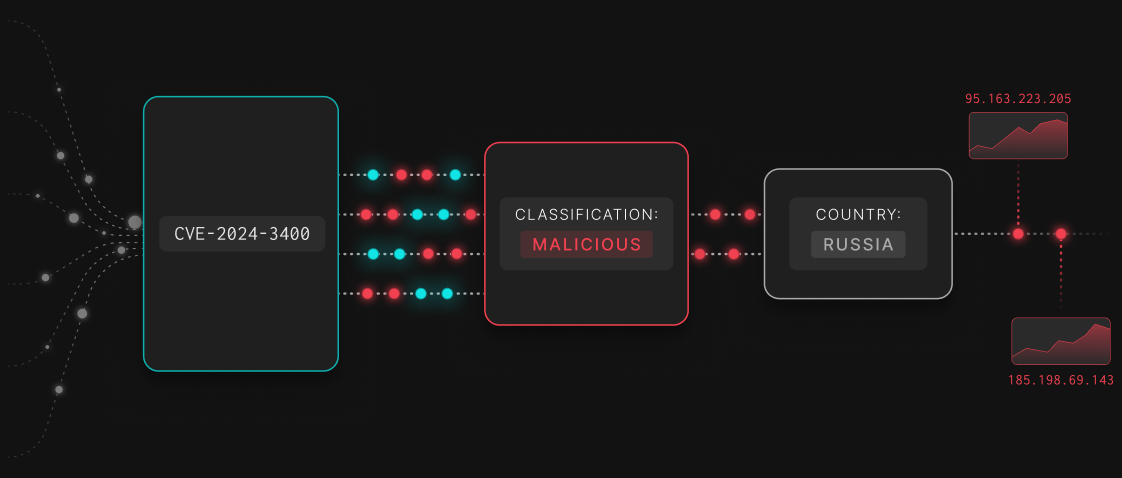
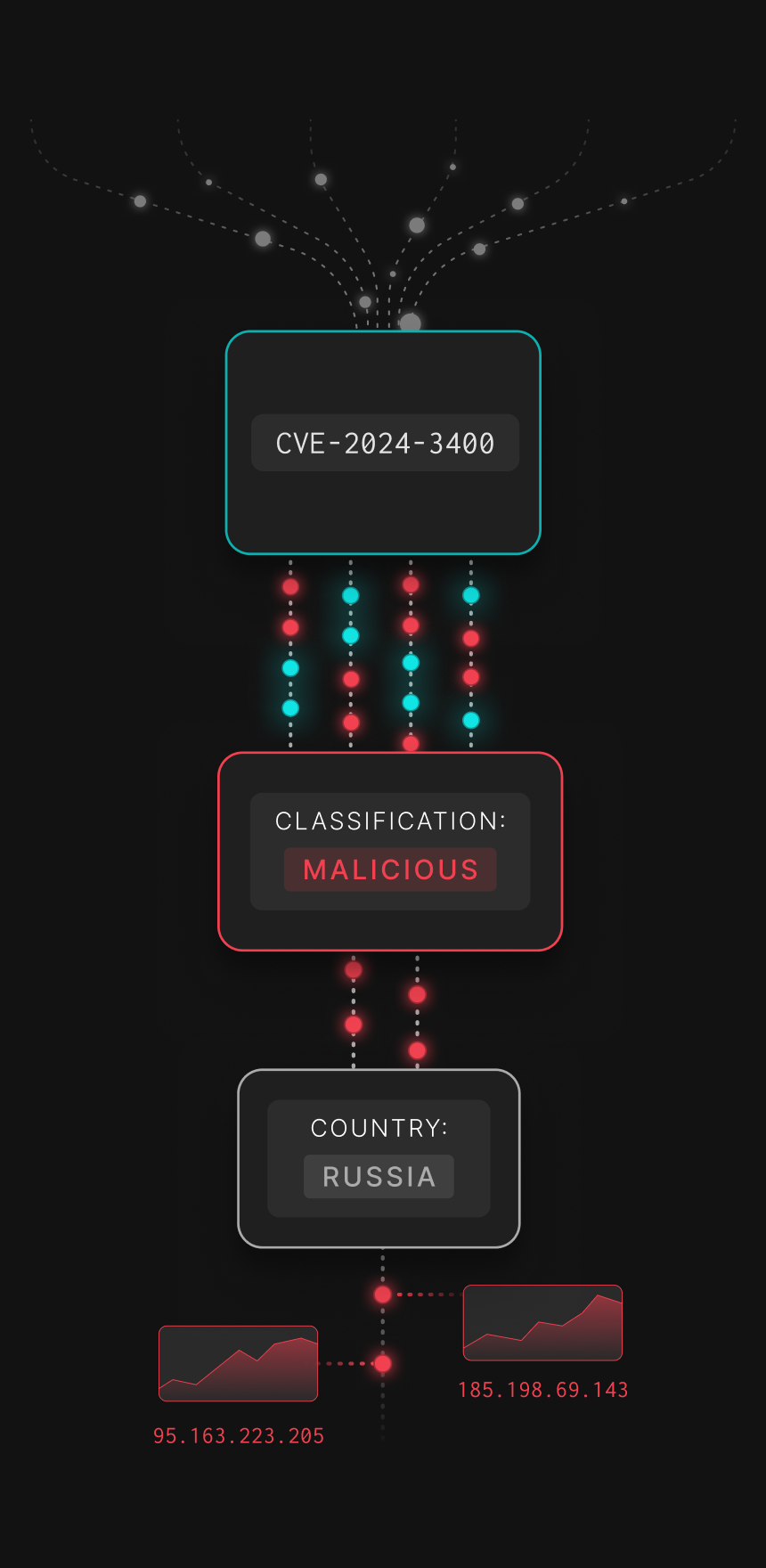
Needle in the haystack. Found
Quickly identify anomalous behavior and catch targeted threats
Overview
Effective threat hunting isn't just about finding more data, it’s about finding the right data. GreyNoise empowers your hunt team to adopt the PEAK Framework by correlating your internal traffic against our real-time map of internet-wide mass scanning.
By using GreyNoise to filter out opportunistic probes, benign scanners, and botnet noise, you reveal the statistically significant anomalies that represent targeted attacks. Stop chasing false positives and focus on the signals that actually threaten your perimeter.
How GreyNoise
Helps You Hunt Smarter
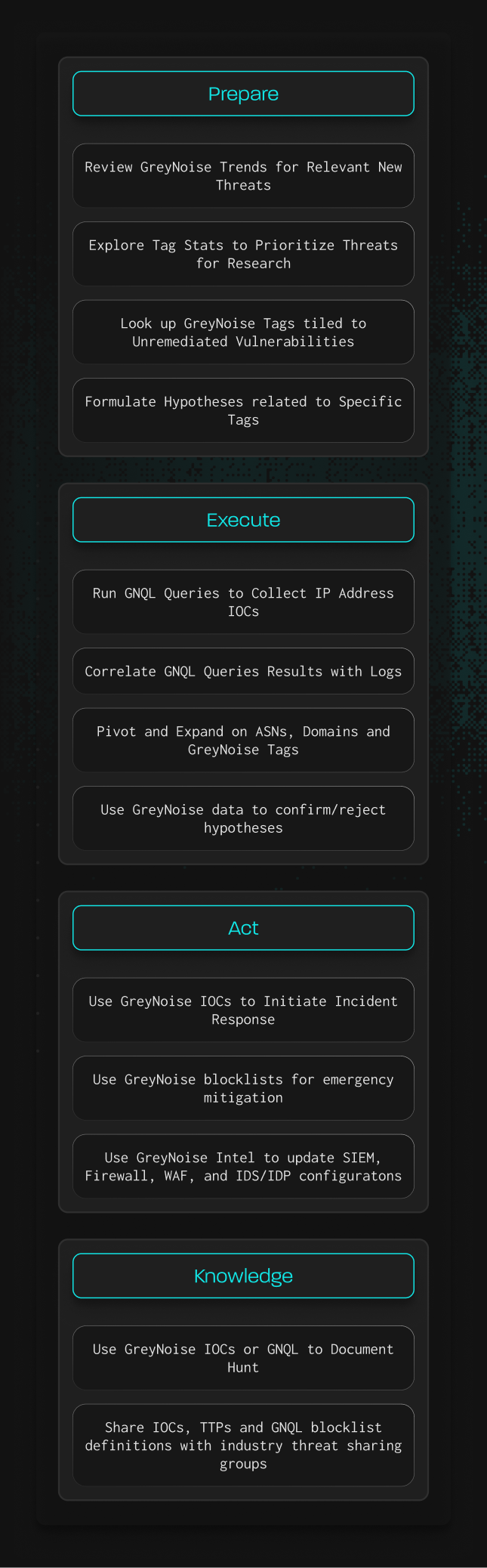
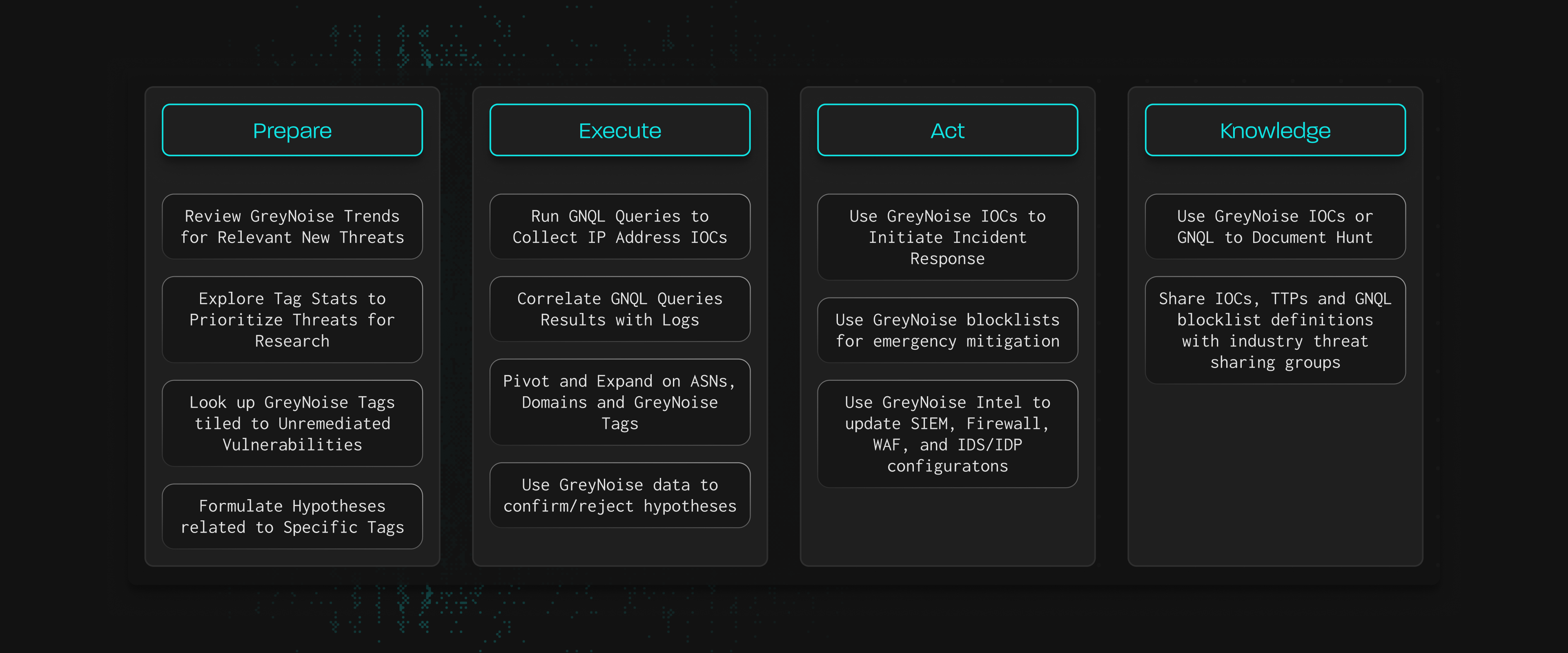
Focus effort on highest risks
Eliminate time-consuming research of benign and opportunistic scanning, allowing hunters to focus on infrastructure actually used by threat actors.
Supports threat research and hypothesis development
Hunters can use GreyNoise to conduct threat research, validate assumptions, and explore attack vectors in order to develop hypotheses.
Correlate isolated incidents
GreyNoise helps threat hunters link isolated incidents to larger campaigns by mapping attacker infrastructure and patterns, connecting logged IPs to those exploiting relevant vulnerabilities.
How GreyNoise Maps to the PEAK Hunting Framework