In May 2025, the European Union took aim at Stark Industries Solutions, a web hosting provider that had become a prime real estate for Russian state-sponsored cyber operations. Sanctions dropped. Assets frozen. Names on lists. The whole regulatory apparatus just doing its thing.
Stark Industries shrugged and kept hosting.
Here's what makes this story worth your time: Stark Industries didn't just survive EU sanctions—they anticipated them, and thrived through them. The Neculiti brothers got a heads-up roughly twelve days before the official announcement, courtesy of leaked EU documents hitting Moldovan media. That's not a lot of time to restructure a hosting empire, but it turns out to be plenty when you control the right infrastructure levers.
By the time sanctions landed on May 20th, Autonomous System AS44477 had already been transferred to a new RIPE organization, Russian infrastructure had migrated to Moscow-based UFO Hosting LLC, and the groundwork was laid for a complete rebrand to "THE.Hosting" under Dutch entity WorkTitans B.V. No frantic scrambling. No operational chaos. Just a methodical shuffle of autonomous systems, IP blocks, and corporate shells that rendered months of regulatory work largely moot.
Founded literally two weeks before Russia invaded Ukraine—subtle, that—Stark Industries quickly became infrastructure-of-choice for DDoS campaigns, disinformation operations, and threat actors like FIN7. They offered all the bulletproof hosting classics: crypto payments, servers in jurisdictions with flexible abuse policies, and a business model built around plausible deniability.
But here's the thing that matters for those of us tracking internet noise: while the legal entities changed and the branding got a fresh coat of paint, the underlying network infrastructure kept singing the same song. The autonomous systems, the IP space, the routing patterns—that's where the truth lives. Corporate paperwork may lie, but packets do not.
Let's see how sanctions evasion actually works when you control your own ASN, and what the network layer reveals.
Signals In The Noise
Analysis of GreyNoise's Global Observation Grid data confirms a seamless migration of malicious infrastructure from AS44477 (PQ Hosting Plus S.R.L.) to AS209847 (WorkTitans B.V.) between August and November 2025. The behavioral signatures, geographic distribution, VPN services, and scanning patterns provide strong evidence this represents the Stark Industries rebranding operation.
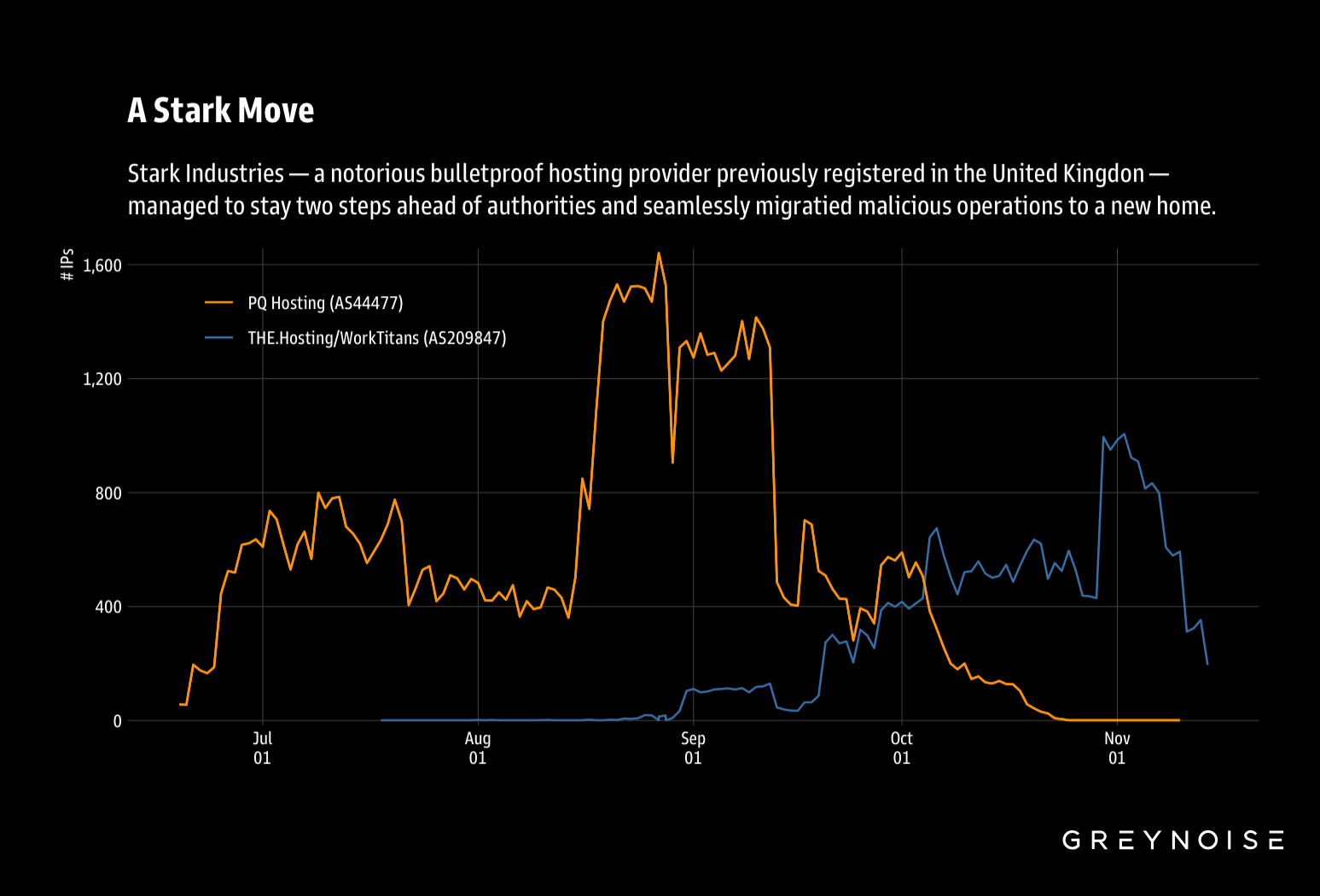
The migration timeline:
AS44477 (PQ Hosting) Activity:
- Peak activity: Aug 18 - Sep 15
- Sharp decline: Week of Oct 20
- Near-complete abandonment: Nov 10
AS209847 (THE.Hosting/WorkTitans) Activity:
- Minimal activity before mid-August (allocated on Jun 24, 2025)
- Ramp-up begins: Aug 25
- Normal malicious operations maintained through migration and post-AS44477 abandonment
The GreyNoise tags used across the ASN switch were virtually identical, however the migration seems to have enabled them to do more with less, since the daily tag distribution skews higher, overall, but they're using less IP infrastructure to accomplish the same goals.

Both ASN's share 24 VPN services in common, but 11 (ABVPN_VPN, ALT_VPN, AMNEZIA_VPN, FLY_VPN, MYSTERIUM_VPN, NURICHINA_VPN, QUARK_VPN, ROCKET_VPN, SUNSSH_VPN, VEEPN_VPN, XVPN_VPN) did not come along for the ride (yet), and 9 new ones (ALOHA_BROWSER_VPN, GIAMPING_VPN, LUMOS_VPN, PLEX_VPN, SSHMAX_VPN, SSHOCEAN_VPN, VPN3000_VPN, VPNJANTIT_VPN, ZOOG_VPN) joined in the frey.
Excluding that massive attempt to evade network detection responses via network packet maximum segment size (MSS) manipulation (indicated by the significant elevation in daily unique IP counts between mid-August and mid-September), the pre- and post-migration JA4T hashes also show overlapping source hardware and OS stack footprints. However, some are missing (due to, for example, the loss of the indicated VPN providers), and others are new (due to, again, for example, the gaining of the new VPN providers).
From every angle, our data clearly shows that this is, indeed, the Stark we all knew and loathed. And, thanks to the leak of the sanctions activity, they were able to move fast and can now continue to [attempt to] break things; and do so even more efficiently than before.









.png)

