Update: 25 August 2025
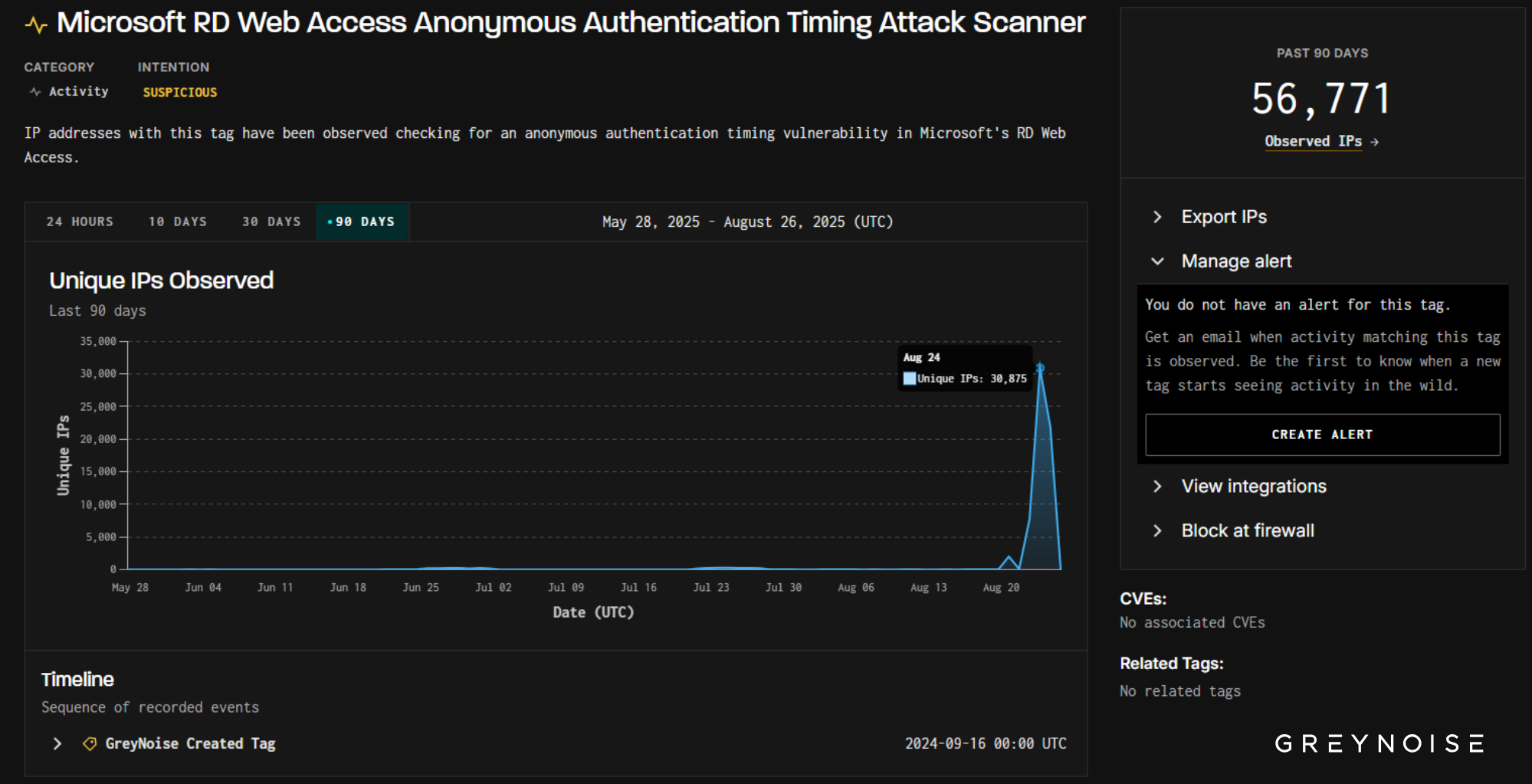
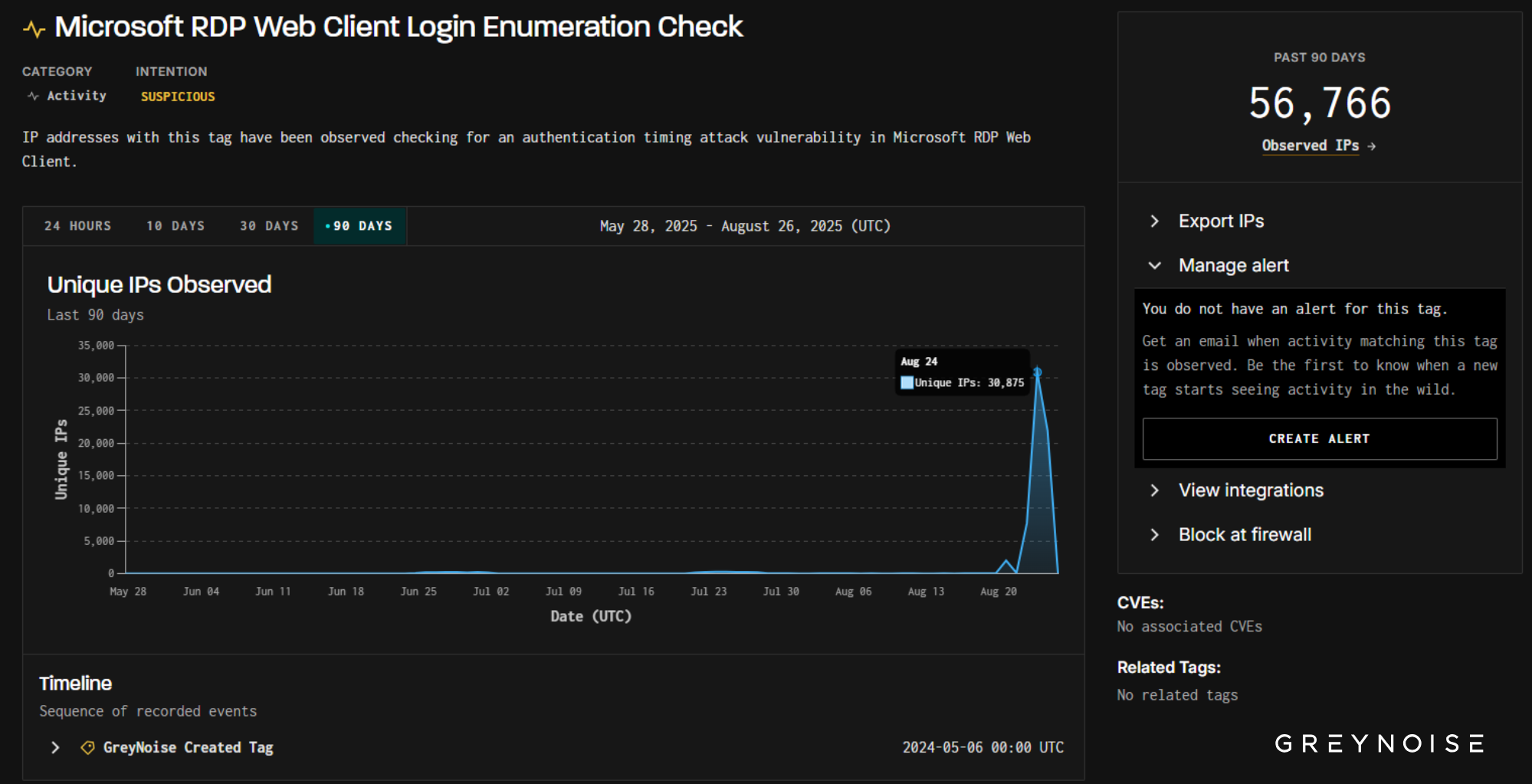
Hours after publishing this blog, GreyNoise identified a much larger wave: on August 24, over 30,000 unique IPs simultaneously triggered both Microsoft RD Web Access and Microsoft RDP Web Client tags, largely from the same client signature behind the August 21 spike we reported below.
A Sudden Surge in RDP Probing
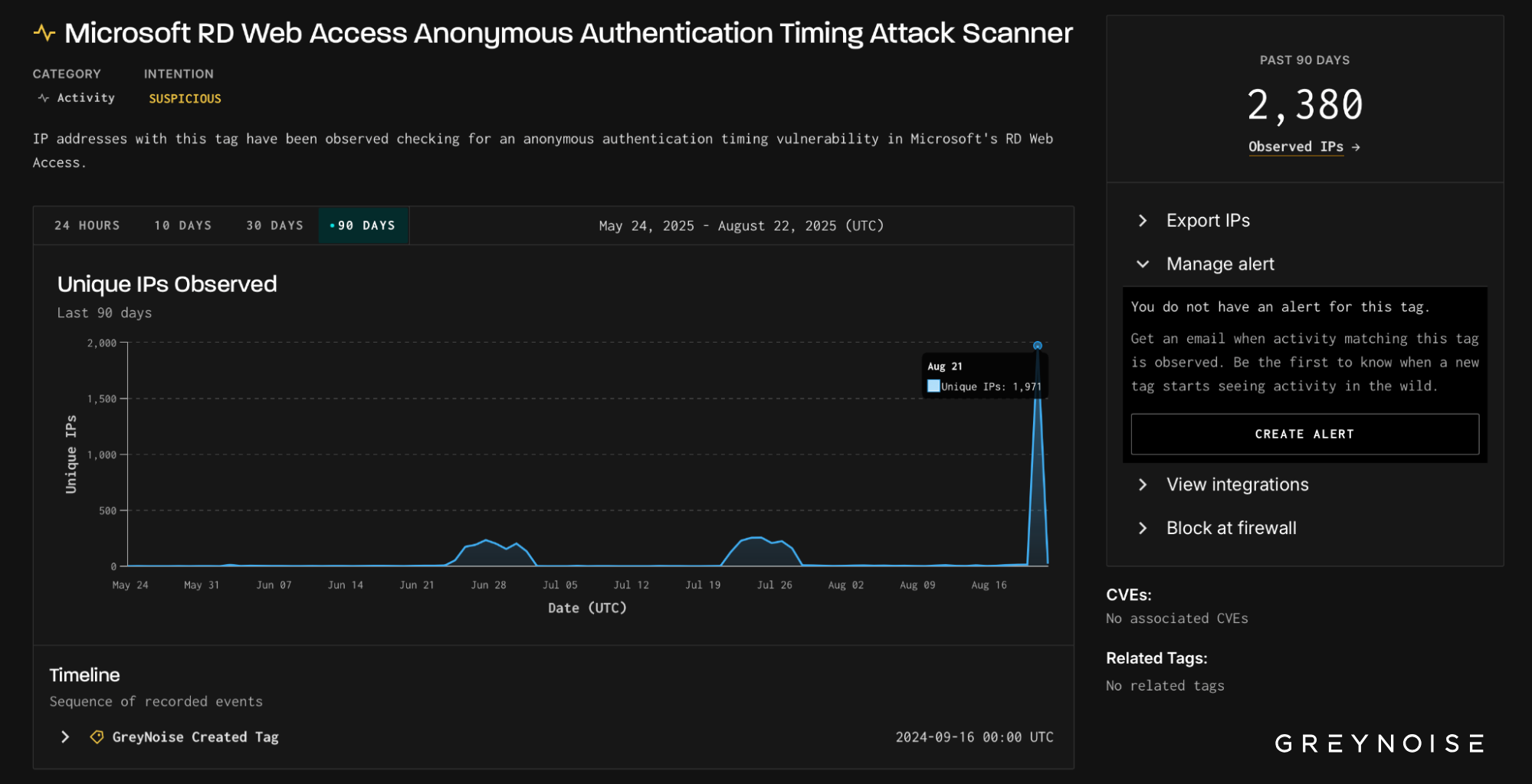
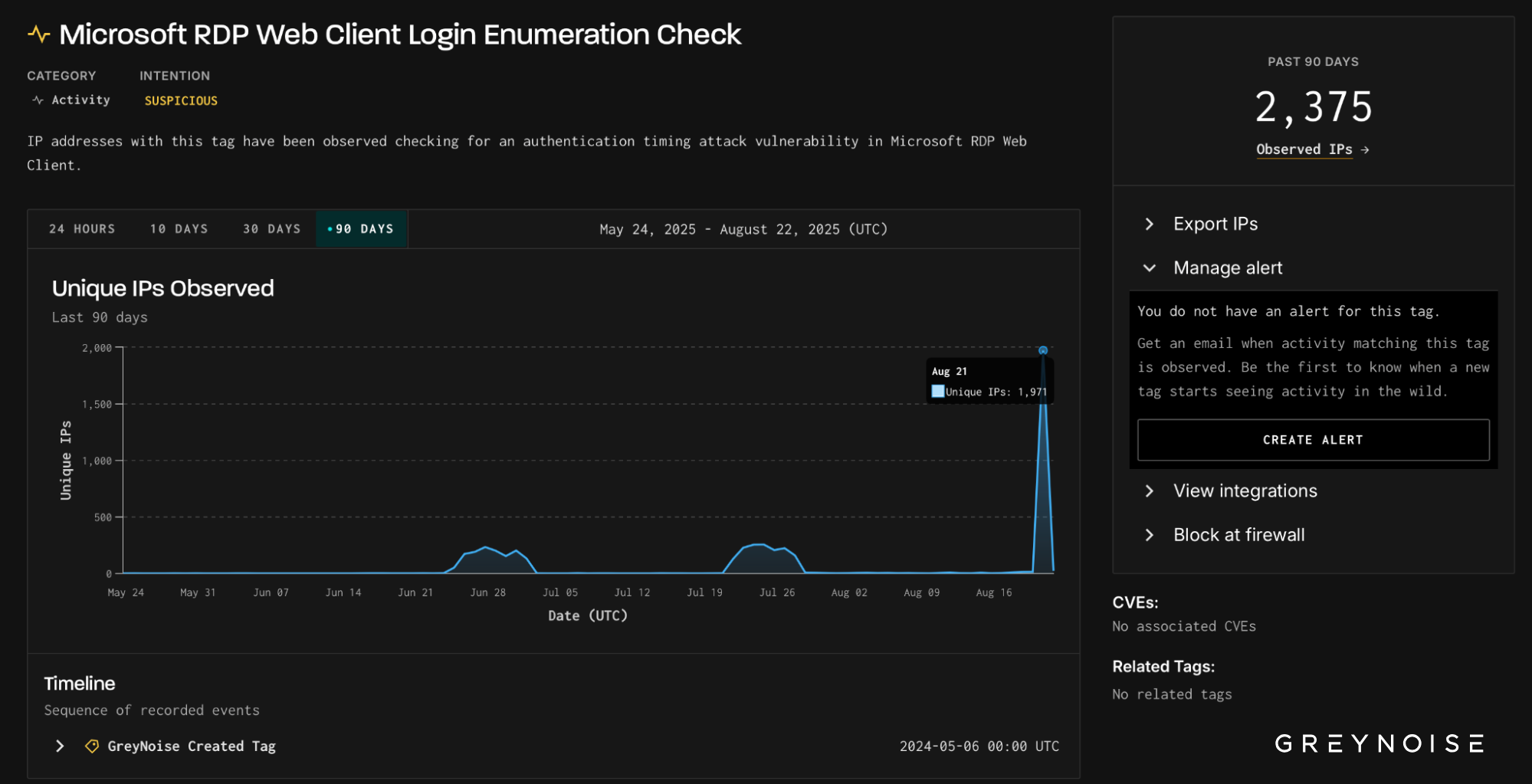
On August 21, GreyNoise observed a sharp surge in scanning against Microsoft Remote Desktop (RDP) services. Nearly 2,000 IPs — the vast majority previously observed and tagged as malicious — simultaneously probed both Microsoft RD Web Access and Microsoft RDP Web Client authentication portals. The wave’s aim was clear: test for timing flaws that reveal valid usernames, laying the groundwork for credential-based intrusions.
The Spike
- Normal baseline: ~ 3-5 IPs/day across these tags.
- August 21: 1,971 IPs — orders of magnitude above baseline.
- 100% overlap: every IP on one tag also appeared on the other.
- Timelines show the same client signature hitting both tags simultaneously.
- The client signature was first observed August 21 and has only engaged in activity targeting Microsoft RDP.
Microsoft RD Web Access
Microsoft RDP Web Client
What the Data Shows
- Uniform client signature: 1,851/1,971 IPs shared the same client signature, indicating a single toolset or botnet module.
- Malicious classifications: 1,698/1,851 (~ 92%) of those IPs are already tagged malicious in GreyNoise.
- Sources & Targets: Source countries skew heavily to Brazil (~ 73%); the United States was the only target country observed in this spike.
- Multi-pronged behavior: The same IPs were also flagged as Open Proxy Scanners and Web Crawlers, consistent with a multipurpose toolkit that includes carrying an HTTP referrer header.
Separately but potentially relevant, on August 22 GreyNoise observed a spike in scanning for open proxies. This heightened activity follows recent anomalies observed on July 31 and August 9 against GreyNoise’s Open Proxy Scanner tag. Early research indicates there is partial overlap in client signatures between this spike and the RDP scan detected on August 21.
Why Now? Back-to-School Exposure
The timing may not be accidental. August 21 sits squarely in the US back-to-school window, when universities and K-12 bring RDP-backed labs and remote access online and onboard thousands of new accounts. These environments often use predictable username formats (student IDs, firstname.lastname), making enumeration more effective. Combined with budget constraints and a priority on accessibility during enrollment, exposure could spike.
The campaign’s US-only targeting aligns with that calendar — education and IT teams should harden RDP now and watch for follow-up activity from this same client signature.
What’s Being Mapped
The RDP scanners were doing more than just touching login pages:
- Step 1: Finding endpoints — identifying IPs that expose RD Web Access or RDP Web Client.
- Step 2: Testing for flaws — checking if authentication workflows leak information via timing (or other login-flow differences) that lets an attacker infer valid usernames.
This is enumeration: confirming accounts on exposed systems so later credential stuffing, password spraying, or brute force has a much higher chance of success.
Why It Matters
A large, uniform, maliciously-classified scanner set is actively mapping Microsoft RDP authentication surfaces for account discovery weaknesses. Even without immediate exploitation, the output of this campaign (which endpoints exist, which accounts likely exist) is directly reusable for:
- Credential stuffing (pairing confirmed usernames with breached passwords)
- Password spraying/brute force (now guided by a valid-user list)
- Future exploitation (attacker already has target map if an RDP-related CVE emerges)
Recent research found spikes in attacker activity against a given technology tend to precede new vulnerabilities in that technology. In 80 percent of cases, a new vulnerability emerged within six weeks of a spike.
Related Real-World Precedent
RDP has been leveraged by threat actors in the past to conduct espionage, deploy ransomware, and run global exploit campaigns:
- Espionage — Russia-nexus actor abusing RDP features for data theft: Google Threat Analysis Group (TAG) reported a suspected Russia-nexus espionage actor (UNC5839) abusing lesser-known RDP capabilities to read victim drives and exfiltrate files during targeted intrusions. Different from timing/enumeration, but shows RDP used directly in espionage tradecraft. The incident mainly targeted European militaries and governments.
- Ransomware — SamSam’s RDP initial access: U.S. CISA/FBI’s SamSam advisory documents actors using RDP for persistent access, typically via brute force or stolen credentials, before deploying ransomware (e.g., City of Atlanta).
- Global exploitation event — BlueKeep (CVE-2019-0708): In 2019, a critical flaw in Windows Remote Desktop Services — the service behind RDP — was broadly scanned and then exploited in the wild (e.g., cryptominer campaigns). It’s a clear example of RDP-exposed systems moving from recon to mass exploitation once a workable flaw appears.
GreyNoise will continue monitoring the situation and update this blog as necessary.
Please contact your GreyNoise support team if you are interested in the JA4+ signatures in this investigation.
GreyNoise has developed an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats. Click here to learn more about GreyNoise Block.
— — —
Stone is Head of Content at GreyNoise Intelligence, where he leads strategic content initiatives that illuminate the complexities of internet noise and threat intelligence. In past roles, he led partnered research initiatives with Google and the U.S. Department of Homeland Security. With a background in finance, technology, and engagement with the United Nations on global topics, Stone brings a multidimensional perspective to cybersecurity. He is also affiliated with the Council on Foreign Relations.










.png)
.png)