Detect Compromised Assets
Detect outbound traffic probing GreyNoise sensors or talking with malicious IPs
Overview
Today's threat actors use botnets to scan for vulnerable systems and launch mass, automated attacks. To do this, compromising edge systems are critical to their operations.
Compromised devices often behave like attacker infrastructure, making it likely that a compromised device will probe the GreyNoise sensor network or interact with a known malicious IP.
GreyNoise can help you quickly spot if you have a compromised host on your network edge.
How GreyNoise Helps You
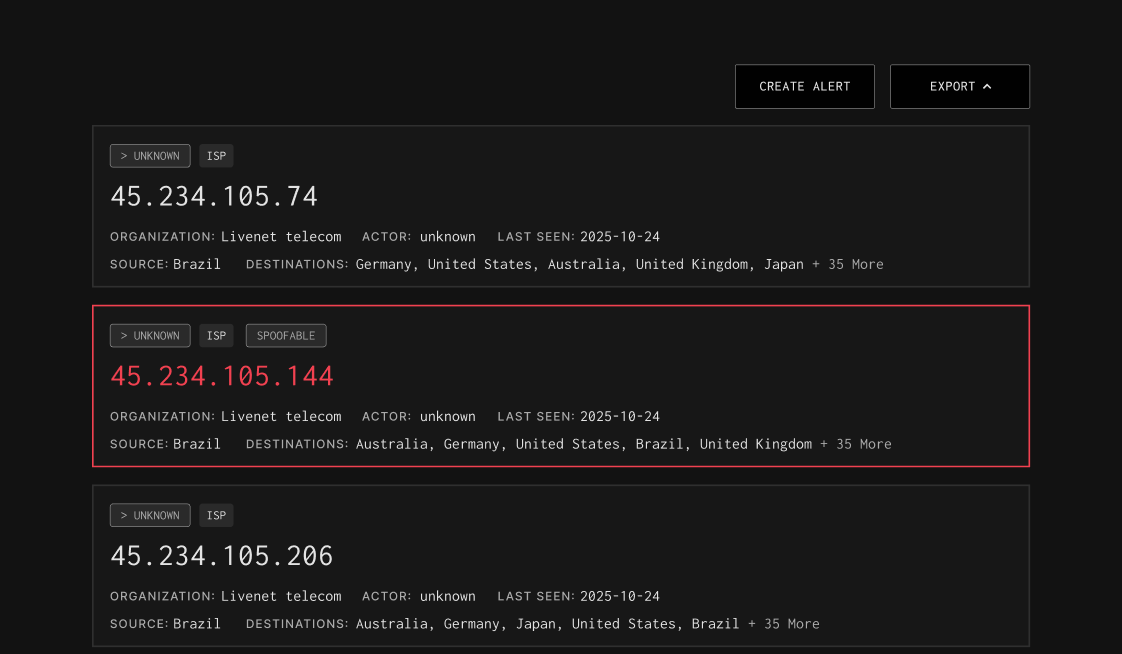
Find Your Compromised Assets
Identify Abnormal Outbound Traffic
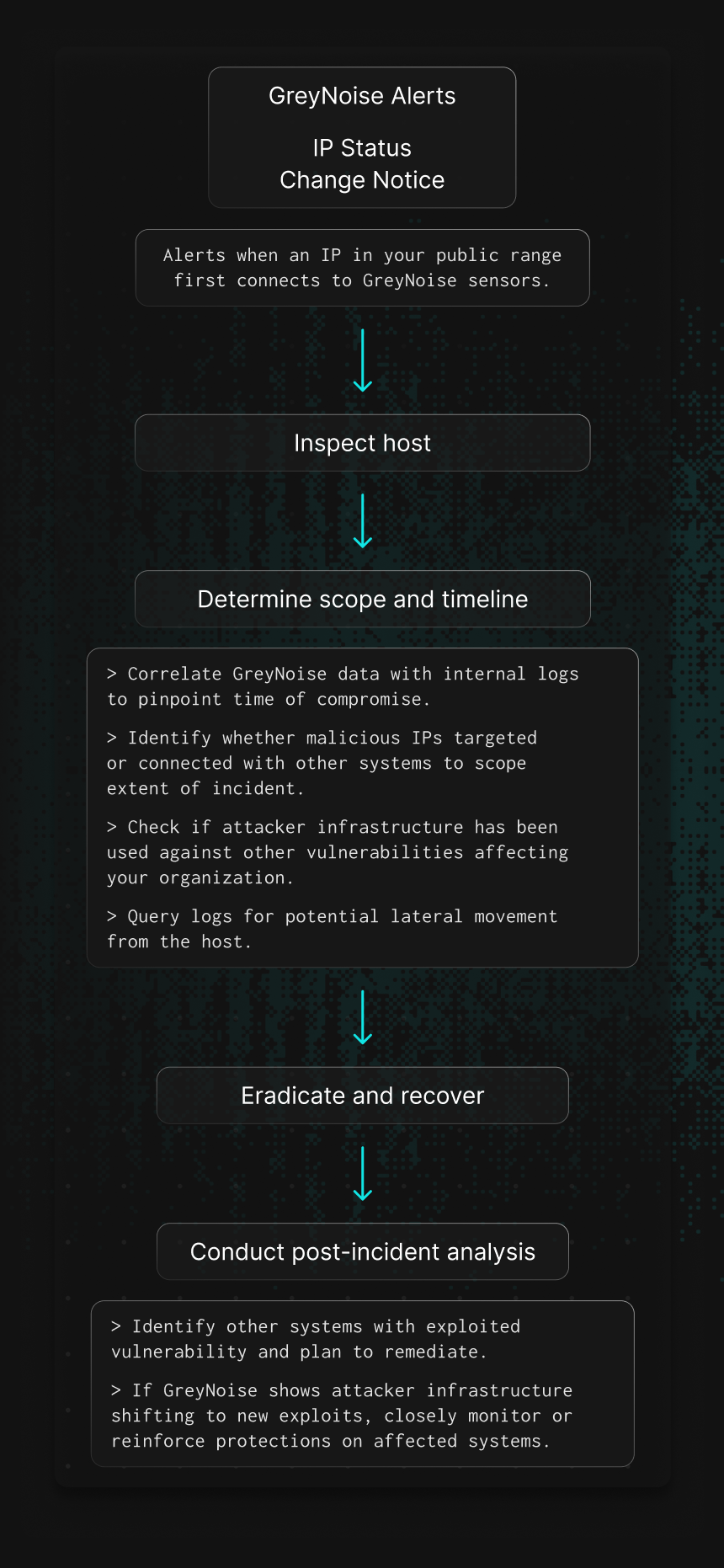
GreyNoise detects when your internal system contacts our global sensor network or is talking with a known malicious IP, both are strong indicators of compromise.
Faster Containment
Early visibility into compromised assets allows defenders to contain hosts, halting lateral movement.
Strengthen Incident Investigations
GreyNoise helps to establish a timeline of when a compromised device began scanning and exploitation.
Stop Outbound Connections to Malicious IPs
GreyNoise provides query-based, dynamic blocklists that prevent devices on your network from outbound communications with malicious IP addresses.
How it Works