Update: 8 October 2025
GreyNoise has identified several links between three recent campaigns:
- Cisco ASA scanning.
- Elevated login attempts against Palo login portals.
- Spike in brute force attempts against Fortinet SSL VPNs (new; info below).
We assess with high confidence that all three campaigns are at least partially driven by the same threat actor(s), evidenced by:
- Recurring fingerprint: shared TCP fingerprints across each campaign.
- Shared infrastructure: recurring subnets leveraged in each campaign.
- Temporal correlation: elevated activity at similar times across each campaign.
In addition to continued escalation of login attempts against Palo login portals, GreyNoise has identified likely related and coordinated credential brute forcing against Fortinet SSL VPNs. We are providing lists of credentials used in both campaigns:
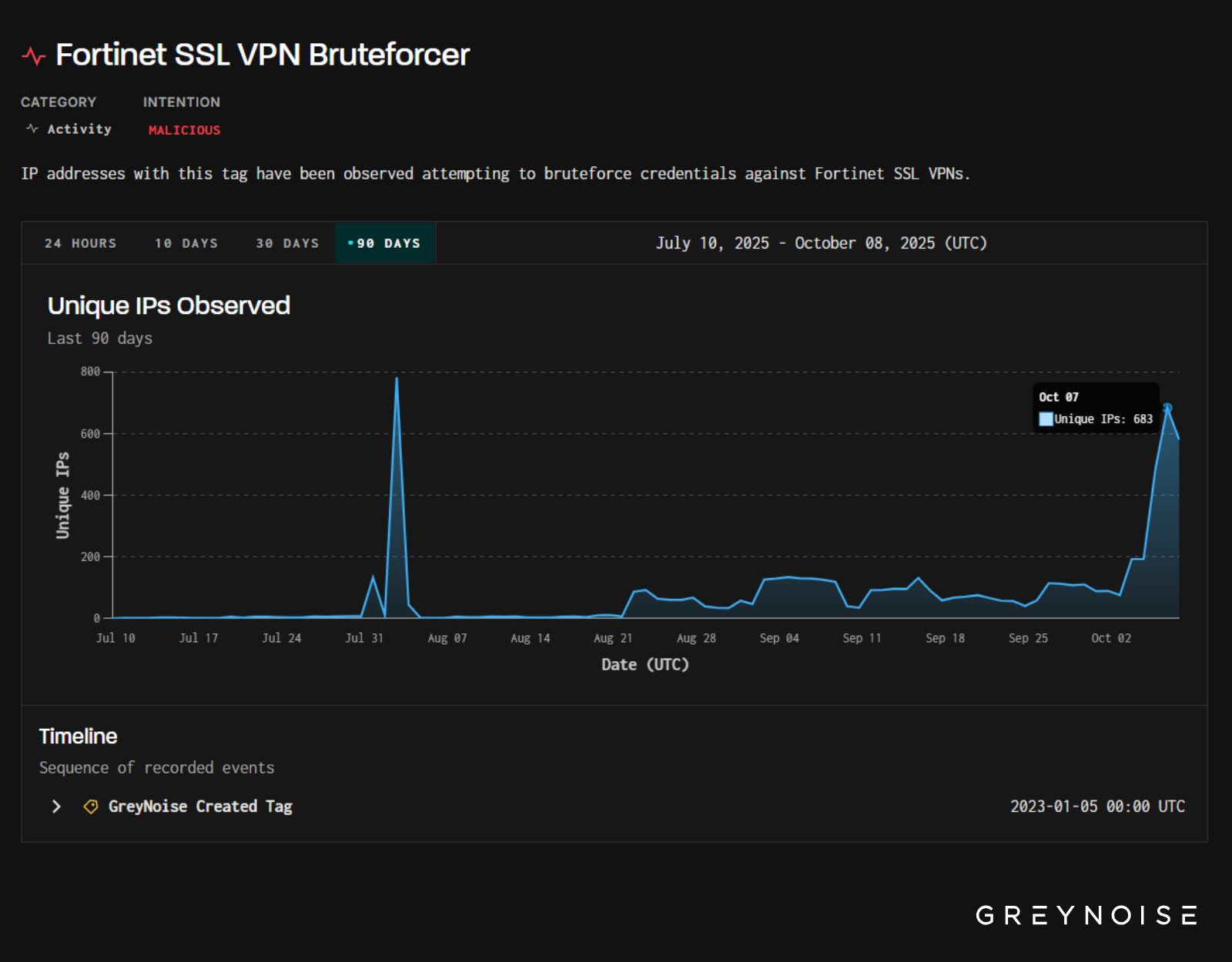
All three campaigns — Cisco ASA scanning, Palo login attempts, and Fortinet VPN brute forcing — heavily rely on the same subnets:
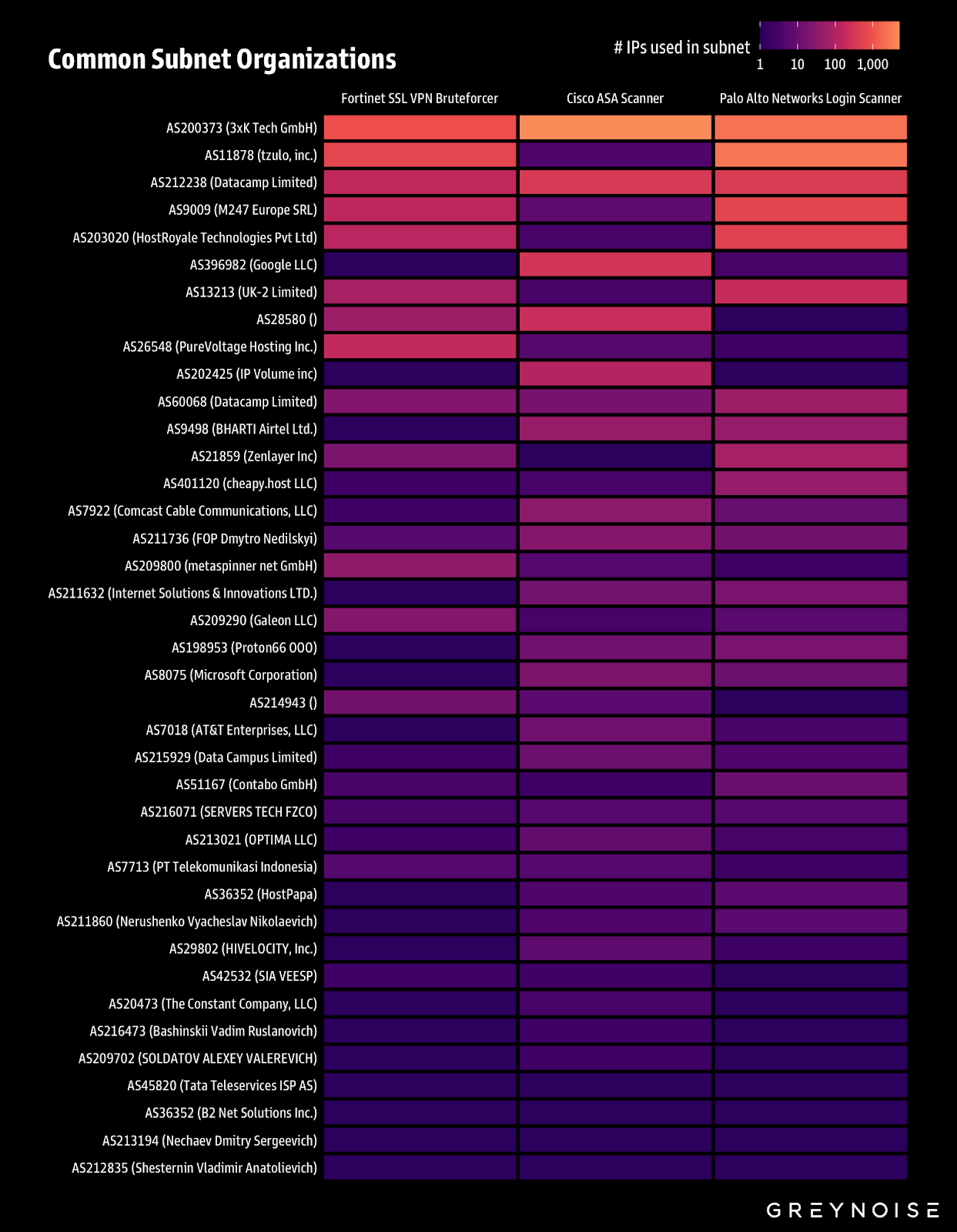
Use GreyNoise Block to directly block threat IPs from all relevant GreyNoise tags (ASA Scanner, Fortinet VPN Bruteforcer, Palo Scanner) and the below ASNs:
- AS200373 (3xK Tech GmbH)
- AS11878 (tzulo, Inc.)
Defenders can use GreyNoise Block to craft custom blocklists, instantly mitigating risk at the perimeter.
Elevated Fortinet Brute Force Attempts Correlated with New Vulnerabilities
In July, GreyNoise research identified a significant correlation:
Spikes in Fortinet VPN brute force attempts are typically followed by Fortinet VPN vulnerabilities disclosures within six weeks.
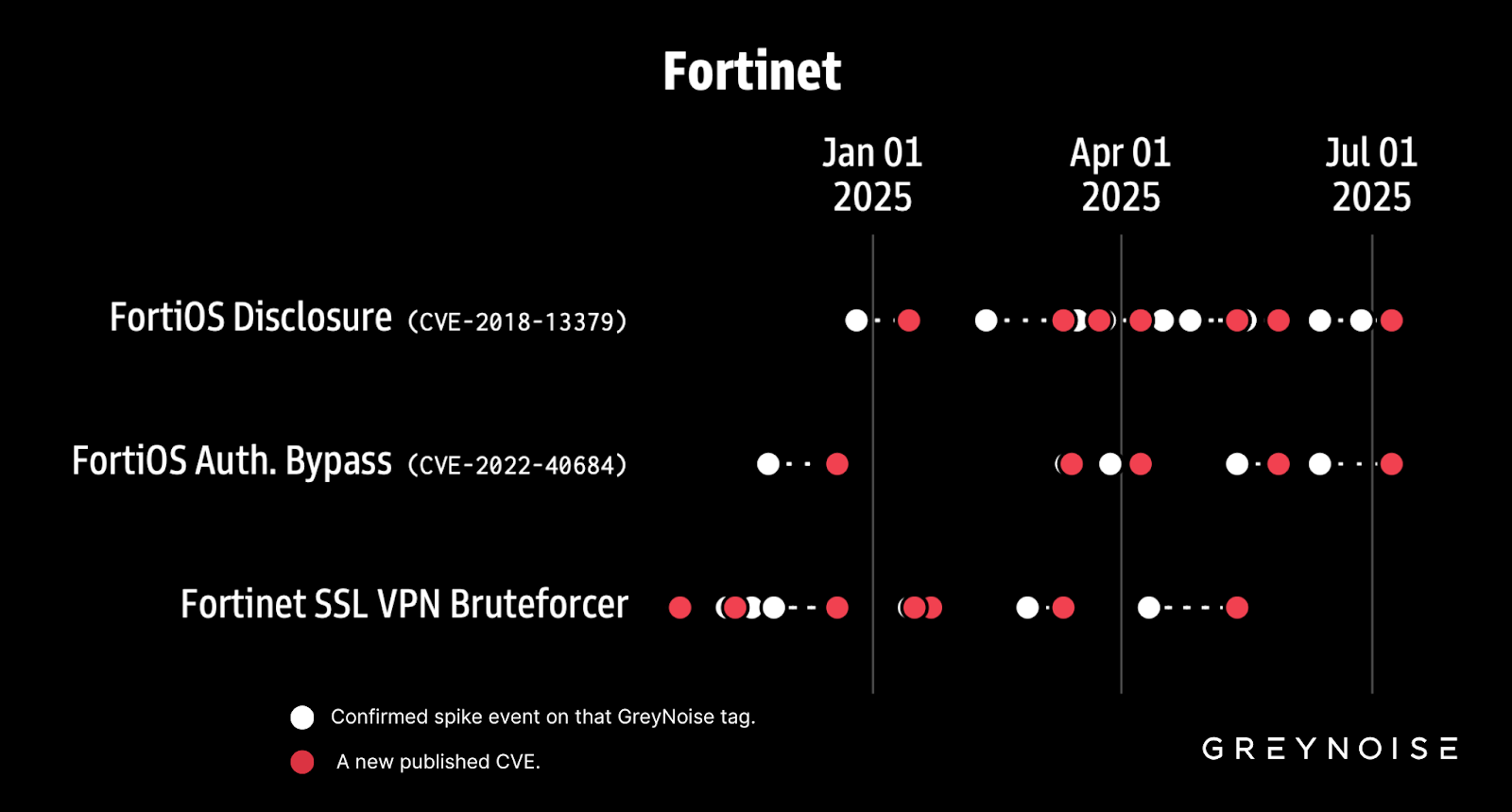
Block all IPs brute forcing Fortinet SSL VPNs, and consider hardening defenses for firewall and VPN appliances amid these findings.
Update: 7 October 2025
For defender review, GreyNoise has published a list of all unique usernames and passwords from Palo login attempts observed in the last week.
GreyNoise has produced an Executive Situation Report (SITREP) on the situation, intended for decision makers.
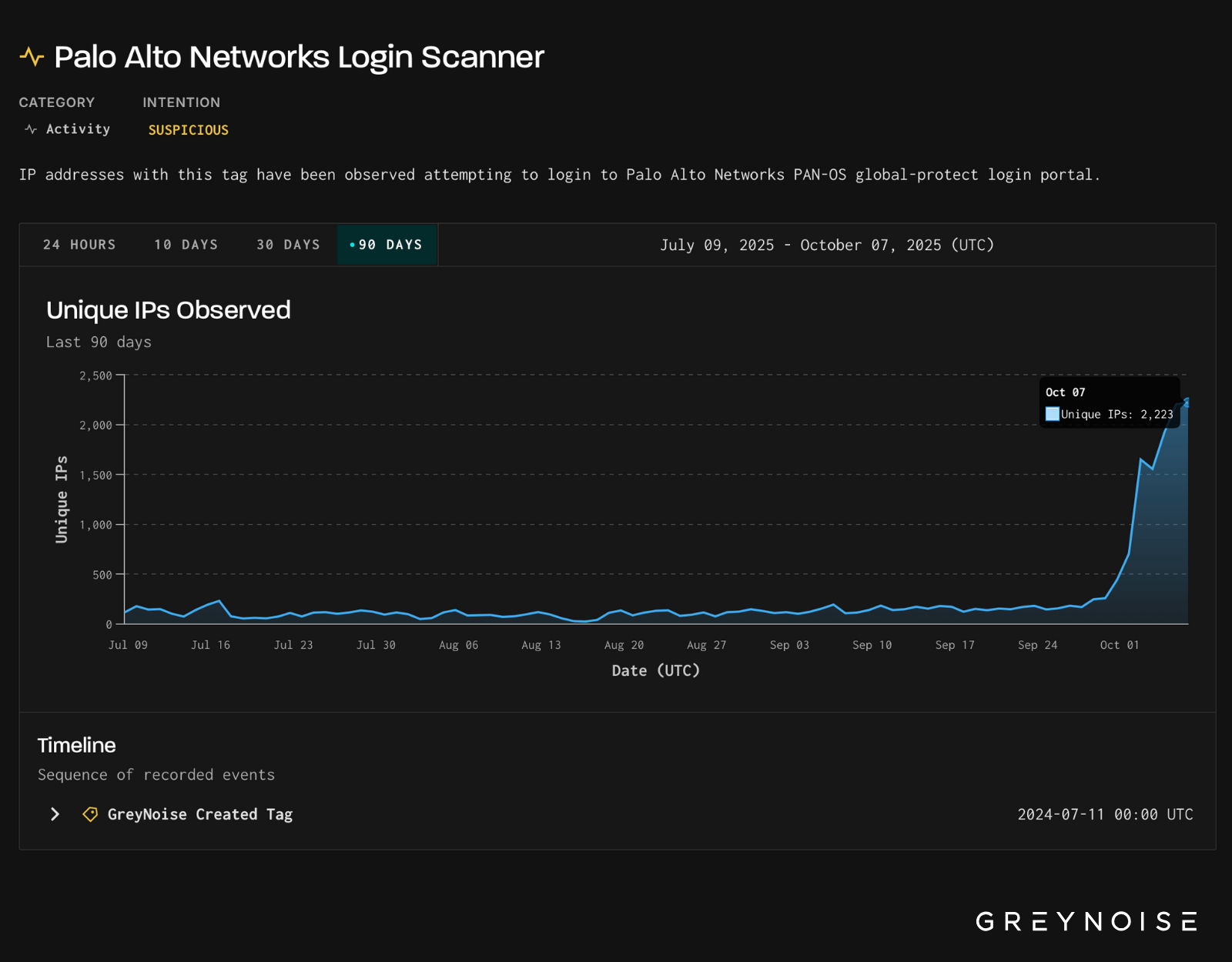
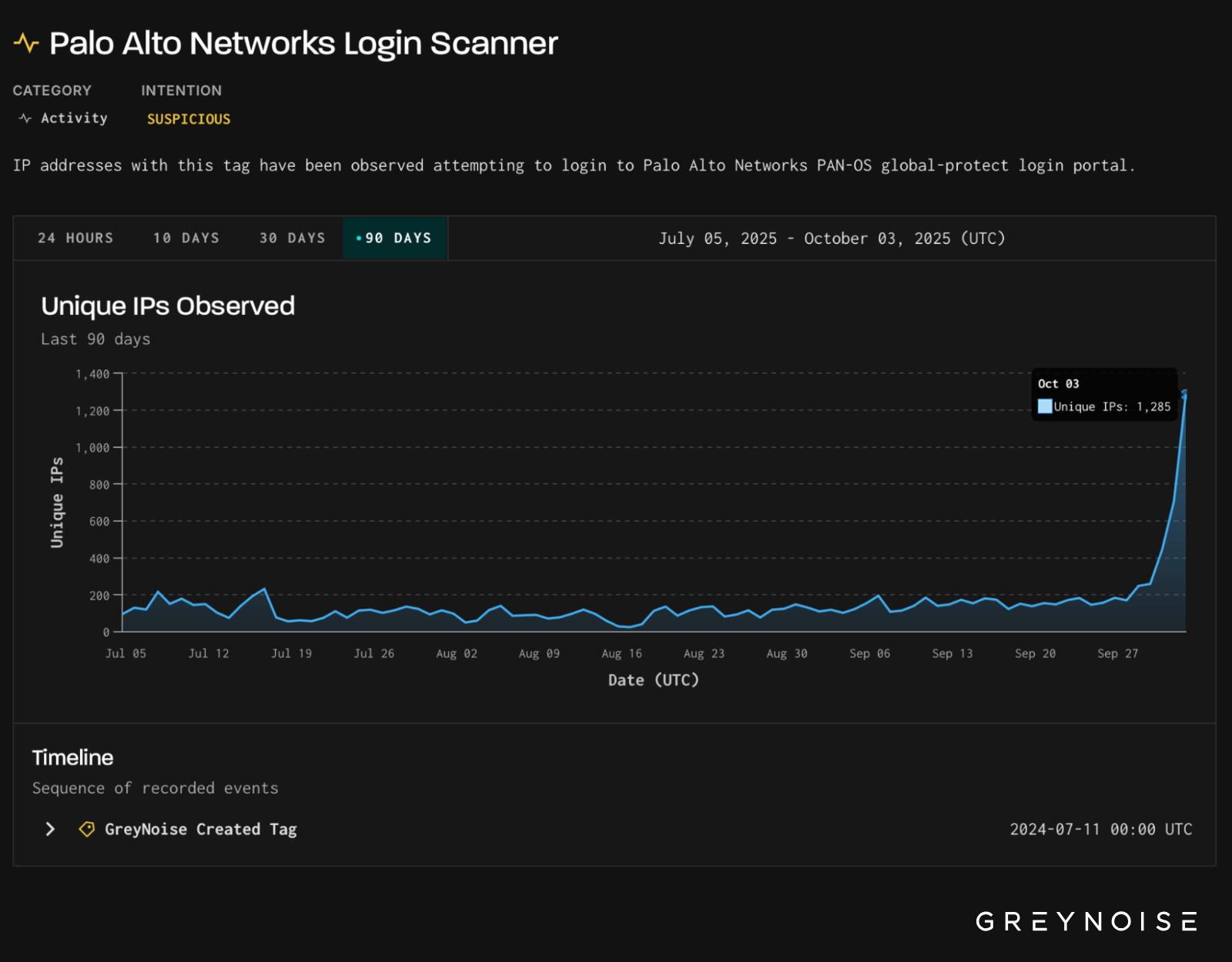
In the past days, GreyNoise has observed an escalation in scanning against Palo Alto Networks PAN-OS GlobalProtect login portals. Since our original reporting of ~1,300 IPs in the afternoon of 3 October, we have observed a sharp rise in the daily number of unique IPs scanning for Palo login portals. Peaking today on 7 October, over 2,200 unique IPs scanned for Palo login portals.
Increasing ASN Diversity Suggests Broadening Operator Involvement
In addition to an increase in the number of IPs involved, GreyNoise has observed a sharp increase in the unique count of ASNs involved in scanning Palo login portals, suggesting an increase in the number of threat actors involved.
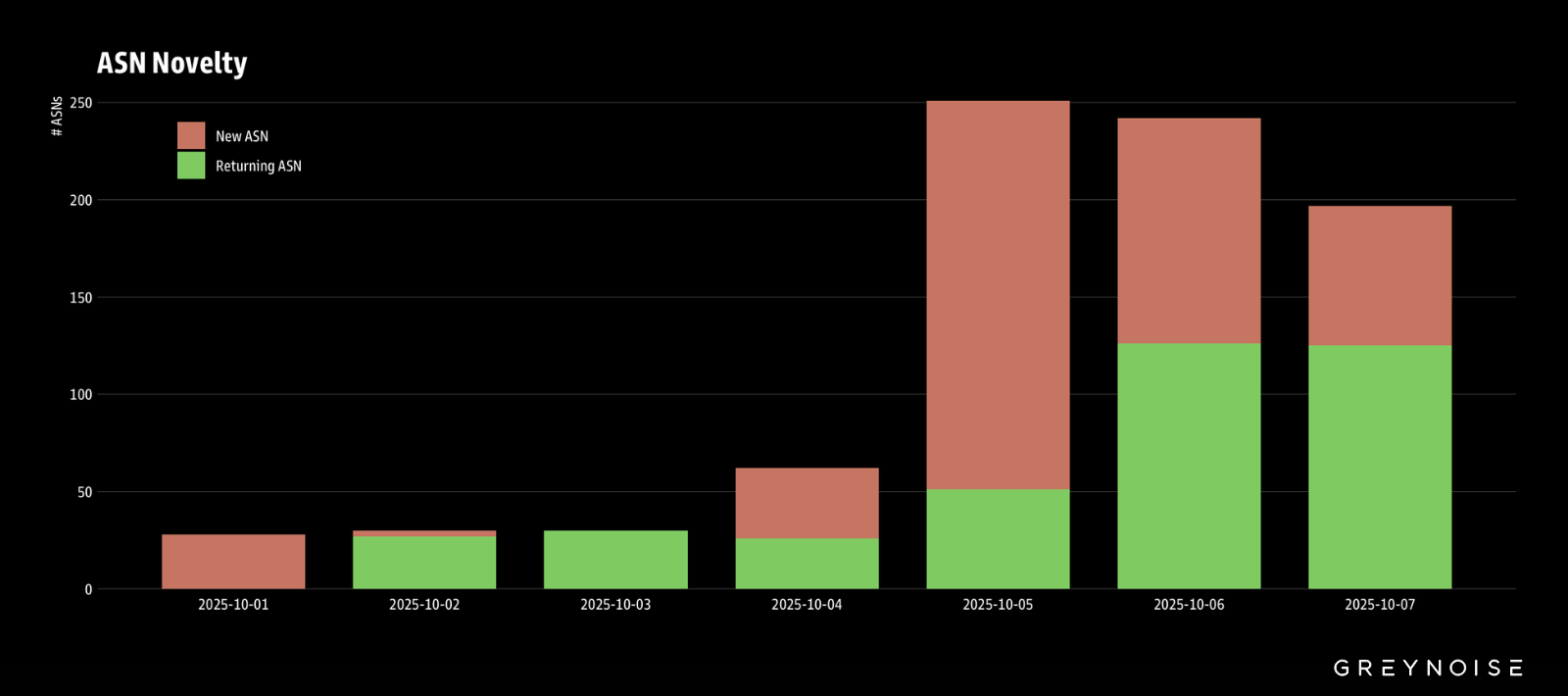
Separately, we discovered that approximately 12 percent of all ASN11878 subnets are allocated to scanning Palo login portals.
Potential Iteration Through Large Credential Dataset
The pace of login attempts suggests elevated activity may be driven by a threat actor(s) iterating through a large dataset of credentials.
.png)
On October 3, 2025, GreyNoise observed a ~500% increase in IPs scanning Palo Alto Networks login portals, the highest level recorded in the past 90 days.
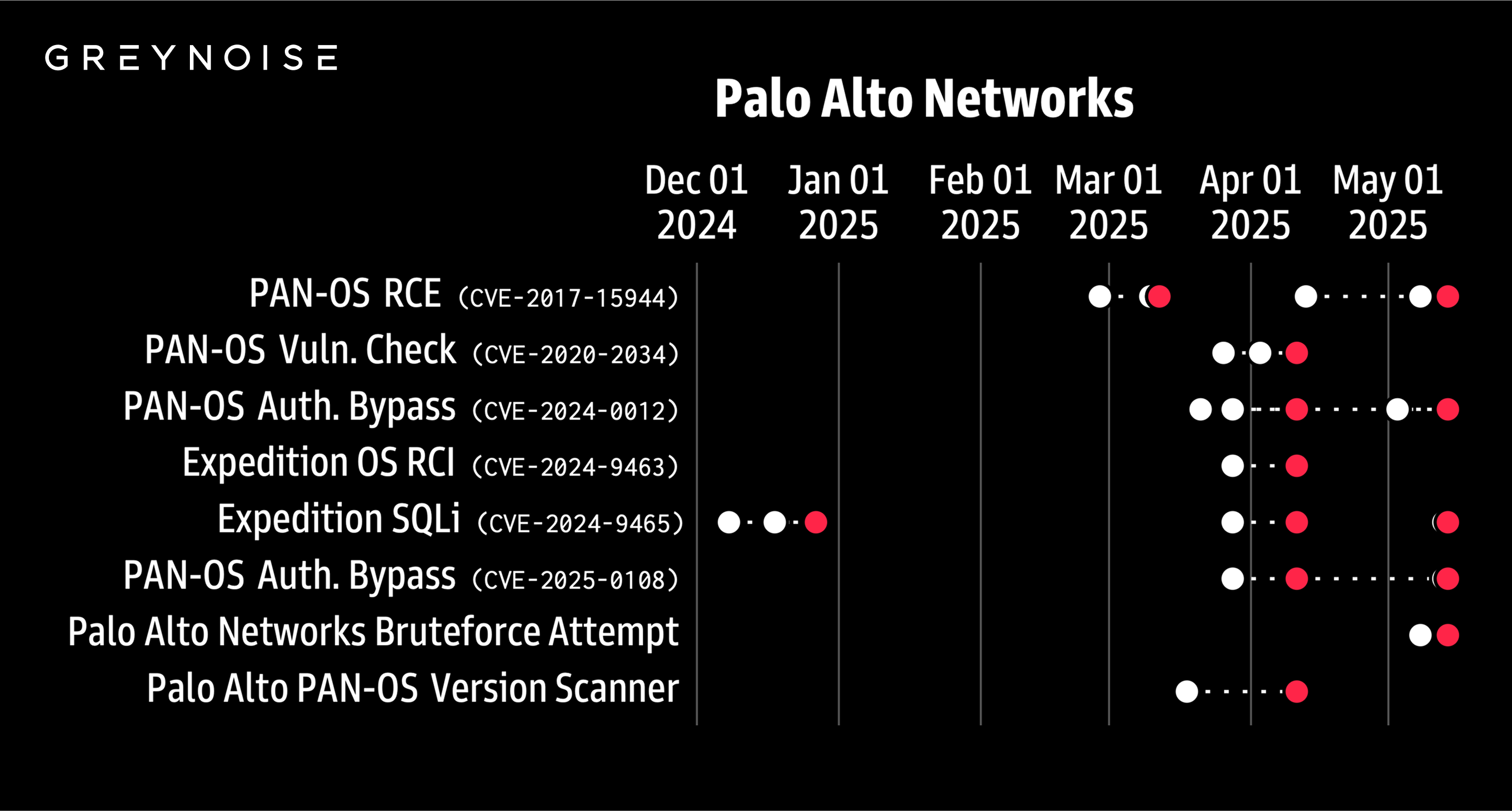
GreyNoise research in July found that surges in activity against Palo Alto technologies have, in some cases, been followed by new vulnerability disclosures within six weeks (see chart below). However, surges against GreyNoise’s Palo Alto Networks Login Scanner tag have not shown this correlation. GreyNoise will continue monitoring in case this activity precedes a new Palo Alto disclosure, which would represent an additive signal to our July research.
Key Findings
- Volume: ~1,300 unique IPs triggered GreyNoise’s Palo Alto Networks Login Scanner tag on 3 October. For the prior 90 days, daily volumes rarely exceeded 200 IPs.
- Classification: 93% of IPs were classified as suspicious and 7% as malicious.
- Source infrastructure: 91% of IPs geolocated to the United States, with smaller clusters in the U.K., Netherlands, Canada, and Russia.
- Targeted profiles: Nearly all activity was directed at GreyNoise’s emulated Palo Alto profiles (Palo Alto GlobalProtect, Palo Alto PAN-OS), suggesting the activity is targeted in nature, likely derived from public (e.g., Shodan, Censys) or attacker-originated scans fingerprinting Palo Alto devices.
- Destination focus: Distinct scanning clusters were observed in the past 48 hours. One directed most of its traffic toward the United States, while another concentrated on Pakistan – both from distinct TCP fingerprints but not without overlap. Environments/Sensors/Deployments based in Mexico, France, Australia, and the U.K. were also targeted.
Potentially Related Activity
GreyNoise analysis shows that this Palo Alto surge shares characteristics with Cisco ASA scanning occurring in the past 48 hours. In both cases, the scanners exhibited regional clustering and fingerprinting overlap in the tooling used. Both Cisco ASA and Palo Alto login scanning traffic in the past 48 hours share a dominant TCP fingerprint tied to infrastructure in the Netherlands. This comes after GreyNoise initially reported an ASA scanning surge before Cisco’s disclosure of two ASA zero-days.
These similarities indicate the activity may be related through shared tooling or centrally managed infrastructure, but GreyNoise cannot confirm whether it was carried out by the same operators or with the same intent.
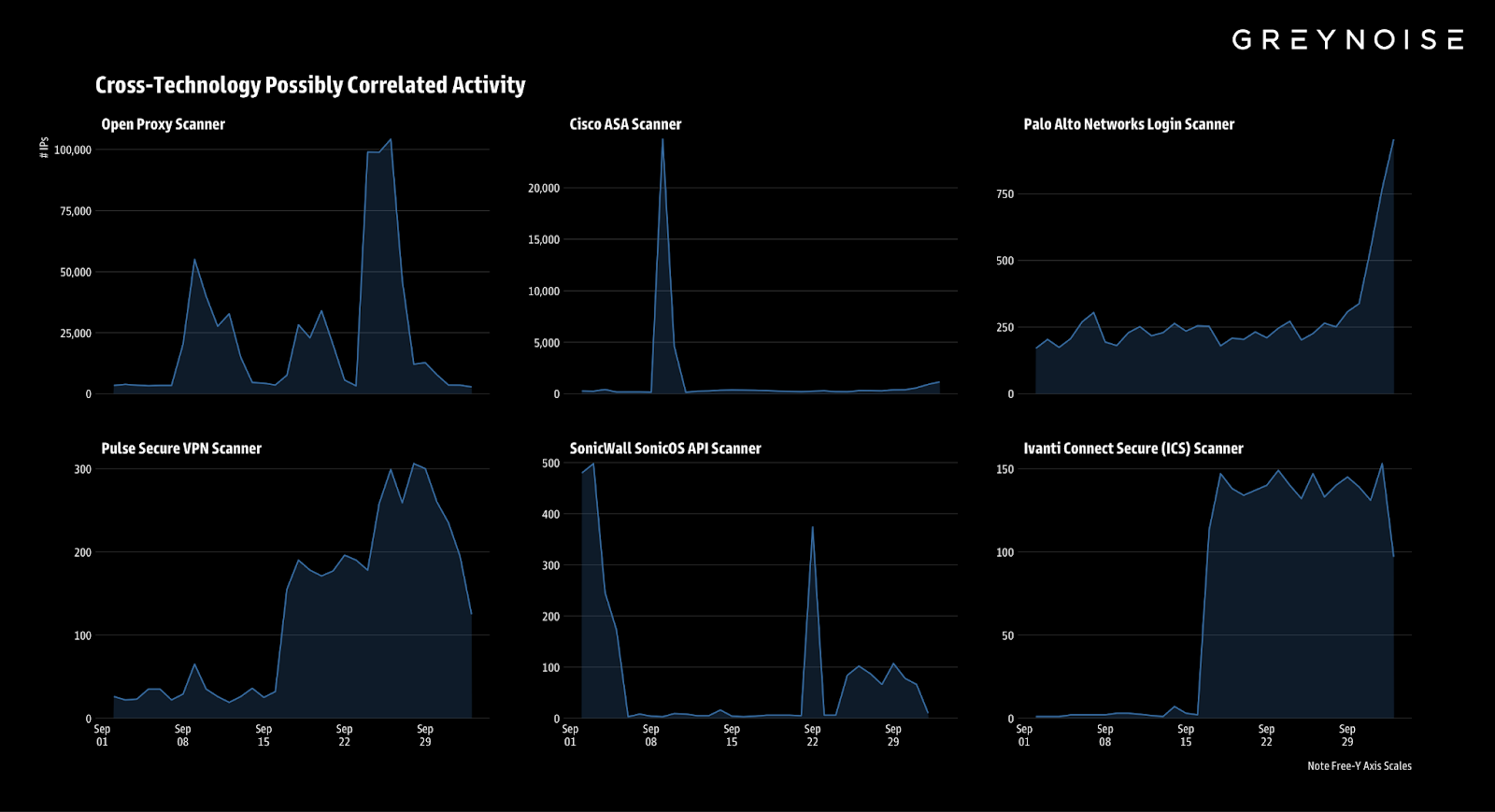
Cross-Tech Activity May Be Coordinated
In addition to a possible connection to ongoing Cisco ASA scanning, GreyNoise identified concurrent surges across remote access services. While suspicious, we are unsure if this activity is related.
Implications for Defenders
- The October 3 surge was the largest burst of IPs scanning for Palo Alto login portals in three months.
- Almost all participating infrastructure was first observed in the past 48 hours.
- Traffic was targeted and structured, aimed overwhelmingly at Palo Alto login portals and split across distinct scanning clusters.
These factors distinguish the surge from background noise and mark it as a clear reconnaissance event. GreyNoise will continue monitoring for potential follow-on exploitation attempts.
GreyNoise has developed an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats. Click here to learn more about GreyNoise Block.
— — —
This research and discovery was a collaborative effort between boB Rudis and Noah Stone, with additional contributions from Towne Besel.







.png)


.png)
.png)