In today’s cyber landscape, blending robust security with effective design is not just beneficial—it’s essential. At GreyNoise, we integrate design principles from the very beginning of our development process, ensuring that every security measure is user-focused and seamlessly integrated. This approach doesn't just enhance the security of digital services; it also ensures that updates and innovative controls fit perfectly within existing systems.
Empowering Users with User-Centric Design
Our philosophy at GreyNoise centers around understanding and addressing your needs, challenges, and feedback. By prioritizing user-centric design, we ensure that each feature and update is not just powerful, but also relatable and engaging.
Putting You First: Your needs, challenges, and feedback are what drive us at GreyNoise. We believe that understanding your perspective is key to making our cybersecurity solutions not just powerful, but also relatable and engaging.
Anticipating Security Needs: We proactively incorporate mechanisms like security logging, monitoring, alerting, and response capabilities into our systems, preparing for potential security incidents before they occur [1].
Join Our Community on Slack: Your insights are invaluable. Engage with us on Slack to share your experiences and suggestions, playing a pivotal role in our product iteration process. Join our Community on Slack.
Simplicity and Accessibility: The Hallmarks of GreyNoise Design
Our commitment to simplicity and accessibility ensures that our tools are straightforward and can be used by everyone. Here’s how we achieve this:
Clutter-Free Interface: Simplicity is central to GreyNoise’s design ethos. Our interfaces are streamlined, focusing on delivering essential information efficiently to prevent overload and facilitate quick, informed decisions.
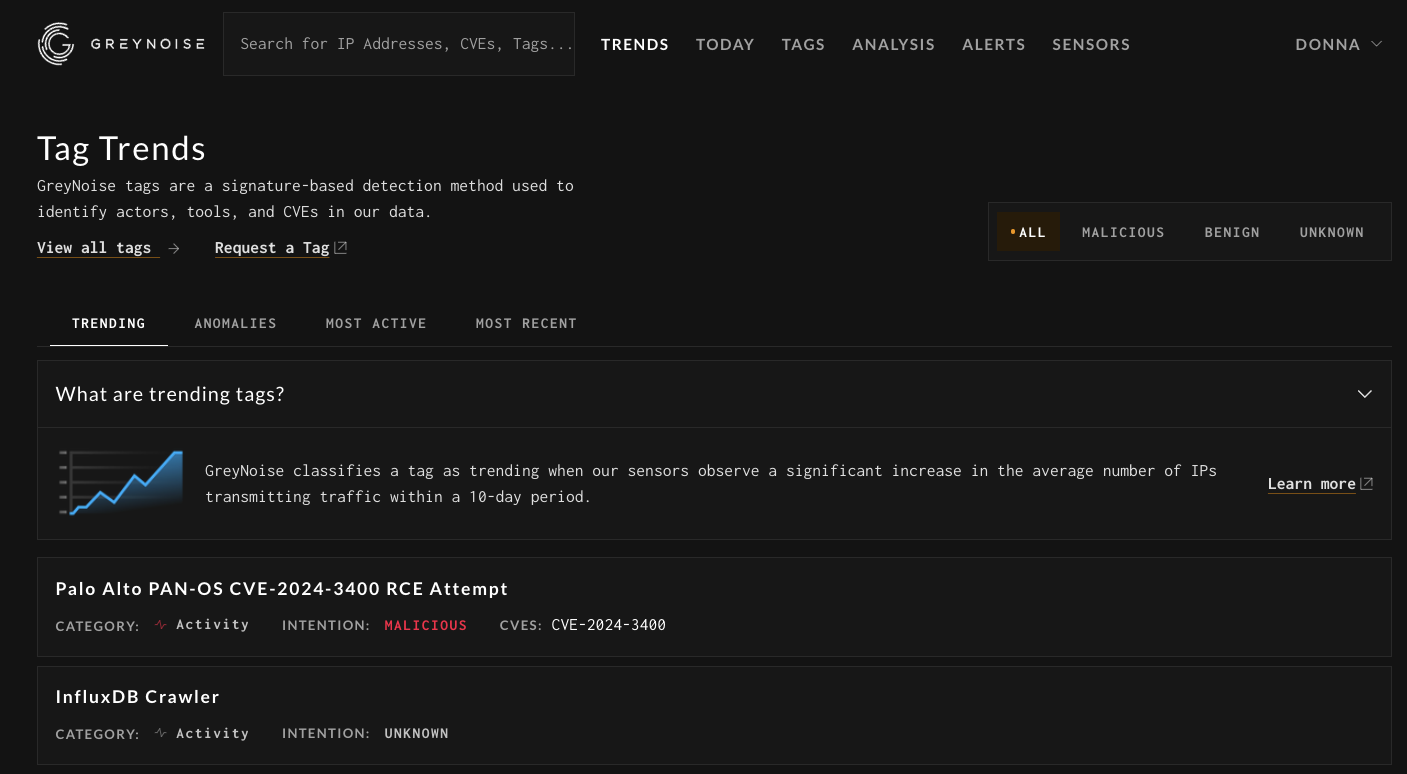
Focused Feature Set: We hone in on the most impactful features, ensuring our tools are straightforward and effective, making complex threat analysis accessible to all users.
Inclusive Design Philosophy: Upholding the principle that cybersecurity should be accessible to everyone, GreyNoise designs tools that cater to a wide range of abilities, embodying our inclusive design philosophy. Our proof of promise and commitment to accessibility is demonstrated through our Voluntary Product Accessibility Template (VPAT), which details how our products adhere to recognized accessibility standards. This transparency underscores our belief in making security tools accessible to everyone, affirming that effective security is a universal right.
Visual Engagement: Simplifying Complex Information
GreyNoise uses visual elements like infographics to break down complex information, making cybersecurity concepts more understandable and engaging, illustrating the practical benefits of our design-driven approach.

Real-World Applications and User Experiences
GreyNoise consistently demonstrates its commitment to enhancing user capabilities through various educational and interactive platforms. We offer comprehensive demos and case studies, which are pivotal for users looking to deepen their understanding of cybersecurity practices [2]. These resources are tailored to help both novice and advanced users by providing practical, real-world applications of GreyNoise's cybersecurity solutions.
Additionally, GreyNoise is proactive in addressing future cybersecurity concerns by hosting webinars, such as the recent discussion on the future of honeypots. These events aim to educate participants on strategies to combat targeted attacks, reflecting GreyNoise's dedication to keeping the cybersecurity community informed and prepared [3].
A Fusion of Cybersecurity and Design
At GreyNoise, we are redefining the synergy between security and design. Our dedication to user-centric, simple, and accessible design propels us to deliver tools that are not just powerful but also intuitive and inclusive. With GreyNoise, you are equipped with cybersecurity tools designed for the modern digital landscape, where effective security seamlessly integrates with exceptional user experience.
Key Innovations and Features
1. Explore and Investigate: Users can delve into detailed analyses of IP activities, enhancing their understanding and ability to react swiftly to potential threats [4].

2. IP Timeline and Details: Offers a comprehensive view of an IP's history and current status, allowing users to track and analyze behavior patterns over time [5].

3. Alerts and Blocklists: Enables proactive responses with customized alerting systems, ensuring users can respond to threats promptly [6].

At GreyNoise, we don’t just create tools; we build solutions that integrate effective security with exceptional user experience. Our commitment to user-centric, simple, and accessible design drives us to deliver products that not only protect but also empower our users.
Explore GreyNoise’s Design-Centric Cybersecurity Solutions
Dive deeper into how our design-centric cybersecurity solutions can transform your security strategy. Interact with our tools, join our community forum on Slack to share your insights and help shape the future of cybersecurity.
FAQs:
How does GreyNoise ensure its design is user-centric?
GreyNoise integrates user feedback throughout the design and development process, ensuring that our tools meet real user needs effectively and intuitively.
What are GreyNoise’s key design principles?
We focus on simplicity, user-centricity, and accessibility to ensure our cybersecurity tools are effective and easy to use for everyone.
How can I provide feedback on GreyNoise products?
Join our Slack community! It’s a vibrant space where you can provide direct feedback, suggest improvements, and influence our product development.
Reference:
- Secure by Design Principles
- GreyNoise Blog
- GreyNoise Resources
- GreyNoise Product Overview
- IP Timeline Feature
- Alerts and Blocklists


 Explore Our Data
Explore Our Data