions of Confluence Server."
Confluence Security Advisory 2022-06-02 identifies which versions were affected, and the company has issued patches for the flaw, as well as recommended temporary workarounds until the fixes can be applied.
Cybersecurity firm Shodan has identified internet-facing Confluence systems in this search query:
Given the severity of the vulnerability and ease of exploitation, GreyNoise advises organizations to:
- Apply mitigations or patch immediately on an emergency basis.
- If you are unable to apply these mitigations, we recommend you restrict or disable Confluence Server and Confluence Data Center instances immediately.
- Consider implementing IP address blocking rules against hosts actively attempting to exploit this vulnerability in the wild.
Observed In The Wild
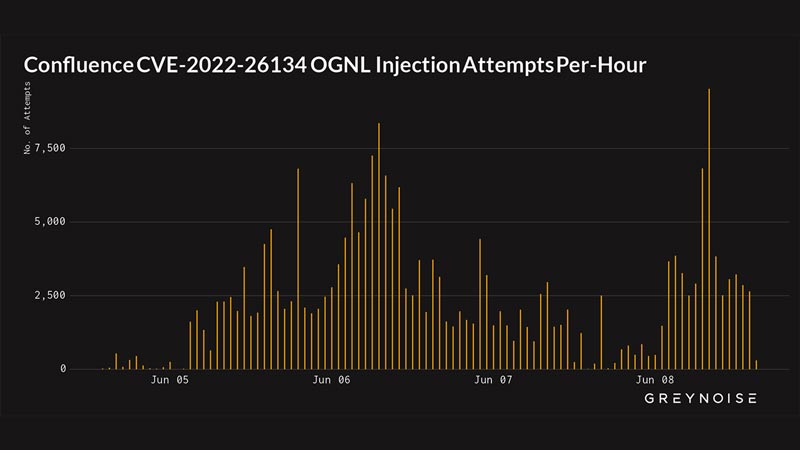
GreyNoise Trends for Atlassian Confluence Server CVE-2022-26134 OGNL Injection Attempt:
As of 6-Jun-22 at 7:00 pm UTC, GreyNoise has observed over 850 unique IP addresses attempting to exploit the Atlassian Confluence Server OGNL Injection Attempt vulnerability, CVE-2022-26134.
Below are a set of observations from the GreyNoise Research team based on the mass exploitation activity for this CVE that we’ve captured via our passive global sensor network:
Scale of attacks
Around a third of GreyNoise sensors have been hit with this attack by a rising number of IP addresses. We have identified over 800 unique IPs in the first week of public proof of concept release, which makes this vulnerability in line with CVE-2021-44228 Apache Log4J exploitation traffic. The potential source of this large number of unique source IPs is the ease of exploitation mixed with the high-value target of Atlassian Confluence databases. The value of these databases is due to Confluence customers potentially storing important information like secrets, passwords, and proprietary knowledge in this documentation platform.
Source of attacks
- Most exploit attempts have originated outside of VPNs or TOR exit nodes.

- Normally malicious attackers primarily use anonymizers, but GreyNoise sensors are seeing a small amount of TOR traffic in comparison to VPN or non-anonymized traffic.
- Attackers that are utilizing VPN are largely using Nord VPN.

- 90% of requests match the current Rapid7 PoC parameters. This includes reference to a Java package and setting the X-Cmd-Response header.
Exploitation techniques
Below is a running list of various exploitation techniques seen by GreyNoise researchers:
- 5% of our current sample includes ‘nslookup’ queries.
- Most of the websites requested use generated subdomain prefixes; these are the apex domains:

- Destructive attacks that include sudo rm -rf -no-preserve-root

- Attempts to download and remove custom scripts.
- Utilization of the Nashorn Java class recommended for exploration in the Rapid7 blog post.
- Potentially “undetectable” initial access indicators. Includes commands like math evaluation, setting special X-headers for the response (<span class="code-block" fs-test-element="rich-text">X-FOI-TEST</span>, <span class="code-block" fs-test-element="rich-text">X-Hax</span>, <span class="code-block" fs-test-element="rich-text">X-Vul=True</span>).
- Admin user creation attempts. Administrative users could be used for later access, but the current commands seen for this did not have any response vector set to indicate success.
- Under 1% of our current sample has Windows-related attempts. These attempts include PowerShell commands that download files that are no longer accessible, running cmd, dir commands.
- Lots of bash shells. These just include wgets and reverse shell attempts so far.
- Old friends: Mirai and Saru botnet additions. XMRig proliferation.
- Classic indicators of initial access orienteering - whoami, dir, cat, hostname, ls -l.
- Obfuscation techniques, such as putting the whole request in URL encoding:

- Base64 encoding generic commands
- A very creative <span class="code-block" fs-test-element="rich-text">[“cl"+"ass"].forName("jav"+"ax.sc"+"ript.S"+"criptEngineManager"</span>
- And naturally, people who have no idea what the hell they are doing.
Indicators of Compromise
The GreyNoise Trends tag, Atlassian Confluence Server CVE-2022-26134 OGNL Injection Attempt, provides a downloadable list of all the IP addresses observed attempting to mass exploit CVE-2022-26134 in the past 24 hours.
Mitigation Actions
- Patch
Atlassian has released patched versions of Confluence Server & Data Center and recommends upgrading to the latest Long Term Support release.
- Mitigation prior to patching
Until you can install the patched version of Confluence, there are several temporary mitigations you can apply:
- Update specific files for specific versions of the product - For organizations unable to upgrade Confluence immediately, then as a temporary workaround, you can mitigate the CVE-2022-26134 issue by updating a specific set of .jar files identified in Confluence Security Advisory 2022-06-02.
- Block mass exploit IP addresses - GreyNoise identifies a list of IP addresses attempting to exploit this Confluence vulnerability in the past 24 hours that you can block temporarily until you have had time to install a patched version. The IP addresses can be downloaded from GreyNoise Trends for Atlassian Confluence Server CVE-2022-26134 OGNL Injection Attempt in several formats, including JSON, CSV, TXT files, as well as dynamically updated URLs for use with Palo Alto Networks, Cisco, and Fortinet firewalls.
Note - Disabling anonymous access does not provide sufficient means to mitigate this vulnerability. link
Additional Information
- https://nvd.nist.gov/vuln/detail/CVE-2022-26134
- https://www.volexity.com/blog/2022/06/02/zero-day-exploitation-of-atlassian-confluence/
- https://www.rapid7.com/blog/post/2022/06/02/active-exploitation-of-confluence-cve-2022-26134/
- https://www.cisa.gov/uscert/ncas/current-activity/2022/06/03/atlassian-releases-new-versions-confluence-server-and-data-center


 Explore Our Data
Explore Our Data