We built something new at GreyNoise Labs, and it started with a question we kept hearing: “How do I know if my home network has been compromised?”
It’s not a theoretical concern. Over the past year, residential proxy networks have exploded and have been turning home internet connections into exit points for other people’s traffic. Sometimes folks knowingly install software that does this in exchange for a few dollars. More often, malware sneaks onto devices, usually via nefarious apps or browser extensions, and quietly turns them into nodes in someone else’s infrastructure.
We’re also seeing the usual seasonal spike in compromised home routers, IoT, and other "edge" devices. These compromises often fly under the radar. Your internet works fine, your streaming doesn’t buffer, but somewhere in the background, your router is participating in vulnerability scans or brute-force attacks against servers around the world. You’re not the target—you’re the weapon.
So we built GreyNoise IP Check. Visit the site from any internet connection and within seconds you’ll know if that IP address has been caught scanning the internet or appears in our database of known business services. No signup required, no email collection—just a straightforward answer about what your IP address has been up to.
What You’ll Actually See
The tool gives you one of a few possible verdicts. The best outcome is clean—your IP hasn’t been observed scanning the internet and doesn’t belong to any known service infrastructure. Most residential connections fall into this category, which is exactly what you want.
If your IP shows up as malicious or suspicious, that’s your cue to investigate. Something on your network is behaving badly. It might be malware on a laptop, a compromised smart TV, or a router that’s been conscripted into a botnet. The tool will show you when the activity was first and last observed, what kinds of scanning behavior were detected, and point you toward next steps.
There’s also a middle category for IPs that appear in our Common Business Services dataset. If you’re on a VPN, corporate network, or cloud provider, that’s normal. The tool knows the difference between “this IP belongs to a data center” and “this IP is your grandmother’s cable modem doing port scans.”
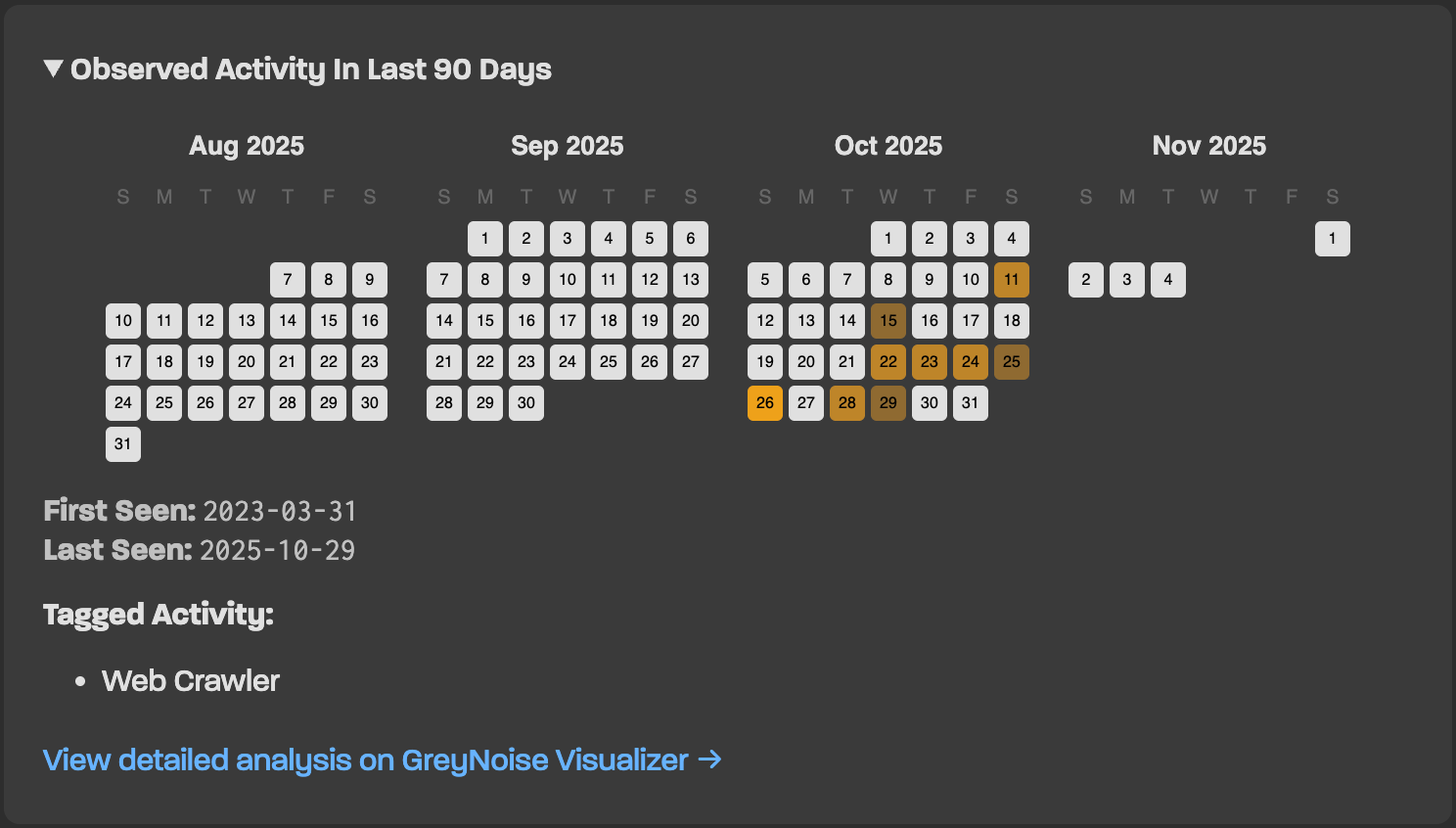
For those who want more detail, the results page includes a 90-day activity timeline showing when scanning behavior occurred and what tags GreyNoise assigned to it. You can see whether your IP was probing for vulnerable web services or attempting SSH connections. It’ll even show if it was hunting for exposed databases.
The Holiday Tech Support Opportunity
Here’s where this gets practical beyond your own network. If you’re the family tech person—and let’s be honest, if you’re reading this, you probably are—this tool fits perfectly in your holiday troubleshooting toolkit.
When you’re home for the holidays or visiting relatives over winter break, take thirty seconds to pull up the IP check on their network. It’s less invasive than asking to look at their devices and gives you an instant read on whether their home network has a problem. If it comes back clean, great. If it doesn’t, you have a specific starting point for helping them secure things.
The conversation shifts from vague “I think you might have a virus” territory to concrete “your network is showing up in our sensor data as scanning for vulnerable routers, so let’s check your devices and update your router firmware.” People understand that much better—and you’re not just the relative who always thinks their computer is infected.
For the More Technical Among Us
If you’re managing infrastructure or dealing with devices that connect to different networks regularly, there’s a programmatic option. You can query the service via curl to get JSON responses:
curl -s https://check.labs.greynoise.io/
This returns structured data about the IP making the request, including whether it appears in our scanning database, its classification if found, trust level for business services, and geographic metadata. You could incorporate this into MDM systems, VPN connection scripts, or network onboarding flows. You can use any programming language, just ensure there's a curl-esque user agent.
Imagine a laptop that checks its network reputation when connecting to a new WiFi. If it finds itself on a compromised or suspicious network, it could automatically force VPN usage, ensure the local firewall is active, or alert the user. For organizations with remote workers bouncing between coffee shops, airports, and client offices, knowing the reputation of each network adds an extra layer of confidence.
The API endpoint requires no authentication and has no rate limiting for reasonable use. We built it to be useful, not locked down behind enterprise pricing tiers.
Why This Matters Now
The scale of residential IP abuse has changed dramatically. What used to be primarily compromised home routers has expanded into a full ecosystem of residential proxy services, IoT botnets, and supply chain compromises in consumer networking gear. Our sensors see millions of residential IPs participating in scanning activity every month—and most of those users have no idea it’s happening.
The challenge with residential IP compromise is that it’s invisible to the people affected. Unlike a loud ransomware attack, a compromised router doesn’t announce itself. The internet keeps working. Netflix still streams. Email still arrives. But your IP address is building a reputation, potentially ending up on blocklists or triggering security alerts when you try to access certain services.
GreyNoise sees this activity because we maintain a global sensor network specifically designed to observe internet background radiation—the scans, probes, and reconnaissance that constantly sweep across every public IP address. We’ve collected data on billions of IPs over the years, cataloging what they scan for, how they behave, and whether they’re real threats or just noise.
This tool takes that visibility and makes it accessible to anyone. You don’t need to be a security analyst or pay for threat intelligence. You just need to wonder whether your home network is okay.
Check your IP address. Check your parents’ network when you visit. Check the coffee shop WiFi if you’re curious. It takes just a few seconds and could save you from a hidden mess. And if it comes back clean, hey—one less thing to worry about.
Visit check.labs.greynoise.io to see what your IP has been up to.







.png)


