Not all alerts are created equal
Filter out noisy, low priority and false-positive alerts from mass internet scanners
Overview
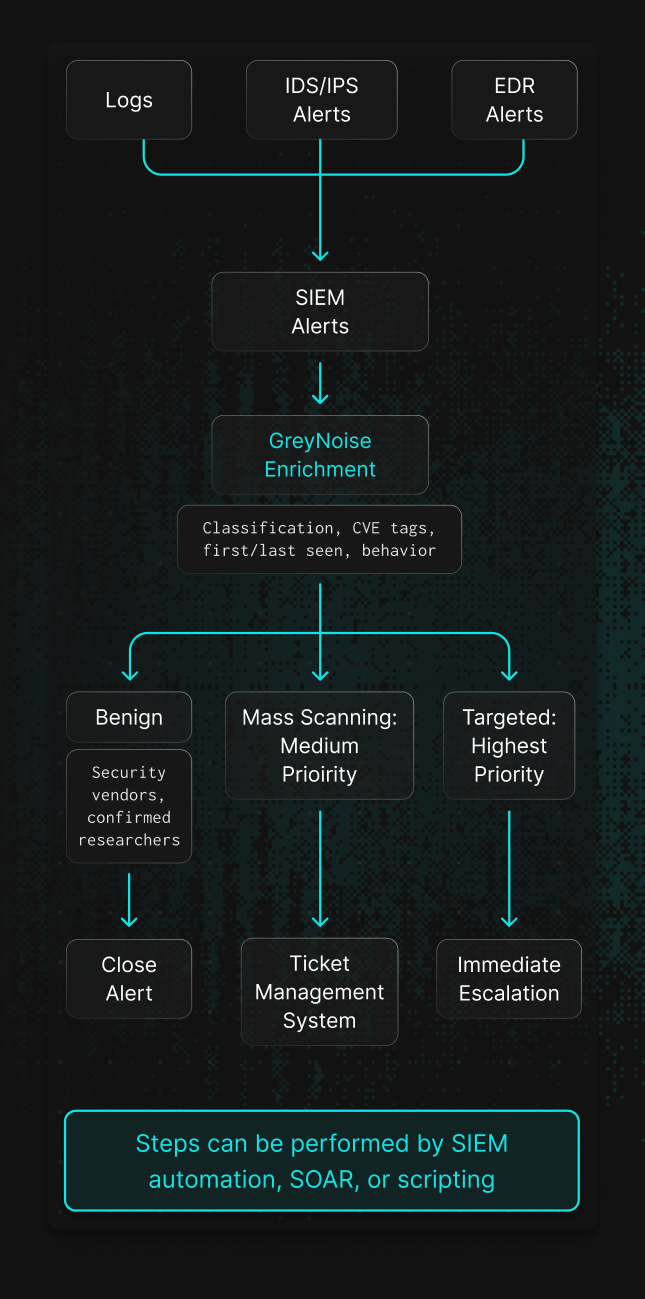
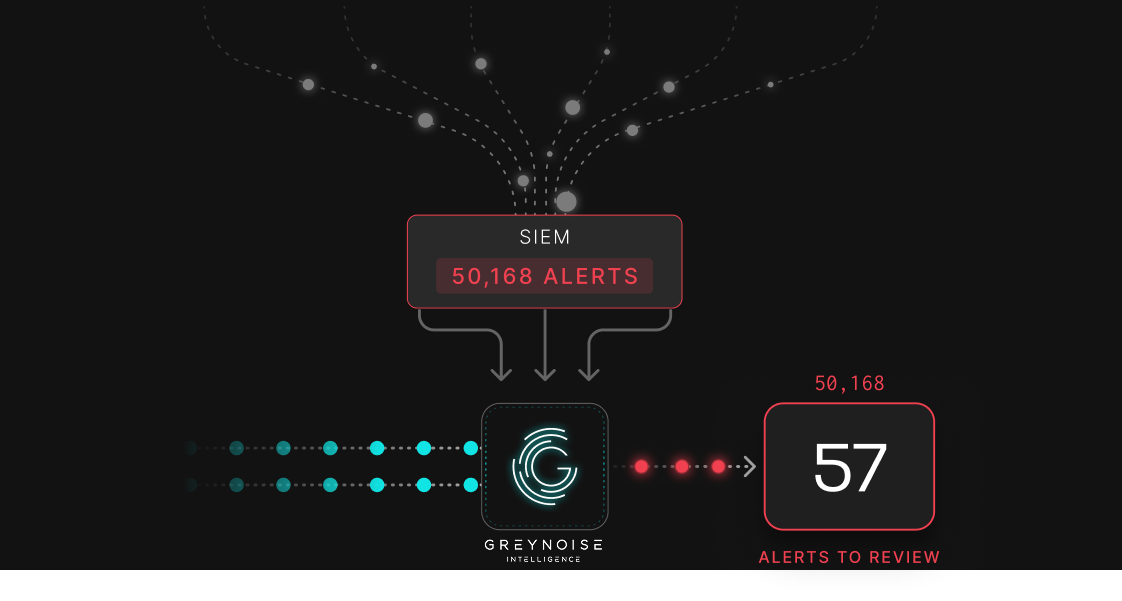
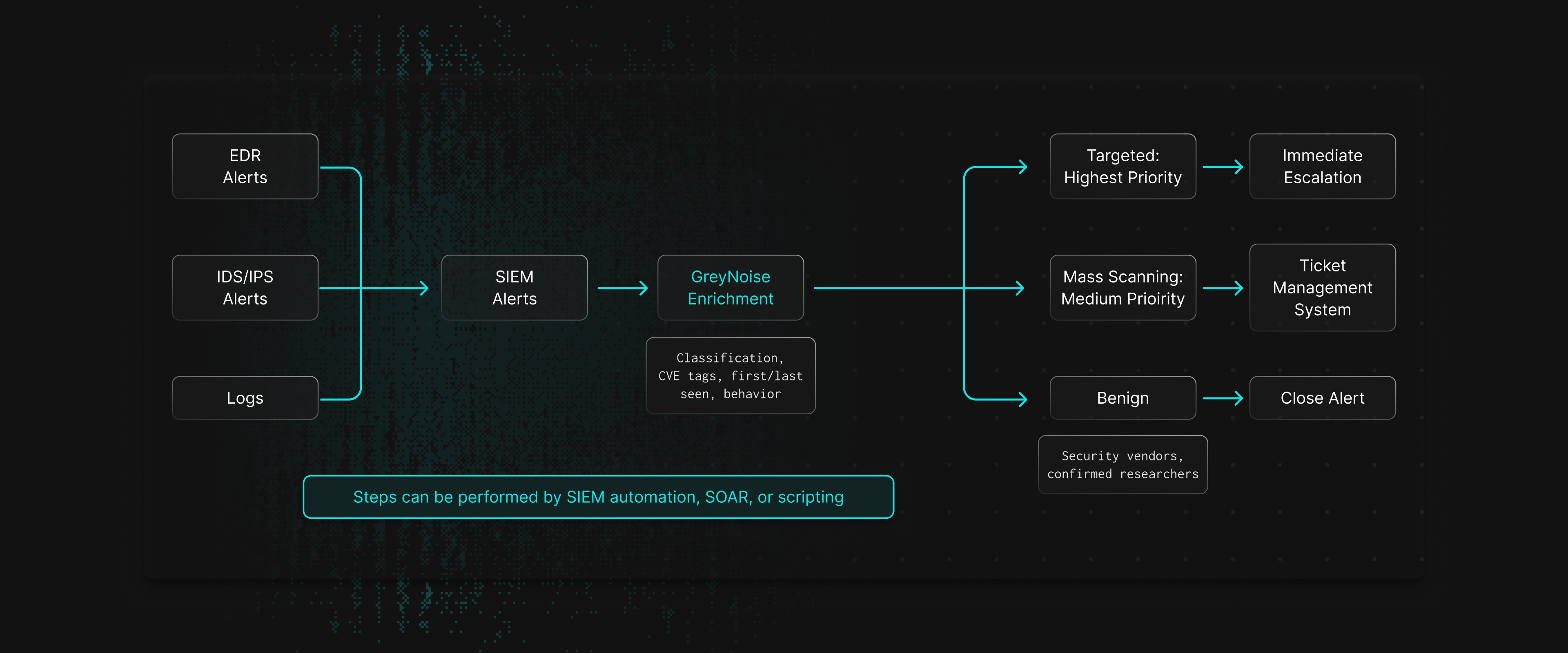
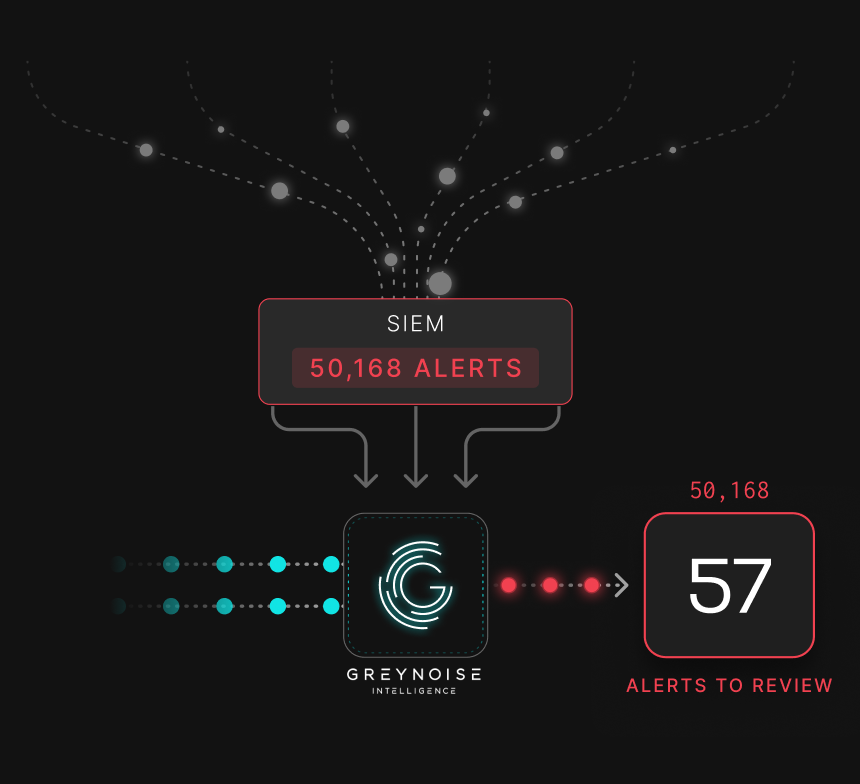
The internet is noisy. Thousands of mass scanners scan the internet every minute, some for legitimate reasons, others to build victim pipelines. Advanced threat actors intentionally create noise to obfuscate more targeted attacks. This creates an unprecedented flood of alerts for your security team.
GreyNoise reduces alert fatigue by classifying IPs as benign, malicious, or suspicious. This instantly separates noise from real threats. Benign traffic can be deprioritized, malicious and suspicious activity escalated for investigation.
How GreyNoise Helps
Reduce Noise in Your SOC
Reduce Alert Fatigue
By classifying benign sources, GreyNoise eliminates noise from the alert triage queue, preventing wasted analyst time.
Escalate Confirmed Threats
Alerts tied to IPs classified as malicious—such as active exploitation, malware distribution, or botnet activity—can be automatically prioritized.
Smarter Automation
SOC playbooks can use GreyNoise classifications and tags to automate alert routing.
Block Unsolicited Scan Traffic
Use GreyNoise query-based, dynamic IP blocklists to block unsolicited scanning and reduce SOC noise.
How it Works