GreyNoise is tracking a coordinated, automated credential-based campaign targeting enterprise VPN authentication infrastructure, with activity observed against Cisco SSL VPN and Palo Alto Networks GlobalProtect services over a two-day period in mid-December.
The activity reflects large-scale scripted login attempts, not vulnerability exploitation. Consistent infrastructure usage and timing indicate a single campaign pivoting across multiple VPN platforms.
GreyNoise has not observed evidence linking this activity to the campaign reported by Cisco Talos targeting Cisco Secure Email Gateway and Secure Email and Web Manager.
Palo Alto Networks GlobalProtect Activity
GreyNoise observed a large, session-heavy spike in automated login attempts targeting Palo Alto Networks GlobalProtect portals. The activity generated approximately 1.7 million sessions over a 16-hour period and was directed at GreyNoise’s emulated GlobalProtect and PAN-OS profiles.
More than 10,000 unique IPs attempted to log into GlobalProtect portals on 11 December.
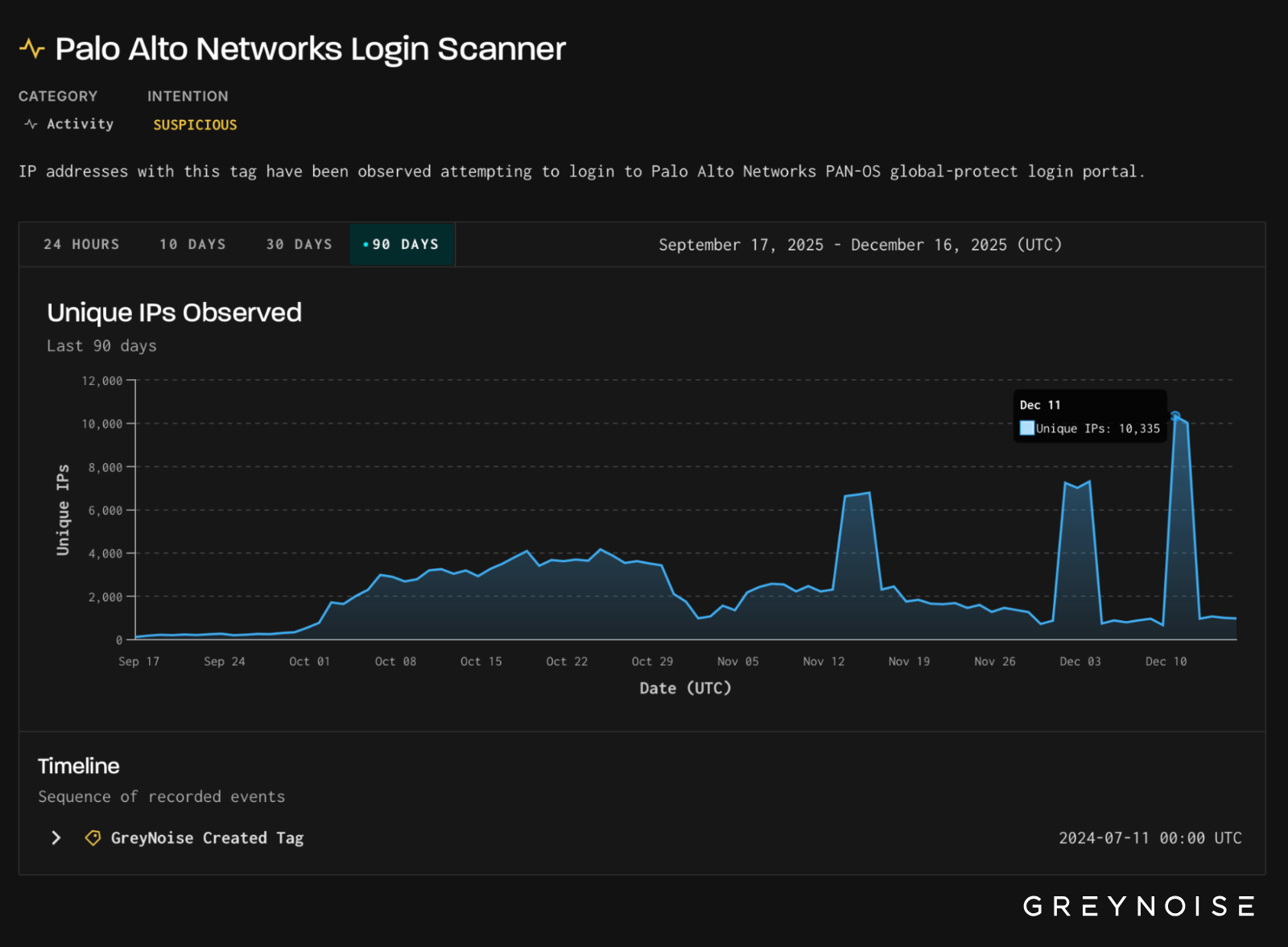
The activity targeted GlobalProtect portals geolocated primarily in the United States, Pakistan, and Mexico. Traffic originated almost exclusively from IP space associated with the hosting provider 3xK GmbH (Germany), indicating centralized, cloud-hosted infrastructure rather than distributed end-user behavior.
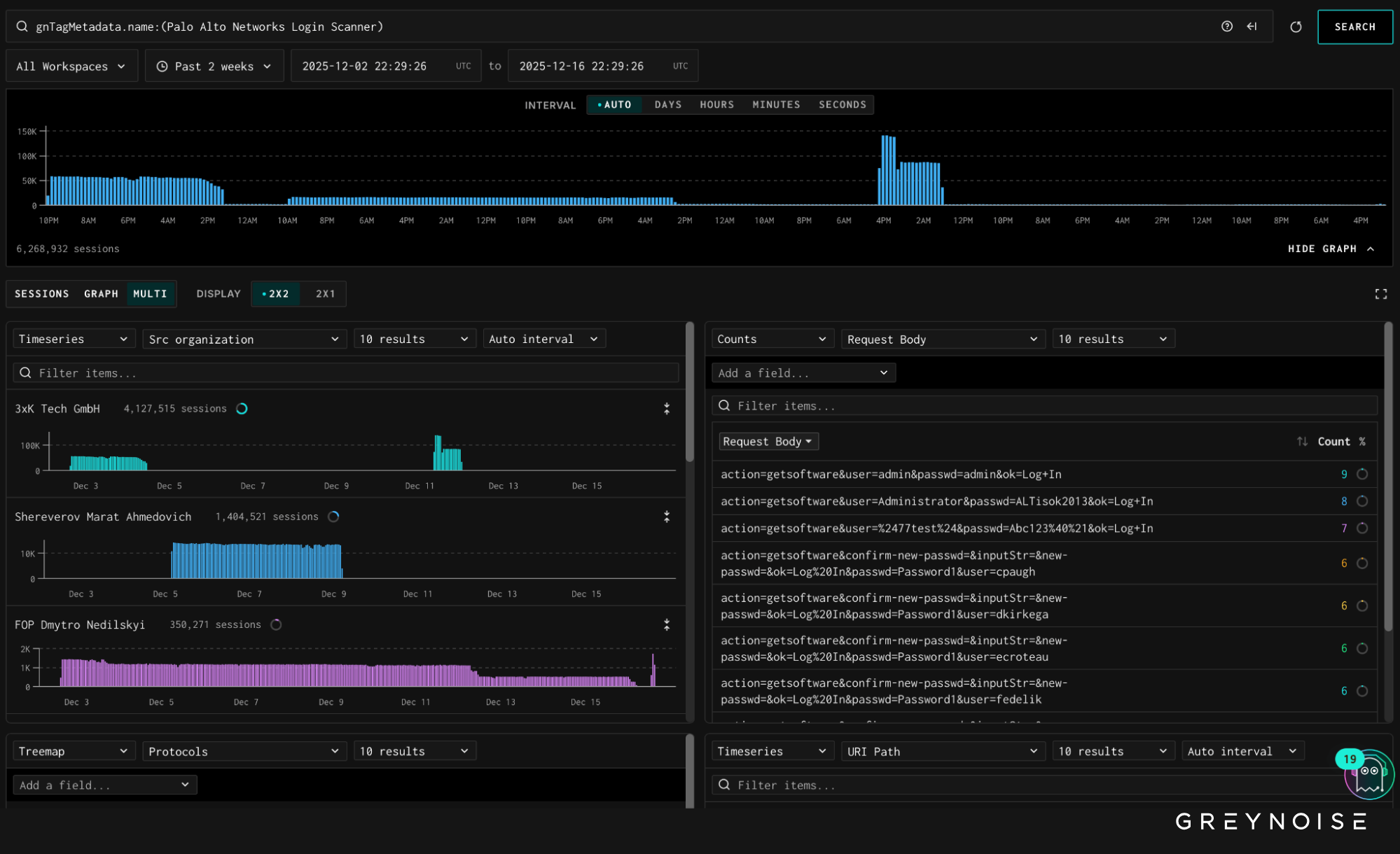
Observed Behavior
Login attempts followed a uniform request pattern and reused common username and password combinations. Most observed requests carried the same browser-like Firefox user agent, which is atypical for automated login activity originating from this provider.
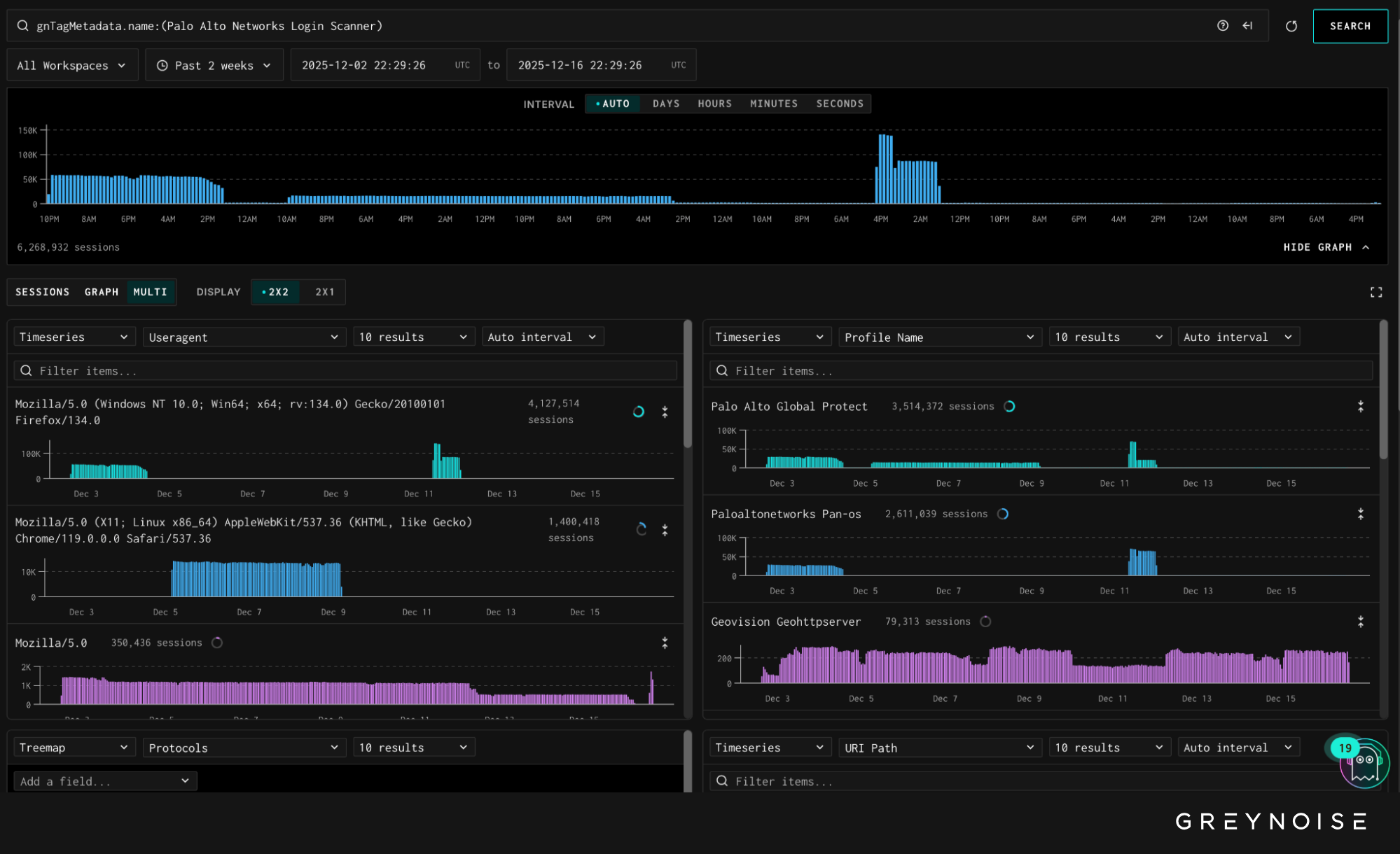
The consistency of the user agent, request structure, and timing suggests scripted credential probing designed to identify exposed or weakly protected GlobalProtect portals, rather than interactive access attempts or vulnerability exploitation.
This activity reflects continued pressure against enterprise VPN authentication endpoints, a pattern GreyNoise has observed repeatedly during periods of heightened attacker activity. The behavior is notable due to the sharp rise in traffic in a short period of time, potentially reflecting the initiation of a new automated campaign or an attempt to inventory exposed GlobalProtect instances at scale.
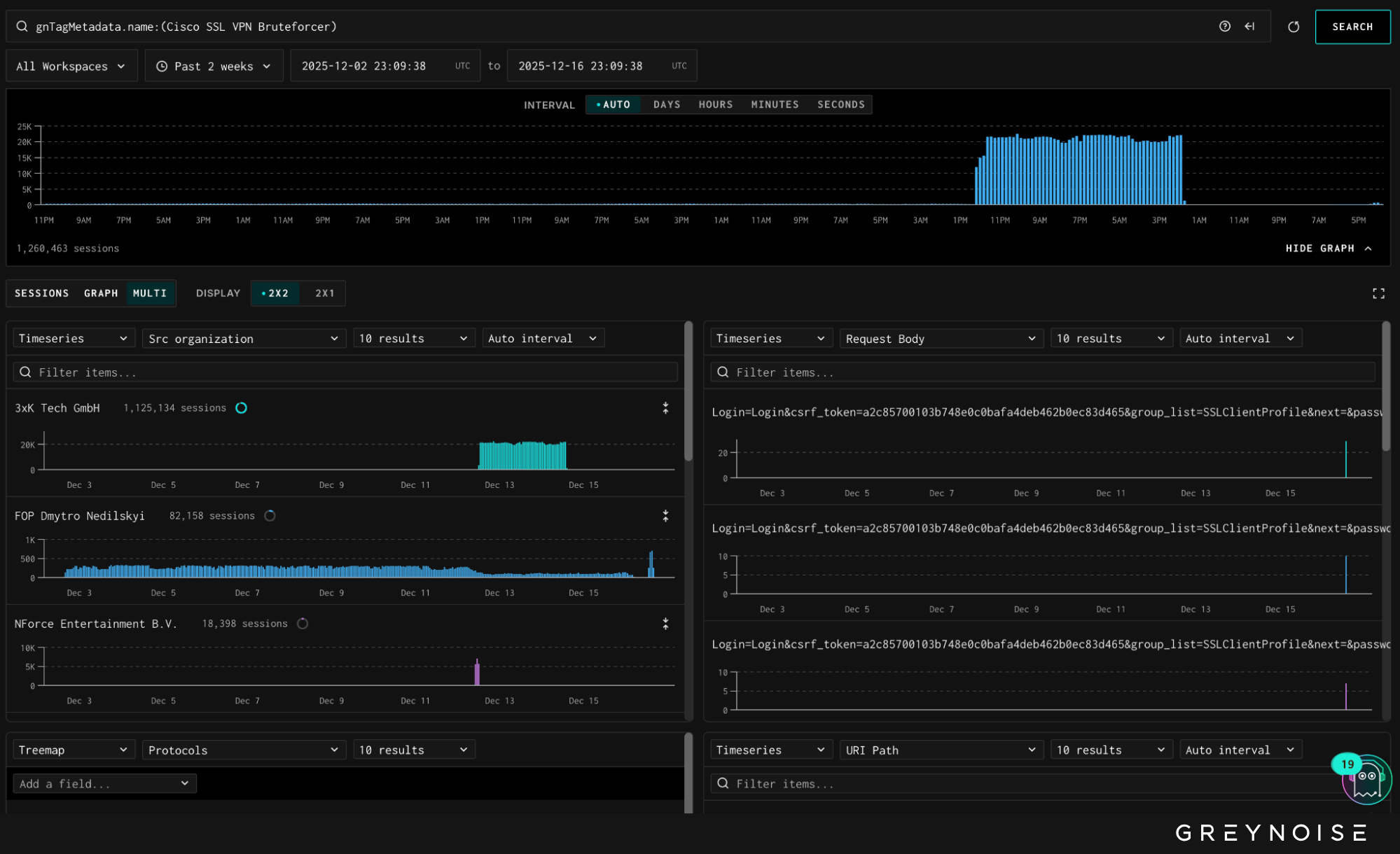
Cisco SSL VPN Activity Follows
On 12 December, GreyNoise observed a sharp surge in opportunistic bruteforce login attempts targeting Cisco SSL VPN endpoints. Daily unique attacking IPs rose from a typical baseline of fewer than 200 to 1,273 IPS, representing a significant deviation from normal activity. The majority of this traffic targeted GreyNoise’s facade sensors — vendor-agnostic systems listening on many ports and thereby implying opportunistic instead of targeted activity.
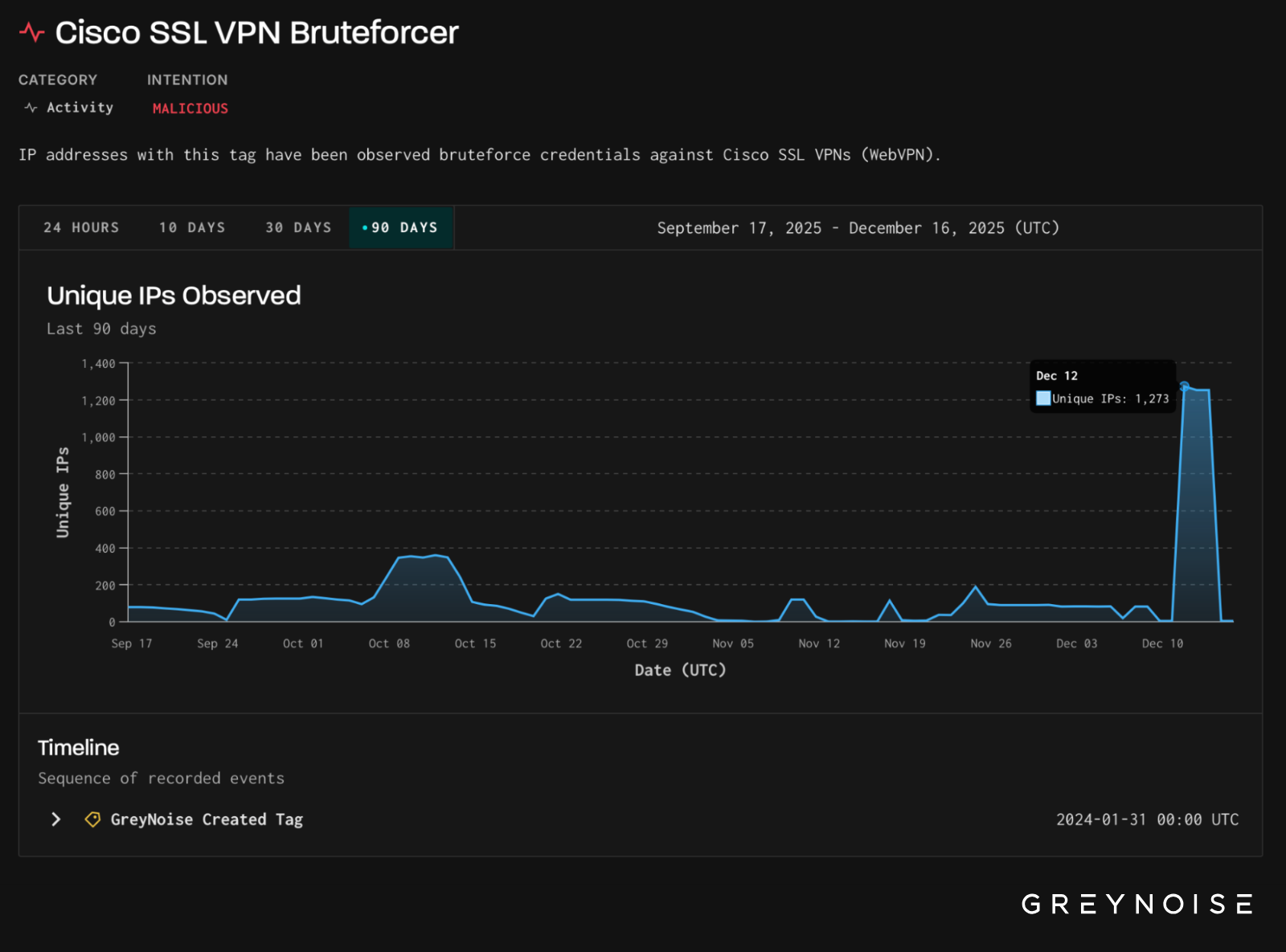
Analysis shows this activity is infrastructure- and tooling-linked to the Palo Alto GlobalProtect login attempts observed earlier in the week. Cisco SSL VPN traffic shares the same TCP fingerprint (GreyNoise customers, please check inbox for intel brief revealing the full signature) and originates from 3xK GmbH IP space — the same hosting provider leveraged to drive the Palo Alto login wave.
The dominant user agent across Cisco SSL VPN attempts was:
Mozilla/5.0 (Windows NT 10.0; Win64; x64)
This user agent is atypical for Cisco SSL VPN bruteforce activity sourced from 3xK infrastructure and marks the first time in the past 12 weeks that 3xK-hosted IPs have been deployed at scale against Cisco SSL VPN portals.
Observed request bodies indicate automated credential-based authentication attempts rather than vulnerability exploitation. Example payloads follow standard SSL VPN login workflows, including CSRF token handling and parameterized username/password fields, consistent with scripted password spraying or credential stuffing.
Recommended Actions
Security professionals can take meaningful steps to defend against this activity:
- Password/MFA Hygiene: Ensure all systems are protected with strong passwords and multi-factor authentication (MFA).
- Regular Edge Device Audits: Consistently audit Cisco and Palo Alto Networks appliances to assess whether or not login attempts are expected, or require escalation.
Additionally, GreyNoise platform customers should block all IPs above using our platform blocklists:
Non-GreyNoise customers can use the following GreyNoise Block templates to quickly and easily block threat IPs:
- Palo Alto Networks Login Scanner
- Cisco SSL VPN Bruteforcer Attacks
New users can try GreyNoise Block free for 14-days.
GreyNoise will continue monitoring this activity and make updates as necessary.
— — —
Stone is Head of Content at GreyNoise Intelligence, where he leads strategic content programs that translate complex internet-scale threat activity into clear, actionable insights. Previously, he led partnered research initiatives with Google and the U.S. Department of Homeland Security, and was a member of the Council on Foreign Relations Young Professionals group. His background spans finance, technology, and engagement with the United Nations on global policy issues.









.png)
.png)