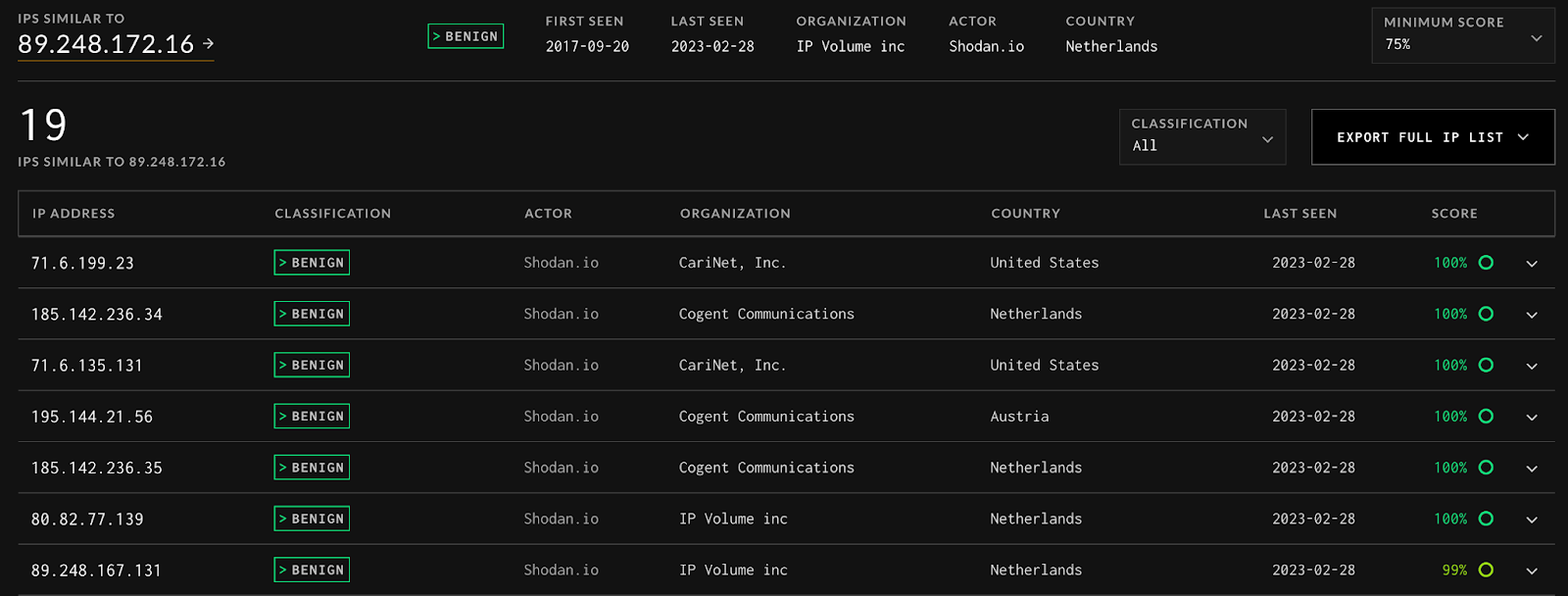
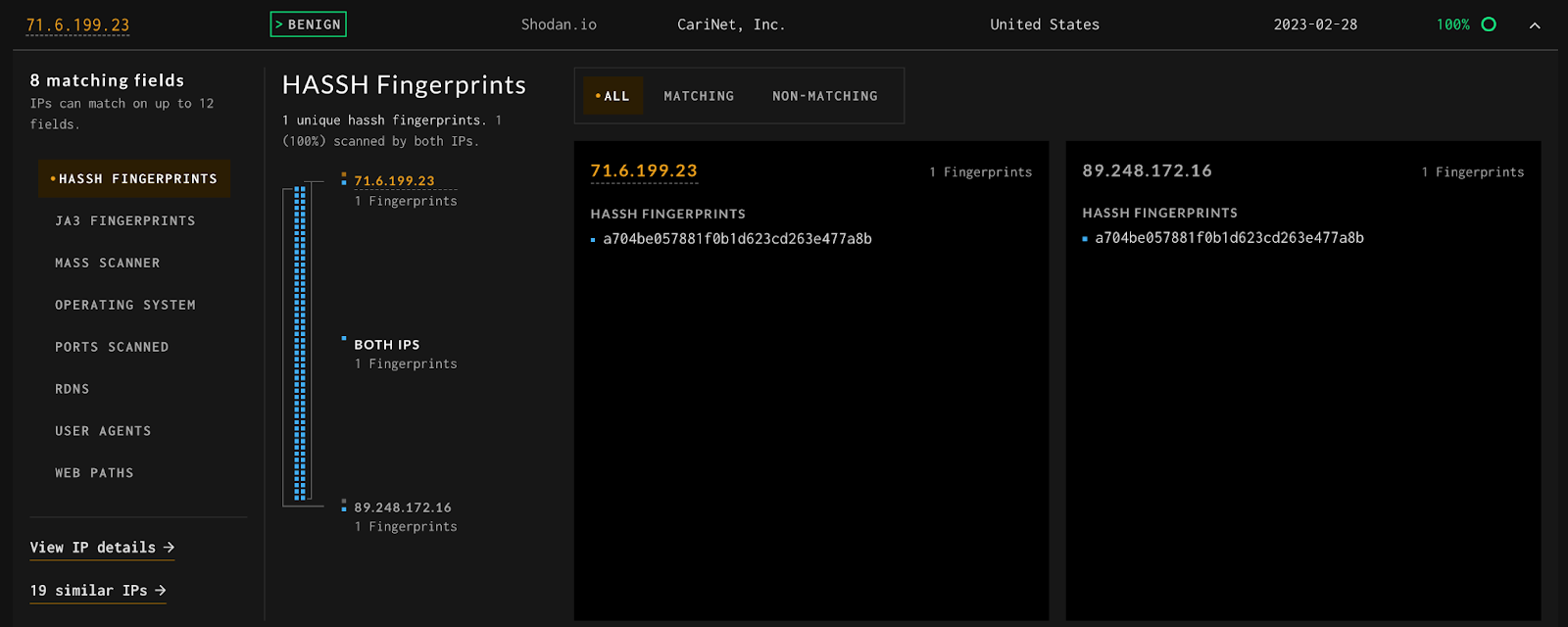
The World Needs A Better Blocklist
Security teams already have access to blocklists; commercial feeds, community lists, vendor-curated sets of bad IPs — they’ve been around for decades. And yet, every practitioner has experienced the same frustrations: the lists are too noisy, too static, too opaque, too slow to update, or just not quite meeting the right criteria.
That’s why GreyNoise built Block, a blocklist approach designed to be highly configurable, grounded in primary-sourced intelligence, and updated in real-time as attacker behavior changes.
The Limits of Traditional Blocklists
Most blocklists share common issues:
- Lack of context — You see an IP is bad, but not why.
- Lagging updates — Exploitation campaigns evolve by the minute, while lists update daily (or worse).
- Overblocking — Feeds often include research scanners, crawlers, or actual business service infrastructure, causing collateral damage.
- Rigid design — Few ways to tune blocklists to match the unique risk tolerance of your environment.
As a result, network security teams struggle to balance security and availability, concerned that they’ll block legitimate traffic or fail to block malicious traffic.
Why GreyNoise Block is Different
GreyNoise approaches blocklists from a different angle:
- Configurable with GreyNoise Query Language (GNQL) — Security teams can define exactly what they want to block. For example:
- IPs exploiting a specific CVE.
- Hosts scanning your technology stack.
- Sources from certain geographies.
- Accurate and timely — Data is updated continuously. When a new exploitation campaign starts, it shows up in GreyNoise in near real time.
- Reduced noise — Traffic like academic research or vendor scanners is categorized as benign and can be easily excluded from blocklists, avoiding the overblocking that plagues generic feeds.
- Primary-sourced data — All entries come from the GreyNoise global sensor network, which collects unsolicited internet traffic at scale. These are IPs actively scanning, exploiting, or behaving like attacker-controlled infrastructure.
Practical Advantages for Network Security
GreyNoise Block delivers practical benefits to cybersecurity teams:
- Focus on most relevant malicious traffic — Stop traffic targeting technology vendors important to your network.
- Respond faster during incidents — Use GNQL to generate emergency blocks for malicious IPs while you buy time for patching or remediation.
- Reduce analyst fatigue — By blocking mass scanners and exploitation before it enters the network, GreyNoise Block reduces the number of alerts triggered by IDS/IPS and SIEM systems, reducing the burden on network security and SOC teams.
How Easy it is to Configure
Creating blocklists within GreyNoise Block could not be easier. To optimize flexibility, each blocklist is associated with a GNQL query. For ease of use, GreyNoise includes a set of query templates that provide pre-built blocklists. Start by either selecting a pre-built template or writing a query from scratch.
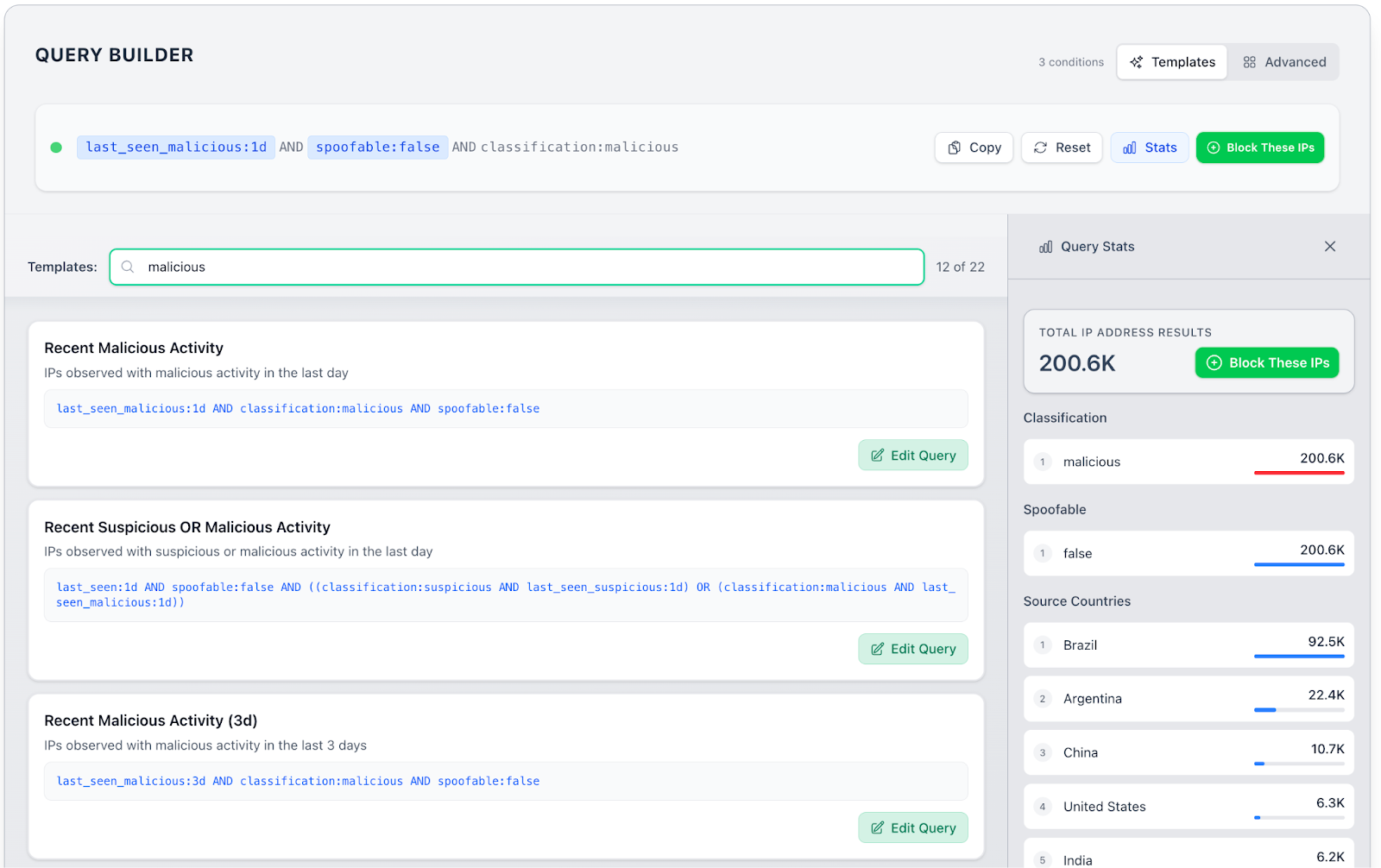
When selecting a template, you can click “Block These IPs” to create a blocklist immediately or click “Edit Query” to refine the blocklist’s criteria even further. When editing the query, you can add, remove, or modify fields and group them logically through and/or clauses. As you modify fields, the Query Stats panel on the right updates automatically.

Once you have the query looking as you want it in the Query Builder, click the “Block These IPs” button to turn the query into a blocklist.
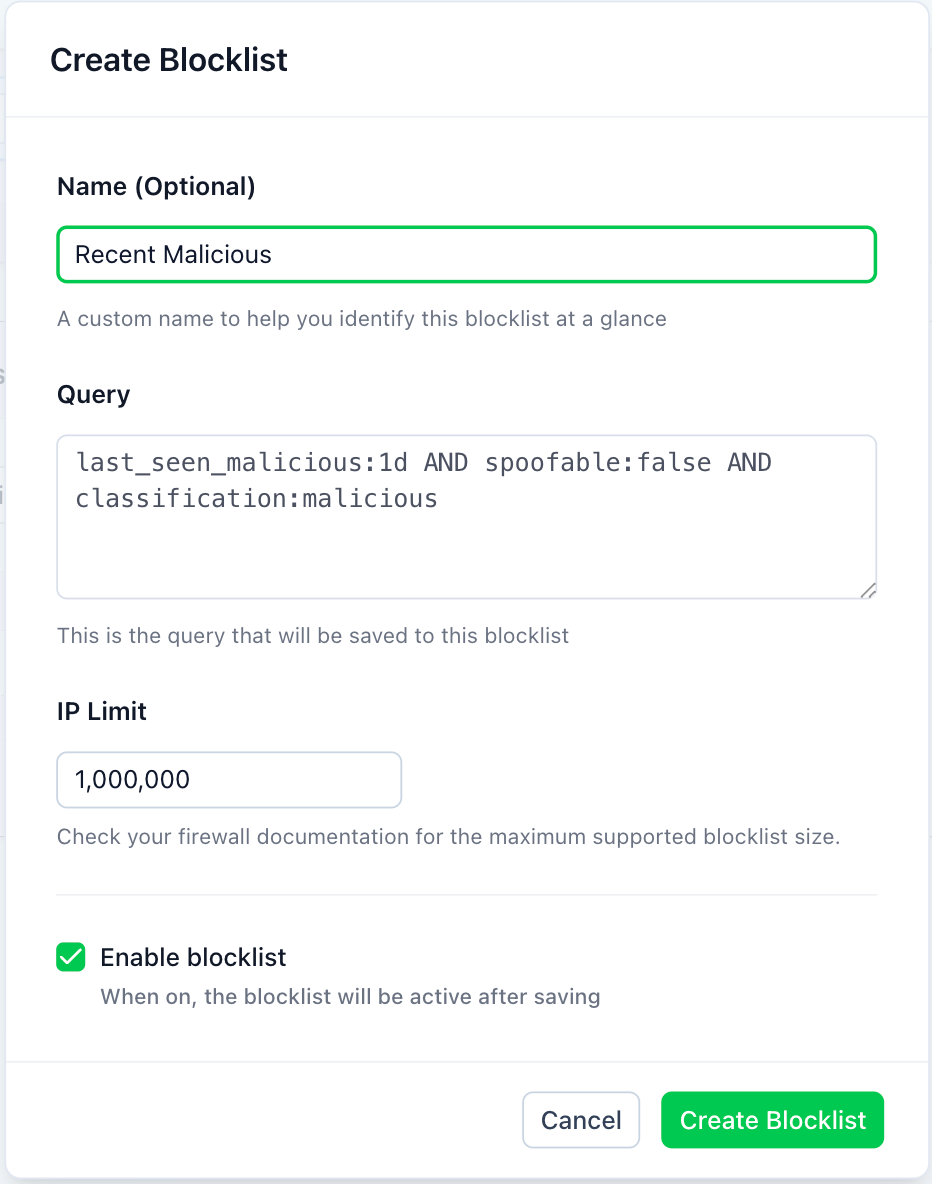
In the Create Blocklist dialog box, give the query a name and assign it an IP limit, which might be necessary if your firewall has a maximum supported size.
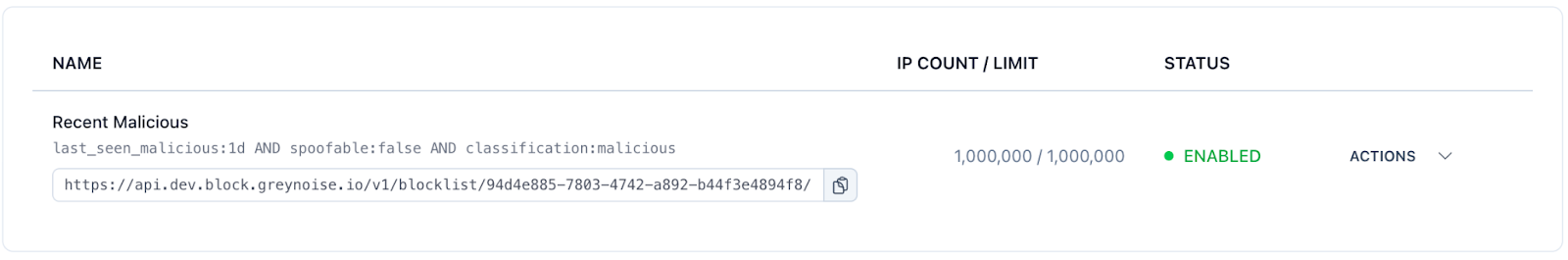
Once the block list is created, click the My Blocklists link at the top of the page to view the new block list and any others you have created. From the list, you can copy the blocklist URL to your firewall.
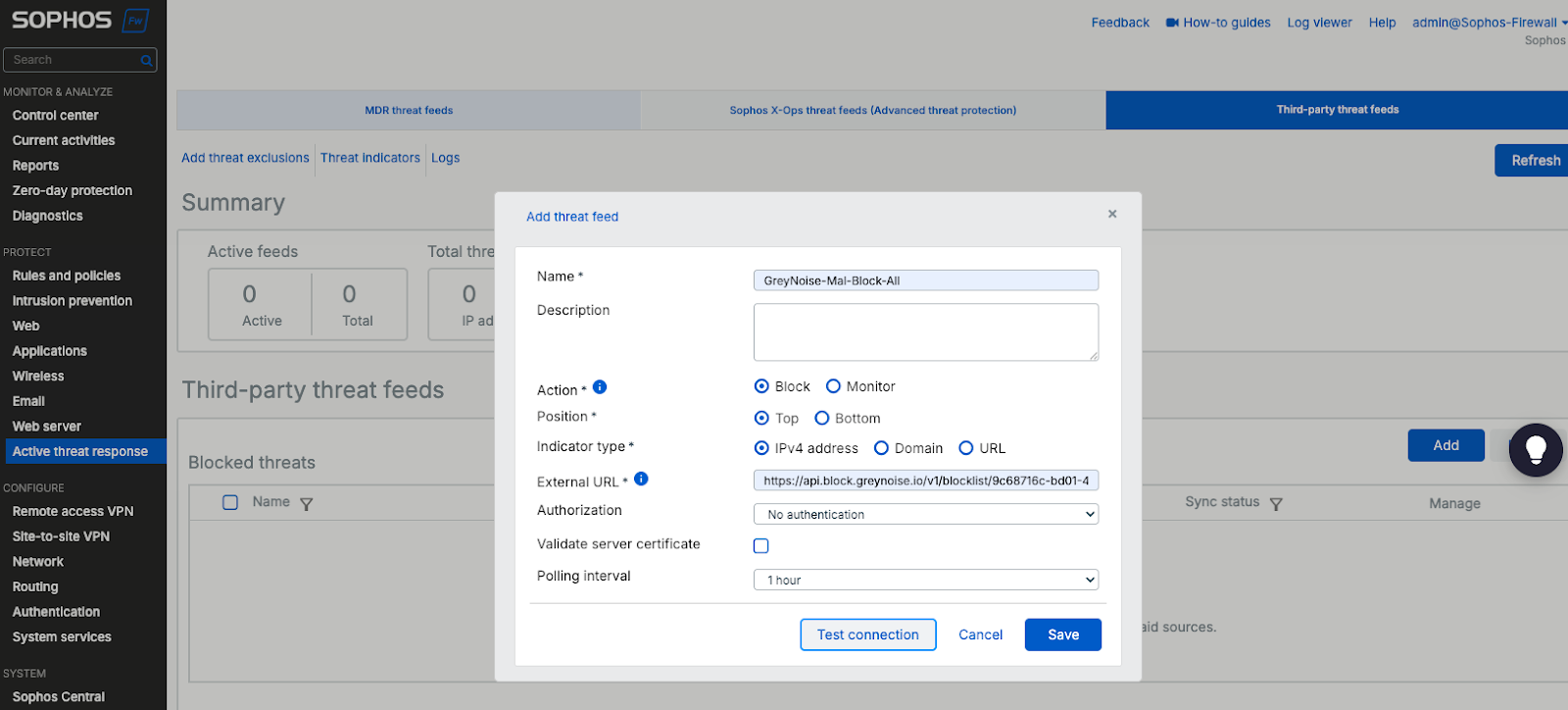
That’s all there is to it. Your firewall will periodically poll the blocklist URL and keep that bad traffic out of your network.
Sign Up Now for a Free Trial
GreyNoise Block is available now with a free trial for 14 days.






.png)





















.png)











.png)




.png)



.png)