On 2 December 2025, GreyNoise observed a concentrated spike of 7,000+ IPs attempting to log into Palo Alto Networks GlobalProtect portals. All activity originated from infrastructure operated by 3xK GmbH and targeted two Palo Alto profiles in GreyNoise’s Global Observation Grid (GOG).

.png)
While the spike — both IP- and session-based — was brief, its significance became clear only when compared with earlier activity.
A Returning Fingerprint
The December traffic shares three identical client fingerprints with a larger wave GreyNoise observed between late September and mid-October.
That earlier activity originated from four ASNs not generally associated with malicious infrastructure:
- NForce Entertainment B.V. (AS43350)
- Data Campus Limited (AS215929)
- Flyservers S.A. (AS209588)
- Internet Solutions & Innovations LTD. (AS211632)
Over several weeks, these ASNs generated over 9 million non-spoofable HTTP sessions, with the majority targeting GlobalProtect portals and related authentication surfaces.
.png)
The return of the same client fingerprints — now from entirely different hosting infrastructure — indicates tooling continuity across what appear to be separate events.
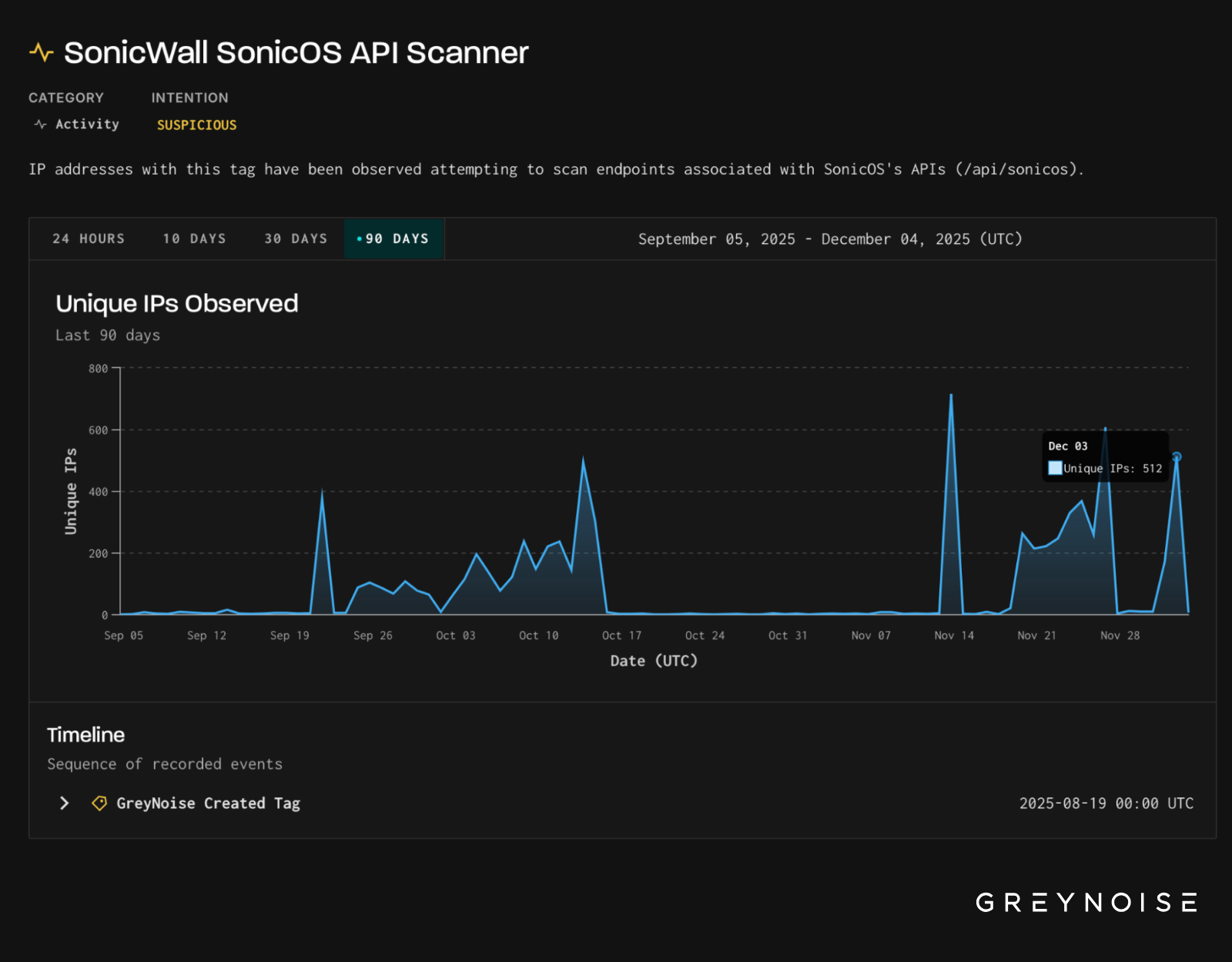
SonicWall Activity Shows the Same Fingerprints
On 3 December, GreyNoise also recorded a surge in scanning against SonicWall SonicOS API endpoints.
This traffic carried the same three client fingerprints, linking it directly to:
- The 2 December GlobalProtect login spike, and;
- The September – October login and bruteforcing spike.
The infrastructure changed. The vendors targeted were different. Yet, the client fingerprinting remained identical.
.png)
Campaign Cadence
The combined telemetry shows a clear sequence:
- Late September – Mid October: high-volume login and bruteforce attempts from “clean” ASNs.
- Late November: reduced activity, with intermittent sessions around the Thanksgiving period.
- 2 December: reappearance of the same scanning client on 3xK’s infrastructure, focused on Palo Alto portals.
- 3 December: SonicWall SonicOS API scanning using the same three fingerprints.
Block IPs Linked to This Campaign
GreyNoise Block customers can block all IPs triggering these GreyNoise tags via GreyNoise Block, using the following templates:
- Palo Alto (All activity)
- SonicWall (All activity)
Customers can also modify the template to specify source country, other IP classifications, etc. New users can get started with a 14-day free trial.
Enterprise customers have targeted blocklists available in the platform (specifying ASNs, JA4, destination country, etc), supporting full queries leveraging the entirety of GreyNoise’s parameters.
- PALO ALTO: BLOCK IPS WITH PLATFORM BLOCKLIST
- SONICWALL: BLOCK IPS WITH PLATFORM BLOCKLIST
In addition, defenders should:
- Monitor authentication surfaces for abnormal velocity or repeated failures.
- Track recurring client fingerprints to surface campaign continuity.
- Apply dynamic, context-aware blocking rather than static reputation lists.
Fingerprint-level telemetry exposes cross-infrastructure relationships that defenders might otherwise miss.
All GreyNoise customers will receive more detailed information in our next At The Edge intelligence brief, including JA4T fingerprints and more.
GreyNoise will continue monitoring the situation and provide updates as necessary.
— — —
Stone is Head of Content at GreyNoise Intelligence, where he leads strategic content programs that translate complex internet-scale threat activity into clear, actionable insights. Previously, he led partnered research initiatives with Google and the U.S. Department of Homeland Security, and was a member of the Council on Foreign Relations Young Professionals group. His background spans finance, technology, and engagement with the United Nations on global policy issues.







.png)



.png)