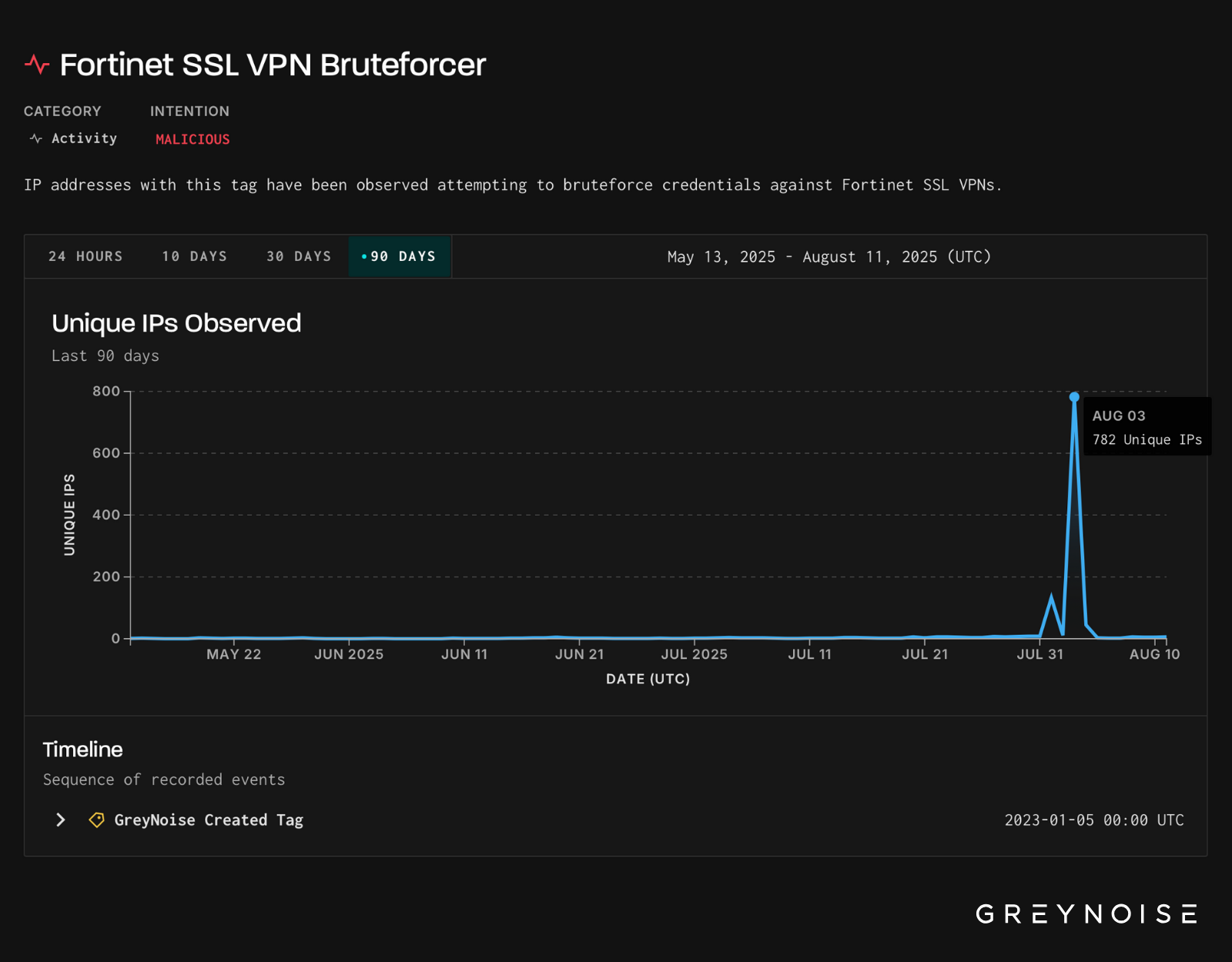
On August 3, GreyNoise observed a significant spike in brute-force traffic targeting Fortinet SSL VPNs. Over 780 unique IPs triggered our Fortinet SSL VPN Bruteforcer tag in a single day — the highest single-day volume we’ve seen on this tag in recent months.
New research shows spikes like this often precede the disclosure of new vulnerabilities affecting the same vendor — most within six weeks. In fact, GreyNoise found that spikes in activity triggering this exact tag are significantly correlated with future disclosed vulnerabilities in Fortinet products. The below chart shows spikes in activity against Fortinet tags (white dots) and CVE disclosures affecting Fortinet products (red dots):
.png)
Critically, the observed traffic was also targeting our FortiOS profile, suggesting deliberate and precise targeting of Fortinet’s SSL VPNs. This was not opportunistic — it was focused activity.
The top target countries in the past 90 days are Hong Kong and Brazil.
A Tale of Two Brute Force Waves Against Fortinet
When we reviewed a two week window of traffic matching the Fortinet SSL VPN Bruteforcer tag, two distinct waves emerged:
- Wave One: A long-running set of brute-force activity tied to a single TCP signature that remained relatively steady over time.
- Wave Two: A sudden and concentrated burst of traffic beginning August 5. This second wave had a completely different TCP signature and stood out due to its abrupt onset.
This made the decision easy: we pivoted to the second wave to learn more.
A Shift in Targeting: From VPN to FortiManager
Once the TCP signature for the second wave was isolated, we paired it with an observed client signature seen in sessions during the same timeframe.
What we found was surprising.
While the August 3 traffic has targeted the FortiOS profile, traffic fingerprinted with TCP and client signatures — a meta signature — from August 5 onward was not hitting FortiOS. Instead, it was consistently targeting our FortiManager - FGFM profile albeit still triggering our Fortinet SSL VPN Bruteforcer tag.
This indicated a shift in attacker behavior — potentially the same infrastructure or toolset pivoting to a new Fortinet-facing service.
IPs associated with the meta signature:
31.206.51.194
23.120.100.230
96.67.212.83
104.129.137.162
118.97.151.34
180.254.147.16
20.207.197.237
180.254.155.227
185.77.225.174
45.227.254.113
A Residential Clue
One additional lead emerged during the investigation.
When reviewing historical data tied to the same post-August 5 TCP fingerprint, we found an earlier spike in June with a unique client signature that resolved to an IP — a FortiGate device — in a residential ISP block (Pilot Fiber Inc.). This may indicate that the brute-force tooling was initially tested or launched from a home network — or it could reflect use of a residential proxy. A quick search of the device revealed:
- Not detected as a residential proxy or host of VPN services by Spur.us.
- Recent detections by AbuseDB.
- Not seen on Virustotal.
Notably, traffic tied to that same client signature in June was later seen paired with the same TCP signature associated with the longer-running brute-force cluster (Wave One) mentioned earlier. This overlap doesn’t confirm attribution, but it suggests possible reuse of tooling or network environments. Simply put, this side quest led us back to the original traffic associated with the August 3 spike.
Key Takeaways
- Brute-force attacks against Fortinet SSL VPN continue, and they appear to evolve over time.
- GreyNoise uncovered a behavioral shift, with traffic moving from FortiOS targeting to FGFM targeting just days after the August 3 spike.
- JA4+ based signatures reveal clustering, connecting recent waves to prior traffic — and even a potential residential origin.
- GreyNoise research has shown that spikes in attacker activity often precede new vulnerabilities affecting the same vendor — with 80 percent of observed cases followed by a CVE disclosure within six weeks.
Defender Recommendations
Use GreyNoise to:
- Search for this traffic using our Fortinet SSL VPN Bruteforcer tag.
- Block malicious IPs using our dynamic IP blocklist for this tag.
Please contact your GreyNoise support team if you are interested in the JA4+ signatures in this investigation.
GreyNoise will continue monitoring the situation and provide updates as necessary.
GreyNoise is developing an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats. Click here to learn more or get on the waitlist.
— — —
This research and discovery was a collaborative effort between Towne Besel and Noah Stone.










.png)
.png)