Our Ollama honeypot infrastructure captured 91,403 attack sessions between October 2025 and January 2026. Buried in that data: two distinct campaigns that reveal how threat actors are systematically mapping the expanding surface area of AI deployments.
GreyNoise customers have received an Executive Situation Report (SITREP) including IOCs and other valuable intelligence from this investigation. Customers, please check your inbox.
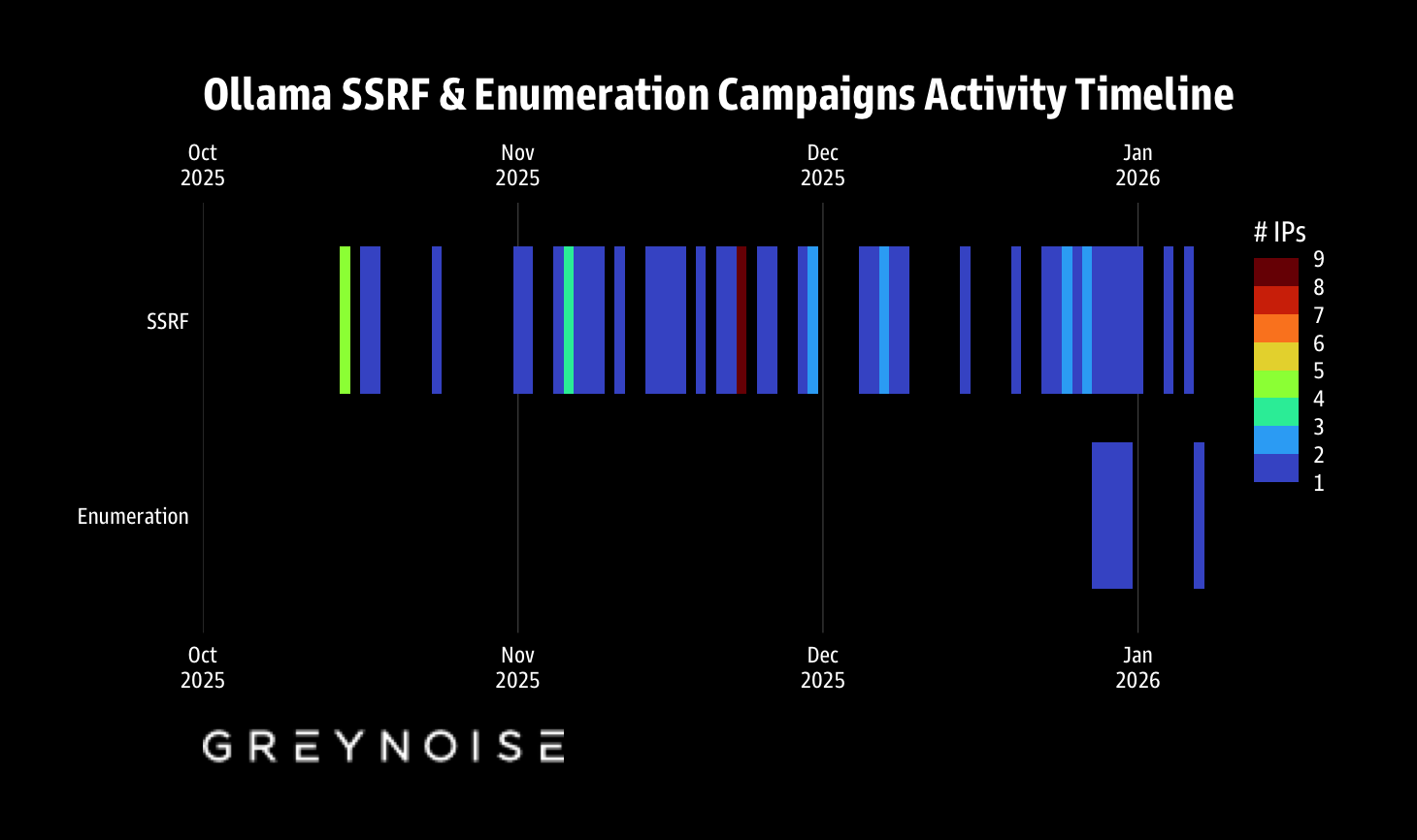
This corroborates and extends Defused’s findings.
The SSRF campaign: Forcing your servers to phone home
The first campaign exploited server-side request forgery vulnerabilities—tricks that force your server to make outbound connections to attacker-controlled infrastructure.
Attackers targeted two vectors:
- Ollama's model pull functionality: Injecting malicious registry URLs that force servers to make HTTP requests to attacker infrastructure
- Twilio SMS webhook integrations: Manipulating MediaUrl parameters to trigger outbound connections (we’re including this since they co-occurred with the Ollama targeting)
The campaign ran from October 2025 through January 2026, with a dramatic spike over Christmas—1,688 sessions in 48 hours. Attackers used ProjectDiscovery's OAST (Out-of-band Application Security Testing) infrastructure to confirm successful SSRF exploitation via callback validation.
Fingerprinting revealed the operation's structure. A single JA4H signature (po11nn060000…) appeared in 99% of attacks, pointing to shared automation tooling—likely Nuclei. The 62 source IPs spread across 27 countries, but consistent fingerprints indicate VPS-based infrastructure, not a botnet.
Assessment: Probably security researchers or bug bounty hunters. OAST callbacks are standard vulnerability research techniques. But the scale and Christmas timing suggest grey-hat operations pushing boundaries.
The enumeration campaign: Building the target list
This is the one that should concern you.
Starting December 28, 2025, two IPs launched a methodical probe of 73+ LLM model endpoints. In eleven days, they generated 80,469 sessions—systematic reconnaissance hunting for misconfigured proxy servers that might leak access to commercial APIs.
The attack tested both OpenAI-compatible API formats and Google Gemini formats. Every major model family appeared in the probe list:
- OpenAI (GPT-4o and variants)
- Anthropic (Claude Sonnet, Opus, Haiku)
- Meta (Llama 3.x)
- DeepSeek (DeepSeek-R1)
- Google (Gemini)
- Mistral
- Alibaba (Qwen)
- xAI (Grok)
Test queries stayed deliberately innocuous with the likely goal to fingerprint which model actually responds without triggering security alerts.
The infrastructure behind this campaign tells us who we're dealing with:
45.88.186.70 (AS210558, 1337 Services GmbH): 49,955 sessions 204.76.203.125 (AS51396, Pfcloud UG): 30,514 sessions.
Both IPs appear extensively in GreyNoise data with histories of CVE exploitation: CVE-2025-55182 (React2Shell), CVE-2023-1389, and over 200 other vulnerabilities. Combined observations exceed 4 million sensor hits.
Assessment: Professional threat actor conducting reconnaissance. The infrastructure overlap with established CVE scanning operations suggests this enumeration feeds into a larger exploitation pipeline. They're building target lists.
What to block
Network fingerprints
OAST callback domains
Block these TLD patterns (580 unique domains observed):
- *.oast.live
- *.oast.me
- *.oast.online
- *.oast.pro
- *.oast.fun
- *.oast.site
- *.oast.today
IP addresses
SSRF campaign (top 3):
- 134.122.136.119, 134.122.136.96 (AS152194, Japan)
- 112.134.208.214 (AS9329, Sri Lanka)
- 146.70.124.188, 146.70.124.165 (AS9009, Romania)
LLM enumeration campaign:
- 45.88.186.70 (AS210558, United States)
- 204.76.203.125 (AS51396, Netherlands)
Defend your LLM infrastructure
- Lock down model pulls. Configure Ollama to accept models only from trusted registries. Egress filtering prevents SSRF callbacks from reaching attacker infrastructure.
- Detect enumeration patterns. Alert on rapid-fire requests hitting multiple model endpoints. Watch for the fingerprinting queries: "How many states are there in the United States?" and "How many letter r..."
- Block OAST at DNS. Cut off the callback channel that confirms successful exploitation.
- Rate-limit suspicious ASNs. AS152194, AS210558, and AS51396 all appeared prominently in attack traffic.
- Monitor JA4 fingerprints. The signatures we identified will catch this tooling—and similar automation—targeting your infrastructure.
Eighty thousand enumeration requests represent investment. Threat actors don't map infrastructure at this scale without plans to use that map. If you're running exposed LLM endpoints, you're likely already on someone's list.







.png)


.png)