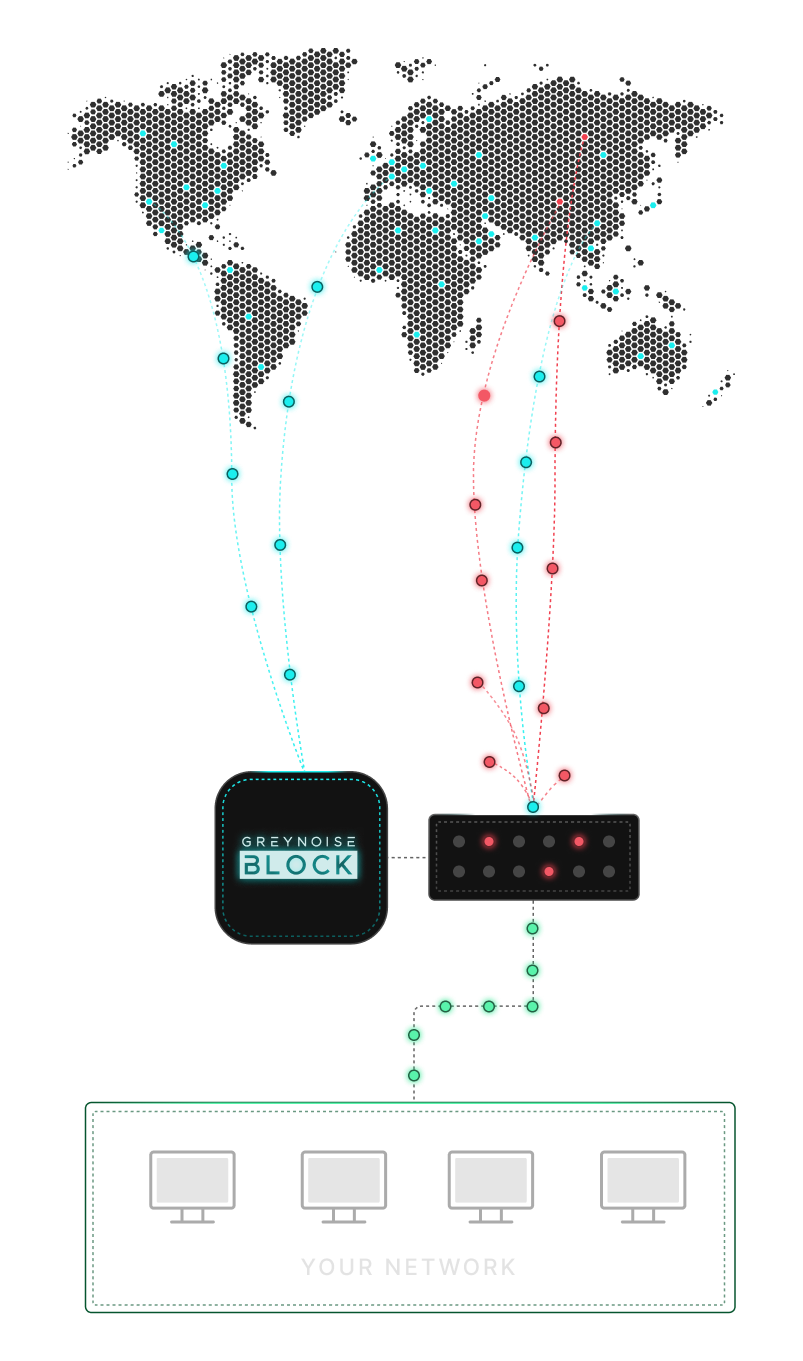
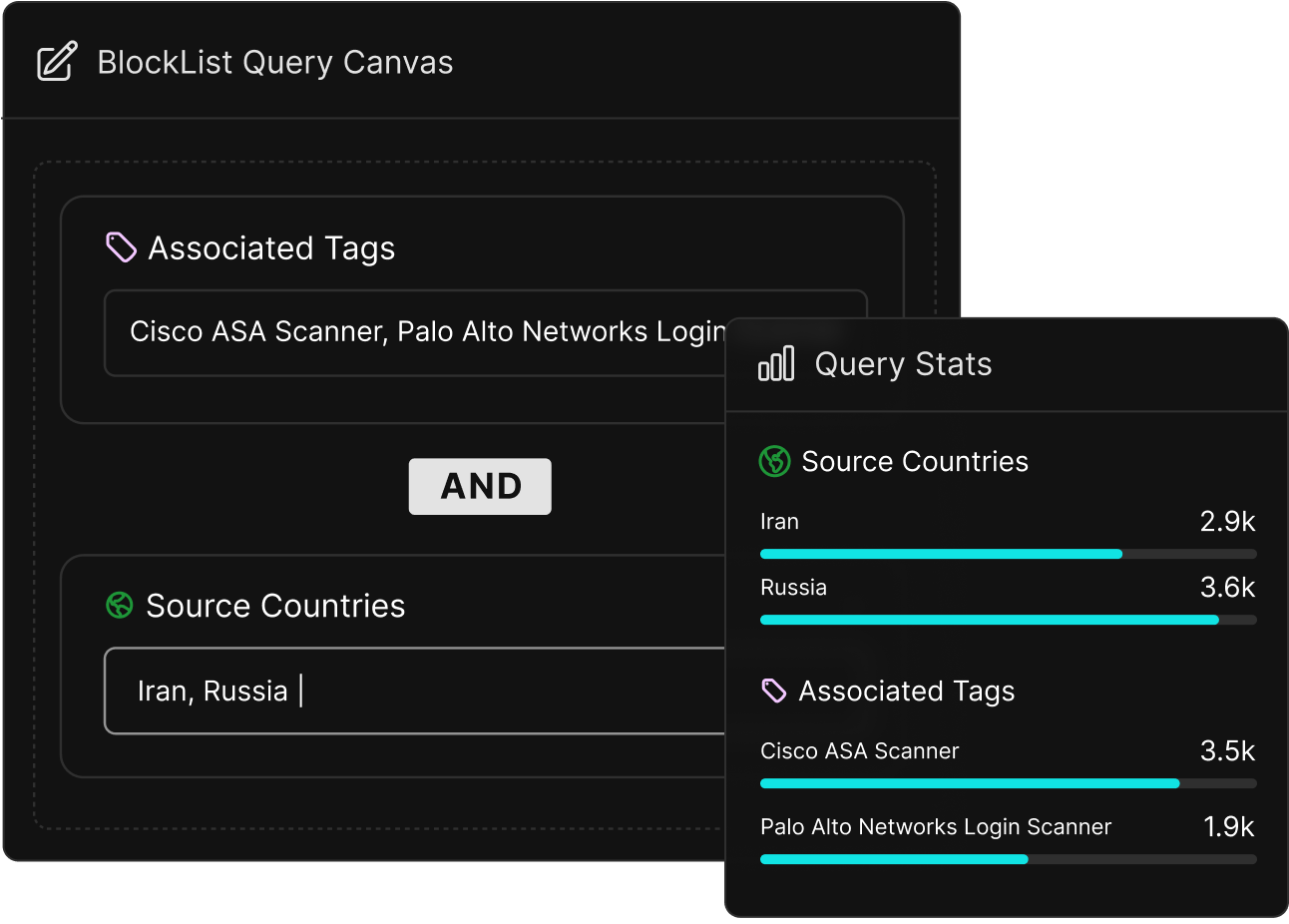
Lower Risk of Overblocking
Real-time lists built from observed attack traffic, not stale third-party feeds. Tune aggressiveness by how recently malicious activity was seen.
Buy Time for Remediation
Cut off hostile IPs and CVE exploits before they spread, giving you critical time for longer-term fixes
Reduce Alert Noise
Block mass scanning and exploitation attempts to shrink SIEM logs, cut storage costs, and ease analyst workload
Keep Pace with Emerging Threats
Blocklists update in real time as new attacker infrastructure appears, staying effective against fast-moving campaigns.