For executive audiences, please see the accompanying Situation Report (SITREP) for this activity.
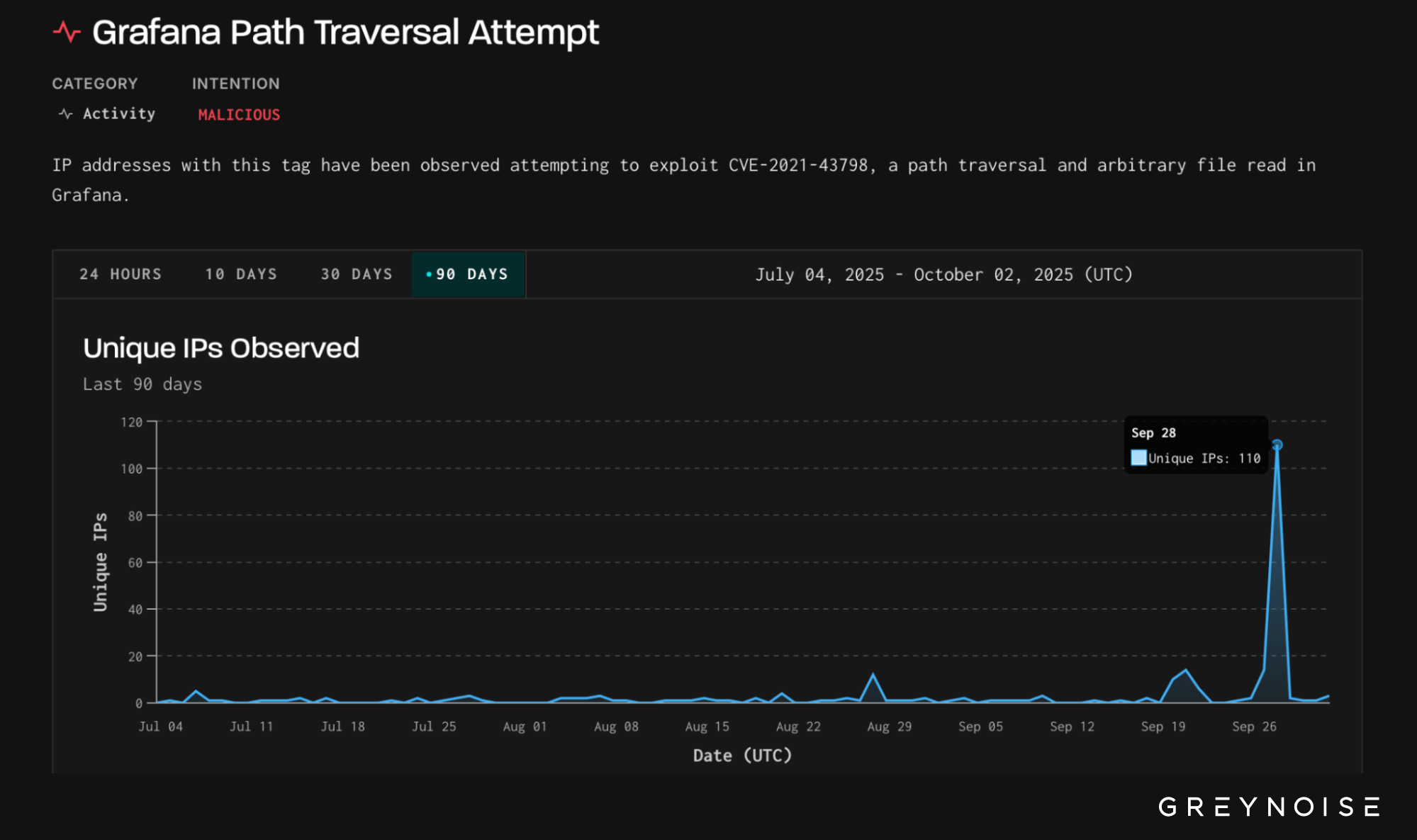
On 28 September 2025, GreyNoise observed a sharp one-day surge of exploitation attempts targeting CVE-2021-43798 — a Grafana path traversal vulnerability that enables arbitrary file reads. Over the course of the day, 110 unique IPs attempted exploitation against GreyNoise’s Global Observation Grid (GOG). All 110 IPs are classified as malicious.
The Spike
Grafana exploitation had been largely quiet in recent months. On 28 September, activity spiked sharply:
- 110 unique IPs observed in a single day.
- Destinations targeted: United States, Slovakia, and Taiwan — the only three destinations observed.
- Top three source countries: Bangladesh (107 IPs), China (2 IPs), Germany (1 IP).
- Of the Bangladesh-based IPs, 105 of 107 targeted U.S. endpoints.
- The majority of IPs were first seen on 28 September, the same day they attempted exploitation.
Patterns in the Activity
Two elements stand out in the data:
- Consistent targeting across sources. All traffic followed a distinct destination pattern, targeting each country following a roughly 3:1:1 ratio (U.S.: Slovakia: Taiwan). Similar patterns in traffic ratios emerged when narrowing this view to the top three source countries:
- China-based IPs → U.S. (7), Slovakia (2), Taiwan (2)
- Germany-based IPs → U.S. (3), Slovakia (1), Taiwan (1)
- Bangladesh-based IPs → U.S. (100), Slovakia (1), Taiwan (1)
- Convergence across tooling. The top TCP fingerprints observed that day also mapped to the same three destinations. Looking back further at activity against this tag, GreyNoise has identified at least two distinct HTTP fingerprints as well, further indicating multiple tools being applied against a common target set.
The alignment across both geography and tooling suggests shared tasking or a common target list, not uncoordinated traffic.
Notable Infrastructure
Two IPs geolocated to China are worth highlighting:
- 60.186.152.35
- 122.231.163.197
Both belong to CHINANET-BACKBONE, were first observed on 28 September, active only that day, and overwhelmingly focused on Grafana.
Threat Context
Exploitation of older, high-impact vulnerabilities like CVE-2021-43798 is common across different threat categories:
- Global Exploitation: Grafana path traversal and related vulnerabilities have been leveraged in large-scale SSRF / exploit waves targeting many IPs and software ecosystems.
- Vulnerability Reuse & Toolkits: Grafana flaws (e.g., CVE-2025-6023) are being actively researched and weaponized for account takeovers and integrated into attacker tool sets.
- Exploit Chains & Reconnaissance: In advisories and analyses, Grafana vulnerabilities show up in reconnaissance stages of multi-step exploit chains (such as SSRF campaigns).
Assessment
This activity reflects a coordinated push against a known, older vulnerability. The uniform targeting pattern across source countries and tooling indicates common tasking or shared exploit use. GreyNoise does not attribute this to a specific threat actor, but the convergence suggests either one operator leveraging diverse infrastructure or multiple operators reusing the same exploit kit and target set.
We anticipate old vulnerabilities — like CVE-2021-43798, and even older ones — will continue resurging in the future. Read GreyNoise’s research from earlier this year to learn more about the patterns and behaviors resurgent vulnerabilities tend to exhibit, and how defenders can stay ahead.
Defender Recommendations
- Block the 110 malicious IPs observed on 28 September.
- Confirm Grafana instances are patched against CVE-2021-43798.
- Review logs for evidence of traversal requests and ensure no sensitive files were returned.
Please contact your GreyNoise support team if you are interested in the JA4+ signatures in this investigation.
GreyNoise has developed an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats. Click here to learn more about GreyNoise Block.
— — —
This research and discovery was a collaborative effort between Glenn Thorpe, Noah Stone, Towne Besel, and boB Rudis.







.png)


.png)
.png)