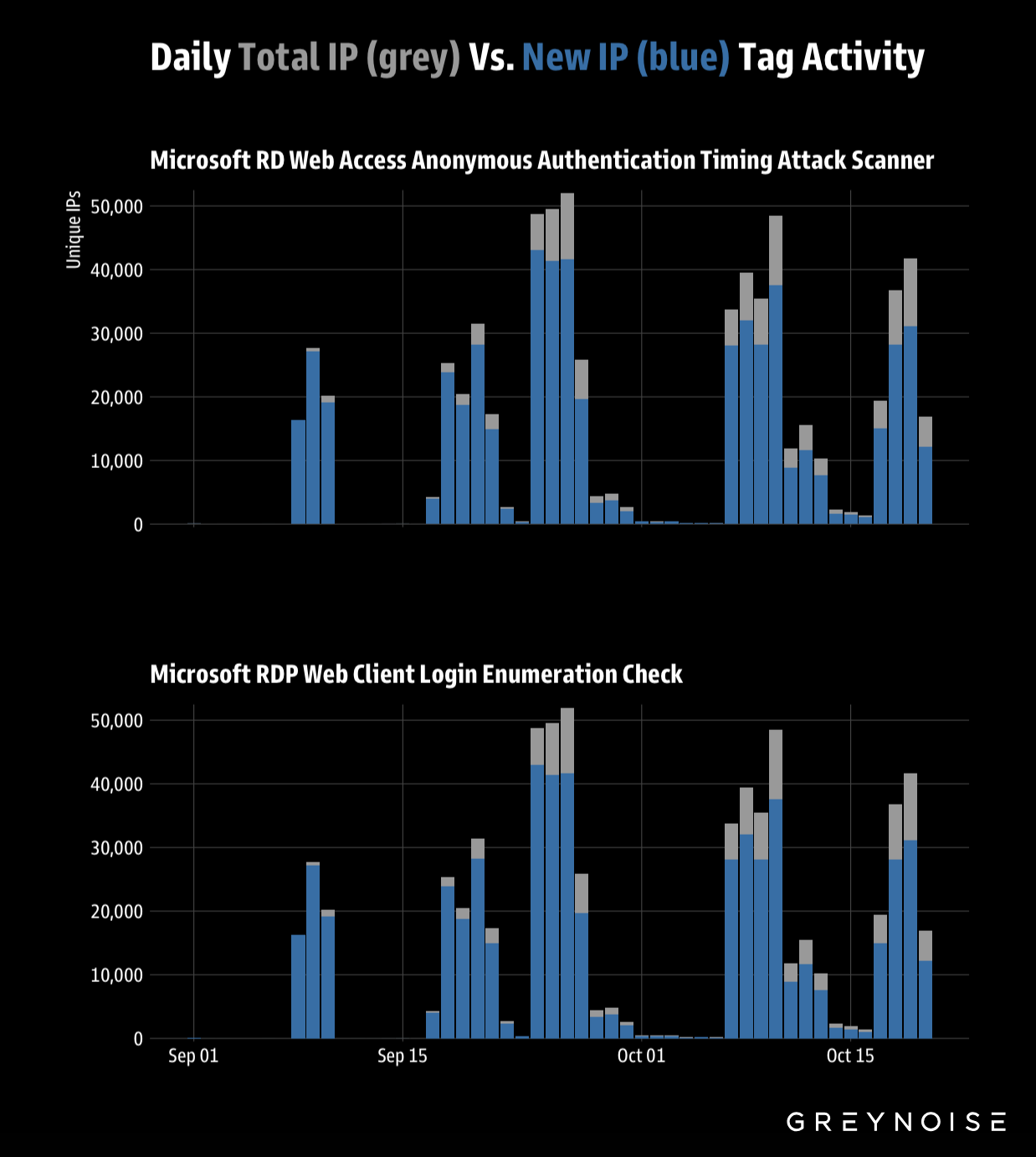
GreyNoise has observed steady deployments of previously unseen IPs attacking Microsoft RDP services through timing-based vulnerabilities. Attackers are rotating significant volumes of new IPs each day to target two primary vectors — RD Web Access timing attacks and RDP web client login enumeration — likely in an effort to evade detection and blocking.
Use GreyNoise Block to dynamically block all IPs engaged in this activity. On 10 October, GreyNoise partially linked this activity to a global botnet, publishing a blocking template named “Oct-2025 RDP Botnet Campaign.” Applying this template instantly neutralizes the threat actors’ IP rotation strategy.
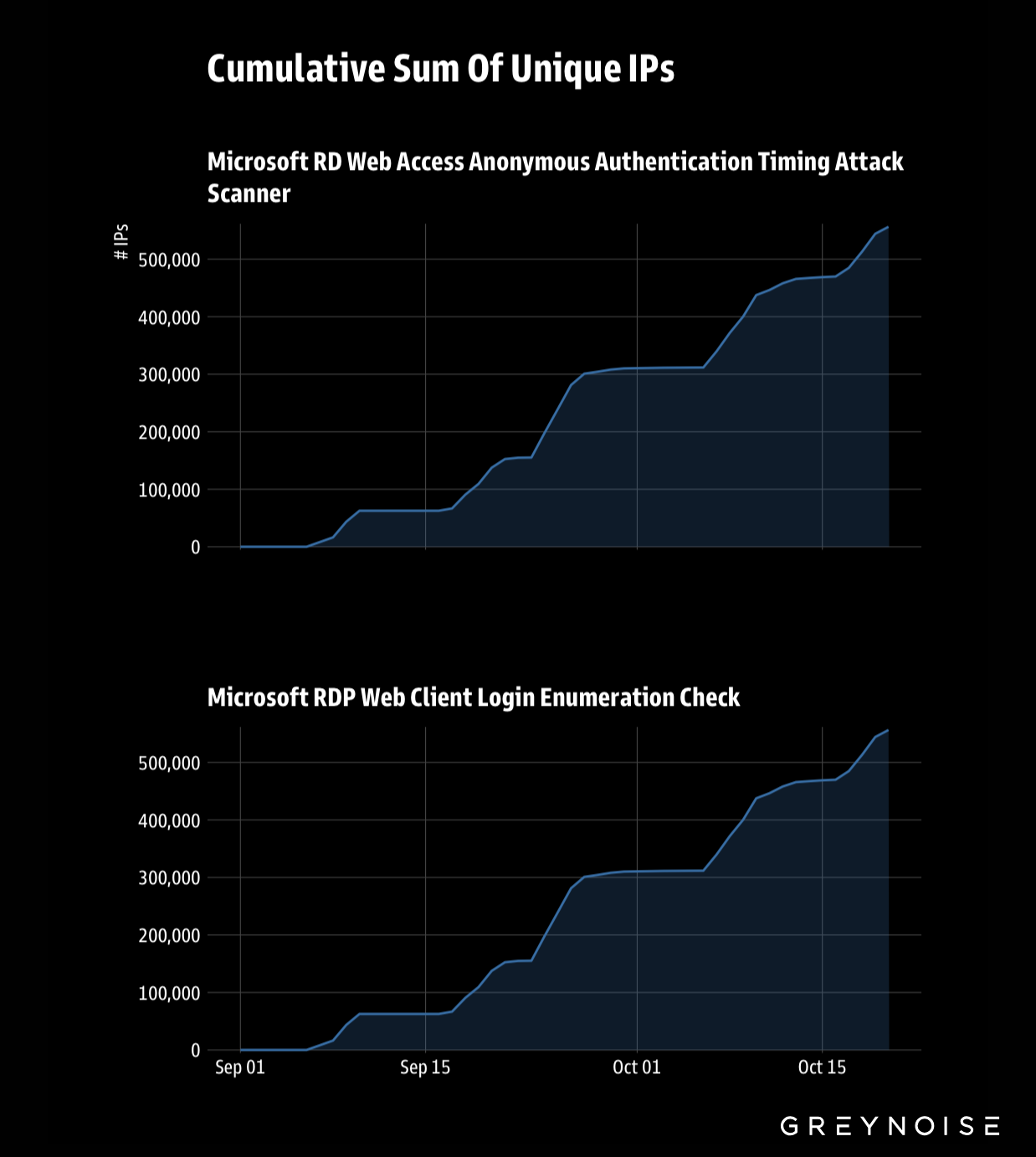
From September 2025 to present, we’ve observed a steady rise in the number of unique IPs targeting RDP — now exceeding 500,000.
Geographic Distribution
The top three source countries in the past 90 days are:
- Brazil (63%)
- Argentina (14%)
- Mexico (3%)
Nearly 100 percent of targeting has been directed at U.S.-based systems. Source and target patterns remain consistent with the botnet activity first identified on 10 October.
IP Turnover Increases Risk
The rapid churn of new IPs underscores an emerging trend: threat actors are increasingly rotating infrastructure to evade static blocking and complicate attribution.
Use GreyNoise Block to dynamically block all IPs engaged in this activity. The “Oct-2025 RDP Botnet Campaign” template remains the most effective method for mitigation. Get started with a free 14-day trial.
GreyNoise will continue to monitor the situation and update this post as necessary.
— — —
This discovery was led by boB Rudis.











.png)