One of our engineers was reviewing our telemetry dashboard when he came across something unusual:
A tight cluster of red dots — each one representing a malicious IP — lighting up a rural patch of New Mexico:
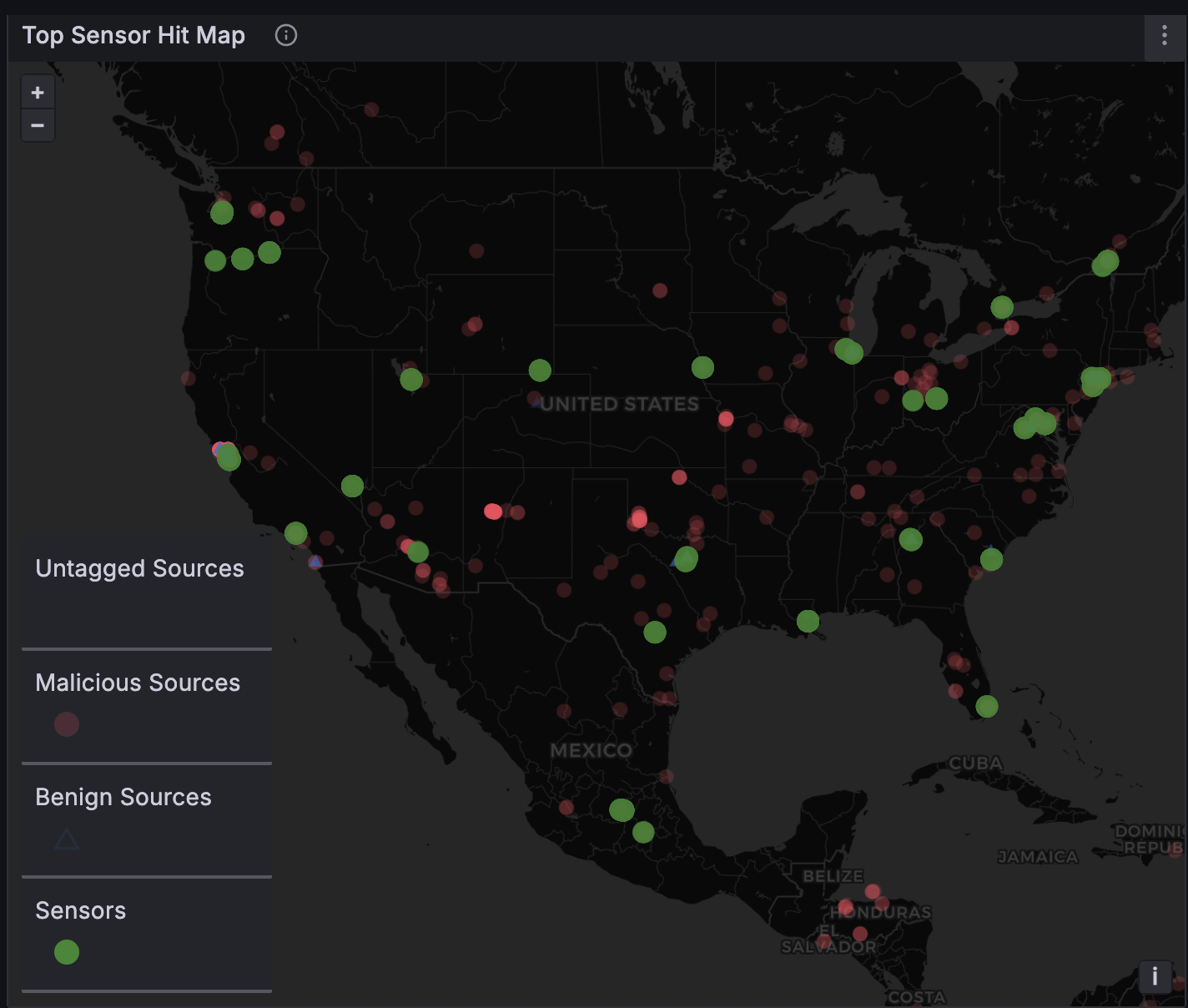
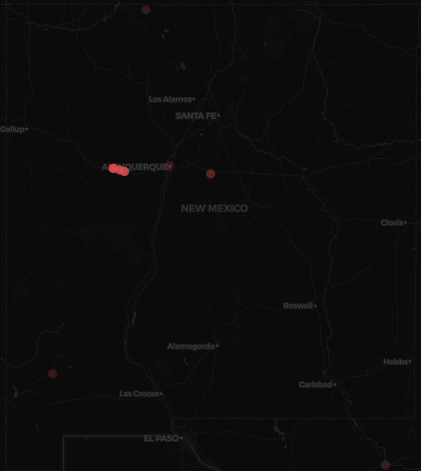
Nothing unusual about botnet traffic. But this time, dozens of malicious IPs were all coming from a single region with a population of just over 3,000 people.
It didn’t fit the pattern. So we dug in.
Starting with a Single IP
We zoomed into the map and picked up the first IP: 137.118.82.76.
It had a troubling combination of GreyNoise tags:
- Telnet Bruteforcer
- Generic IoT Default Password Attempt
- Mirai
- D-Link Hardcoded Telnet Attempt
This wasn’t just a misconfigured device — it looked like a system actively participating in a botnet.
So we pulled the thread.
A Utility at the Center — and AI in the Loop
Zooming out, we found ~90 IPs in the same New Mexico region, all tied to a single provider: Pueblo of Laguna Utility Authority.
100% of this traffic was Telnet-based.
To dig deeper, we used our internal tooling — including the GreyNoise Model Context Protocol (MCP) server (an AI-powered analysis environment) — to iterate quickly on investigation paths.
We fed IP metadata and network behavior into Claude, exploring ideas in real time. We then used Censys infrastructure data and tshark packet captures to enrich the dataset.
This AI-powered analysis helped confirm that many of the systems were VOIP-enabled devices.
While we did not identify exact device models for each system, enrichment suggested hardware from Cambium Networks was likely involved in a portion of the activity.
It wasn’t a one-off misconfiguration — it appeared to be a coordinated cluster of similar systems likely running comparable stacks.
Tracing it Globally
After confirming the localized activity, we widened the investigation.
Using GreyNoise tags, behavioral similarity, and Telnet traffic patterns, we identified about 500 IPs globally exhibiting similar traits:
- A unique JA4t signature — 5840_2-4-8-1-3_1460_1 — representing 90% of the traffic from this ISP, indicating the hardware is similar across compromised hosts.
- Telnet login attempts using weak or default credentials
- High session volumes
- Scanning behavior aligned with known Mirai variants
Some of these IPs were linked to VOIP-capable devices and shared similar infrastructure characteristics — suggesting a wider class of exposed systems is being targeted for botnet activity.
Why VOIP? Why Now?
VOIP devices often run on older Linux-based firmware, sometimes with Telnet exposed by default. They’re also frequently:
- Internet-facing
- Lightly monitored
- Infrequently patched
Some Cambium routers, for example, may still be running firmware versions impacted by a known remote code execution (RCE) vulnerability from 2017.
While we did not confirm exploitation of that CVE in this case, the activity reinforces a broader point: Vulnerabilities remain part of the attack surface long after disclosure.
We recently explored this dynamic in our latest report on resurgent vulnerabilities, where we highlight how long-patched flaws in edge devices are repeatedly targeted.
Then It Stopped
Shortly after a member of our team posted a brief mention of the activity on social media, the traffic from the New Mexico utility dropped off — completely.
Whether coincidence or evidence that attackers monitor visibility, it was a sharp cutoff.
And shortly after that, activity spiked yet again and the global behavior continued.
Why This Matters
- VOIP systems are often overlooked in security monitoring.
- Small utilities and ISPs may unknowingly contribute infrastructure to global botnets.
- Mirai-style botnets remain opportunistic, leveraging systems wherever available.
What started as a spike from a single utility in a rural part of the United States became a lens into an ongoing global pattern — one defenders should track closely.
Defender Recommendations
- Block IPs involved in this activity.
- Use GreyNoise to identify if your infrastructure is being conscripted into a botnet.
- Audit Telnet exposure, especially on VOIP-enabled systems.
- Rotate or disable default credentials on edge and SOHO devices.
GreyNoise has developed an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats. Click here to learn more about GreyNoise Block.
---
This investigation was sparked by GreyNoise’s keen-eyed Lead Software Engineer Jeff Golden, with contributions from the broader GreyNoise research team.










.png)
