Update: 9 October
GreyNoise identified a connection between three campaigns targeting Cisco, Palo Alto, and Fortinet firewalls and VPNs. We observed infrastructure overlap between recent Cisco ASA scanning, Palo login attempts, and Fortinet brute force attempts:
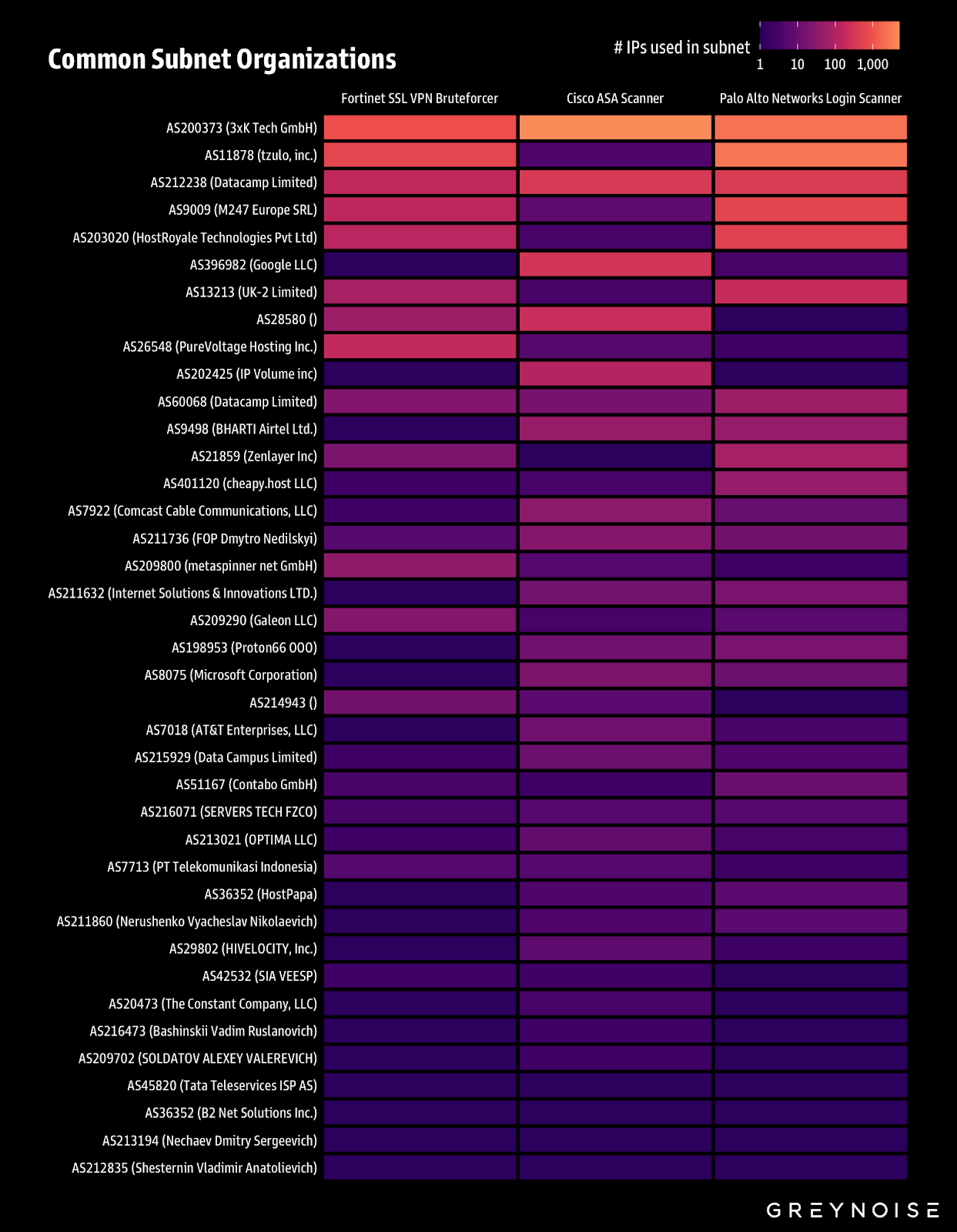
See the full update here.
Update: 29 September 2025
GreyNoise has produced an Executive Situation Report (SITREP) on the situation, intended for decision makers.
Update: 26 September 2025
Yesterday, Cisco announced two zero-day vulnerabilities affecting their Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) platforms. These disclosures come just weeks after GreyNoise reported a surge in scanning activity against Cisco ASA devices (see initial reporting below). The timing is notable because recent research found that spikes in attacker activity against a specific technology (white dots) may serve as an early warning signal for future vulnerability disclosures affecting that same technology (red dots).
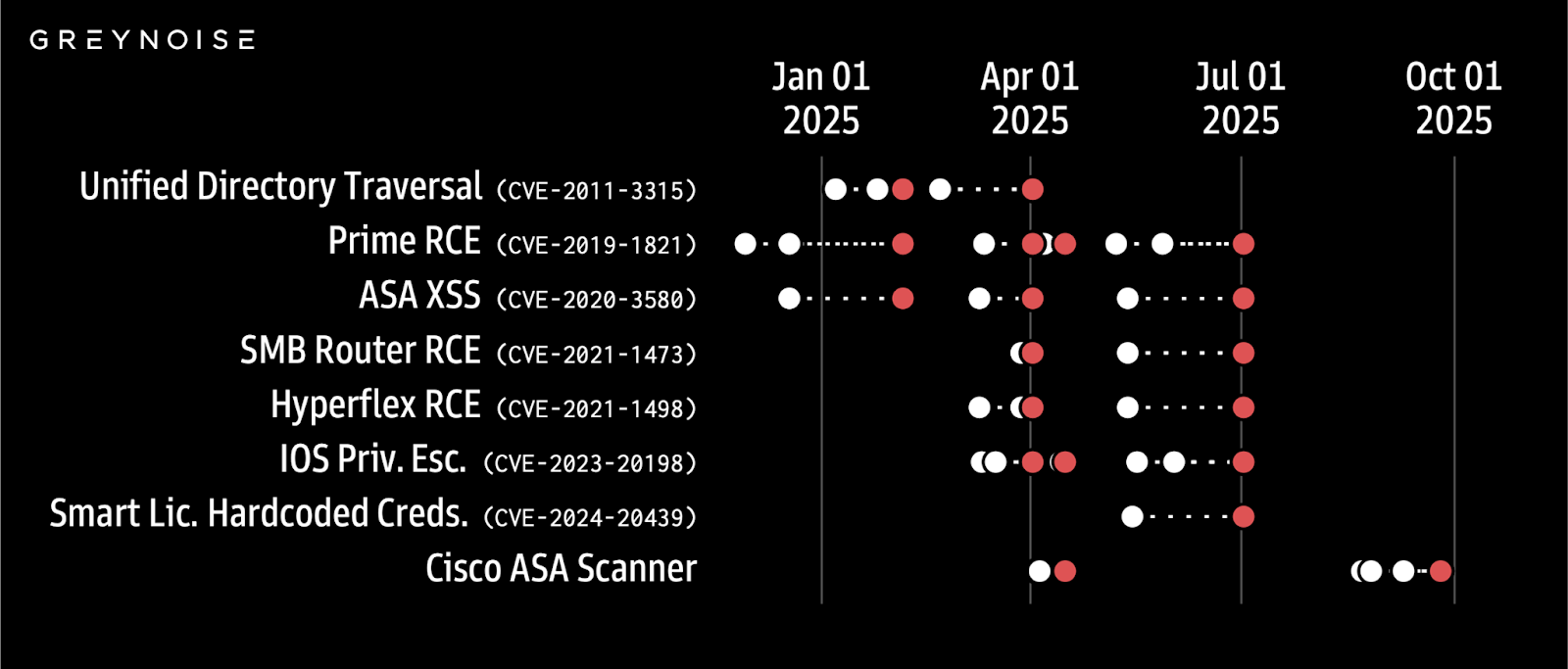
GreyNoise’s detection of 25,000 IPs scanning Cisco ASA in the weeks leading up to two zero day disclosures is a clear example of this research turning into reality:
“This is a real signal we’re seeing in our data across enterprise edge tech,” said boB Rudis, VP of Data Science and Security Research at GreyNoise. “We see elevated attacker activity against XYZ tech and then weeks later, new CVEs are disclosed affecting XYZ tech. This has repeatedly happened across enterprise edge, with Cisco ASA being the most recent example. So, yes, we’re very excited to learn our data may serve as an early warning signal for future vulnerability disclosures and we hope defenders will use this information to make the world a little safer.”
CISA issued an Emergency Directive (ED 25-03), requiring federal agencies to apply mitigations within 24 hours — representing the third-ever emergency directive since the agency’s founding. Both vulnerabilities, tracked as CVE-2025-20333 and CVE-2025-20362, have been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Resurgent Brute Force Attacks Against Cisco SSL VPNs
After investigating activity against our Cisco profiles, GreyNoise identified resurgent brute force attacks targeting Cisco SSL VPNs occurring yesterday at approximately 1:00pm EST. This activity was preceded by a period of inactivity, ceasing on September 24 at 6PM EST and restarting yesterday. All traffic during this period shares the same client fingerprint and source organization (Global Connectivity Solutions LLP), along with other shared characteristics:
- Example URI: /+webvpn+/index.html
- User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.5005.63 Safari/537.36
Take Action Now
CISA has issued guidance and mitigation instructions related to CVE-2025-20333 and CVE-2025-20362. We encourage defenders to review CISA’s official resources and apply recommended actions.
GreyNoise will continue monitoring its Cisco profiles for anomalous behavior, and will provide updates here as necessary.
---
End of Update
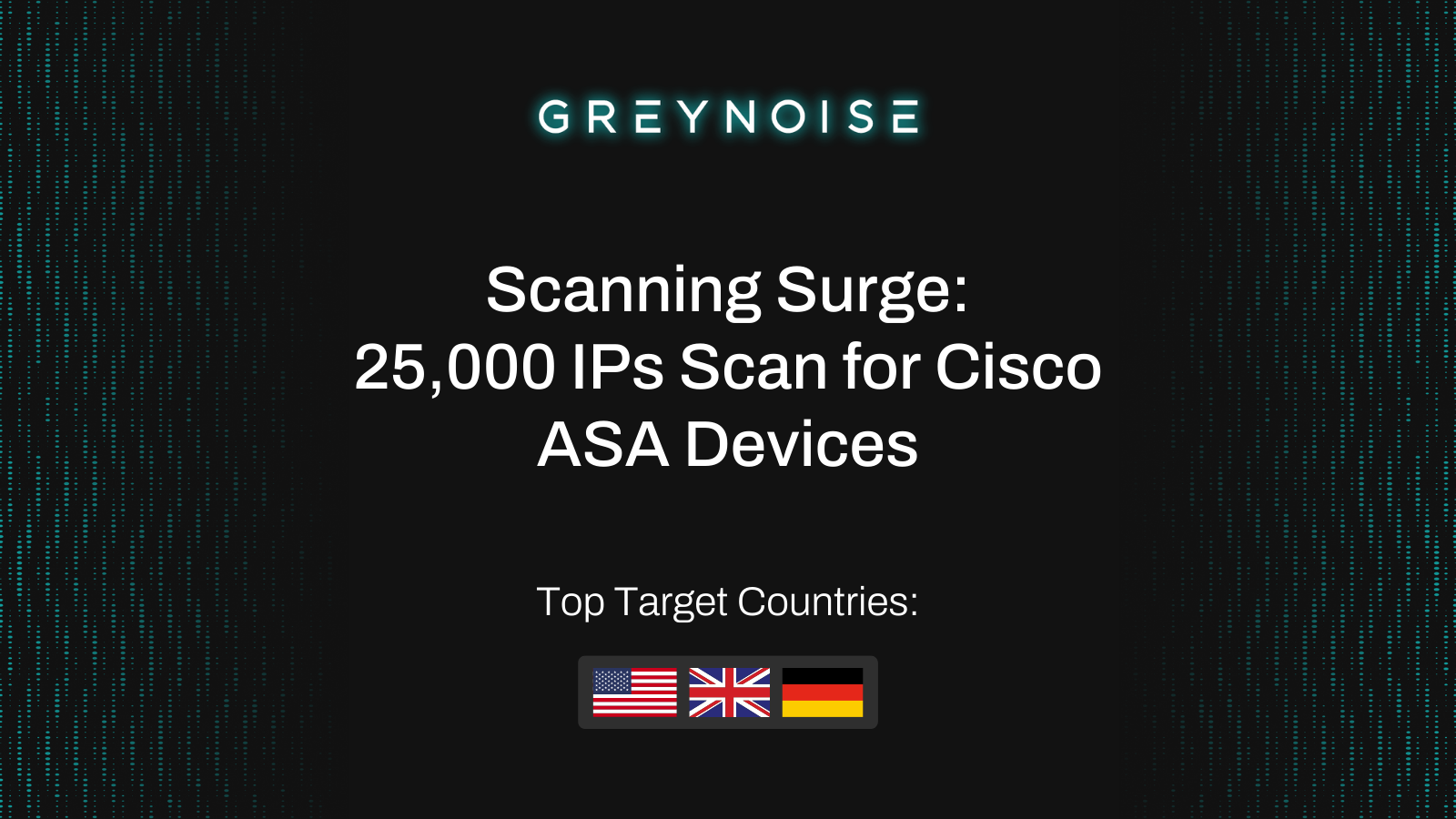
GreyNoise observed two scanning surges against Cisco Adaptive Security Appliance (ASA) devices in late August. The first involved more than 25,000 unique IPs in a single burst; the second, smaller but related, followed days later. This activity represents a significant elevation above baseline, typically registering at less than 500 IPs per day.
Both events targeted the ASA web login path (/+CSCOE+/logon.html), a common reconnaissance marker for exposed devices. Subsets of the same IPs also probed GreyNoise’s Cisco Telnet/SSH and ASA software personas, signaling a Cisco-focused campaign rather than purely opportunistic scanning.
The Two Spikes
- Spike One: ~25,000 IPs scanned ASA login portals; a subset also targeted Cisco IOS Telnet/SSH.
- Spike Two: A smaller wave repeated ASA probing, with subsets hitting both IOS Telnet/SSH and ASA software personas.
- Shared traits: Overlapping client signatures and spoofed Chrome-like user-agents, indicating a common scanning toolkit used across both events.
.png)
Geographic Context
In the past 90 days, GreyNoise has observed traffic triggering its Cisco ASA Scanner tag originating from and targeting the following countries:
Top Source Countries:
- Brazil (64%)
- Argentina (8%)
- United States (8%)
Top Target Countries:
- United States (97%)
- United Kingdom (5%)
- Germany (3%)
Note: Target country percent sum may exceed 100% due to one source IP targeting several IPs based in different countries.
Brazil-Heavy Botnet Behind August 26 Wave
Analysis of the August 26 wave shows that it was driven primarily by a single botnet cluster concentrated in Brazil. By isolating a specific client fingerprint, and reviewing two months of activity, GreyNoise determined that this fingerprint was used exclusively to scan for Cisco ASA devices.
On August 26:
- 16,794 IPs were observed scanning ASA devices.
- 2,858 did not match this client signature.
- Meaning roughly 14,000 of the ~17,000 IPs active that day — more than 80% — were tied to this botnet.
The client signature was seen alongside a suite of closely related TCP signatures, suggesting all nodes share a common stack and tooling. This makes the August 26 spike attributable to a coordinated botnet campaign dominated by Brazil-sourced infrastructure.
Could Indicate Upcoming Cisco ASA Vulnerability Disclosure
GreyNoise’s Early Warning Signals research shows that scanning spikes often precede disclosure of new CVEs. In past cases, activity against GreyNoise’s Cisco ASA Scanner tag surged shortly before a new ASA vulnerability was disclosed (see last row in chart below). The late-August spikes may represent a similar early warning signal.
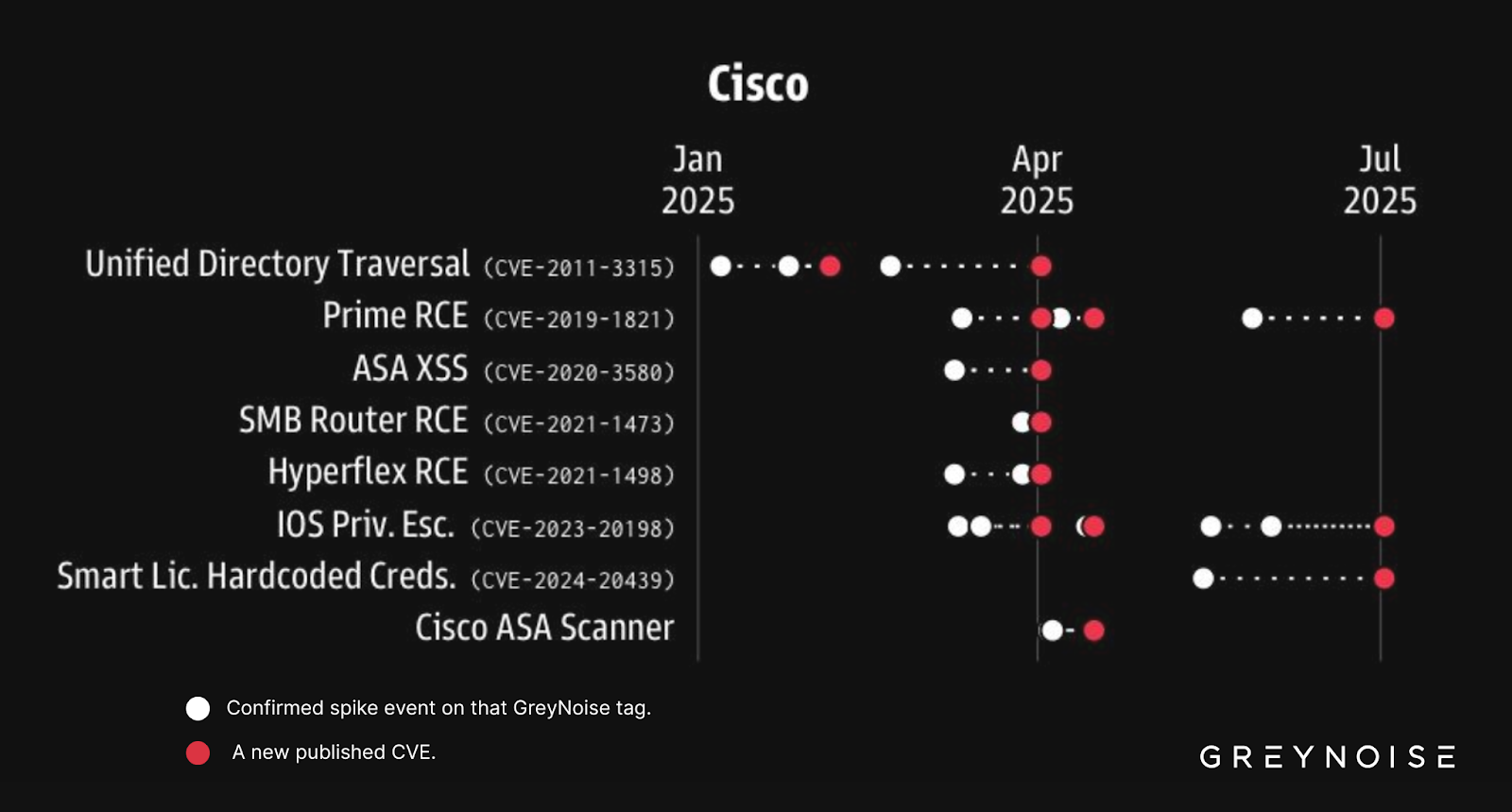
Even if organizations are fully patched, blocking these IPs now may reduce the likelihood of appearing on target lists used to exploit new CVEs in the future.
Related Real-World Precedent
- Espionage: The ArcaneDoor campaign used two zero-days in Cisco ASA (Line Dancer, Line Runner) to infiltrate government networks.
- Ransomware: The Akira and LockBit ransomware groups have historically targeted Cisco ASA systems.
- Global Campaign: CVE-2020-3452 was weaponized worldwide soon after disclosure, with exploitation attempts observed within days.
Defender Takeaways
- Limit exposure: Avoid placing ASA web portals, Telnet, or SSH directly on the internet.
- Patch quickly if a new CVE emerges: ASA vulnerabilities have historically been exploited soon after disclosure.
- Require MFA: Strengthen remote access with multi-factor authentication.
Monitor GreyNoise’s Cisco ASA tags for real-time scanning and exploitation activity:
- Cisco ASA Scanner
- Cisco ASA CVE-2020-3259 Information Disclosure Attempt
- Cisco ASA Information Disclosure Attempt
- Cisco ASA XSS Attempt
- Cisco ASA Arbitrary File Retrieval Attempt
GreyNoise will continue monitoring the situation and update this blog as necessary. Concentrated reconnaissance bursts, such as those in August, should be treated as potential early indicators of future vulnerability disclosures.
Please contact your GreyNoise support team if you are interested in the JA4+ signatures in this investigation.
GreyNoise has developed an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats. Click here to learn more about GreyNoise Block.
— — —
This research and discovery was a collaborative effort between Towne Besel and Noah Stone.










.png)