Early Warning of Upcoming CVE Disclosures
Get ahead of new CVEs on the systems you care about.
Overview
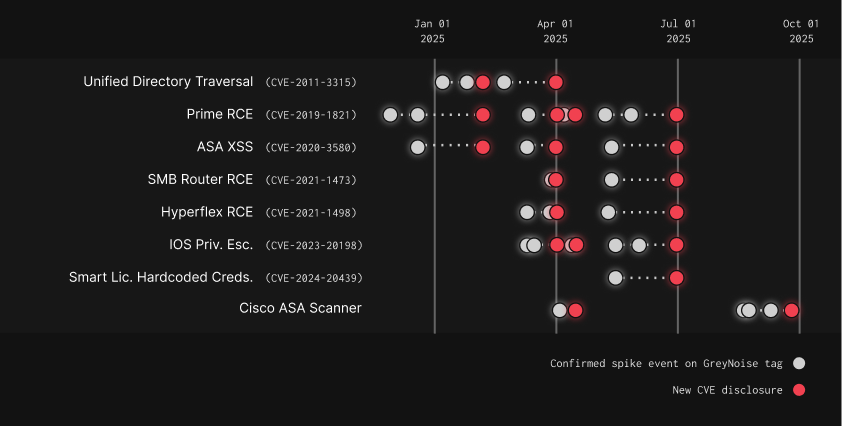
GreyNoise research shows that spikes in traffic targeting older CVEs often precede new CVE disclosures for that same vendor within weeks. These early warnings give organizations time to harden systems, patch, monitor, or block probing IPs.
By detecting shifts in attacker reconnaissance prior to CVE disclosure, GreyNoise provides a critical window of opportunity to prepare before a threat materializes.
How GreyNoise Helps You
Prepare for New CVEs
Provides Time to Prepare
When a new CVE hits critical perimeter systems, it can trigger emergency response and disruption. Early warnings from GreyNoise let teams prepare in advance and minimize impact
Aligns Risk Assessments to Real-World Threat Activity
GreyNoise shows which vendors and technologies are seeing abnormal reconnaissance levels, keeping risk assessments aligned with real-world signals.
Improves Resource Allocation
Defenders can focus investments, patching, and monitoring on upcoming threats most likely to impact them.
Enables Proactive Blocking
Use GreyNoise query-based, dynamic blocklists to stop attacks as your organization patches exposed systems.