In 2025, 59 vulnerabilities silently flipped to "known ransomware use." If CISA updates a vulnerability's status in the Known Exploited Vulnerabilities (KEV) catalog and nobody notices, did it even matter?
Stick around to the end for a new tool that exposes these hidden flips. But first, some background.
The Silent Flip
In October 2023, CISA added a knownRansomwareCampaignUse field to KEV, designed to help organizations prioritize more effectively. Relying on KEV for prioritization is already a trailing indicator, and waiting for the ransomware flag is even slower. But I get it: practitioners often need substantial evidence to move the needle internally. (Another problem for another day.)
CISA doesn't just flag ransomware usage when vulnerabilities are added. They also silently update existing entries.
When that field flips from "Unknown" to "Known," CISA is saying: "We have evidence that ransomware operators are now using this vulnerability in their campaigns." That's a material change in your risk posture. Your prioritization calculus should shift. But there's no alert, no announcement. Just a field change in a JSON file.
This has always frustrated me. So I dug into the 2025 data to surface every silent flip.
What Was Found
59 vulnerabilities flipped.
Tracking these changes required pulling down a daily snapshot of KEV throughout 2025 and diffing the dailies for field changes. Silly, right?
Edge Devices Everywhere
Fortinet SSL-VPN. Ivanti Connect Secure. Palo Alto GlobalProtect. Check Point Security Gateway. Ransomware operators are building playbooks around your perimeter.
19 of the 59 target network security appliances, the very devices deployed to protect organizations. Legacy bugs show up too; Adobe Reader vulnerabilities from years ago suddenly became ransomware-relevant.
Authentication bypasses and RCE vulnerabilities led the pack as ransomware operators prioritize "get in and go" attack chains.
The Usual Suspects
The vendor breakdown shouldn't surprise anyone:
- Microsoft: 16 CVEs (SharePoint, Print Spooler, Group Policy, Mark-of-the-Web bypasses, and more)
- Ivanti: 6 CVEs (Connect Secure auth bypass, command injection, SSRF, EPM)
- Fortinet: 5 CVEs (FortiOS SSL-VPN heap overflows)
- Palo Alto Networks: 3 CVEs (PAN-OS auth bypass, GlobalProtect command injection, privilege escalation)
- Zimbra: 3 CVEs (still a reliable vector for email compromise)
Ransomware operators are economic actors after all. They invest in exploit development for platforms with high deployment and high-value access. Firewalls, VPN concentrators, and email servers fit that profile perfectly.
The Acceleration Problem
While some CVEs sat in KEV for years before the ransomware flag, the 2025 crop moved fast:
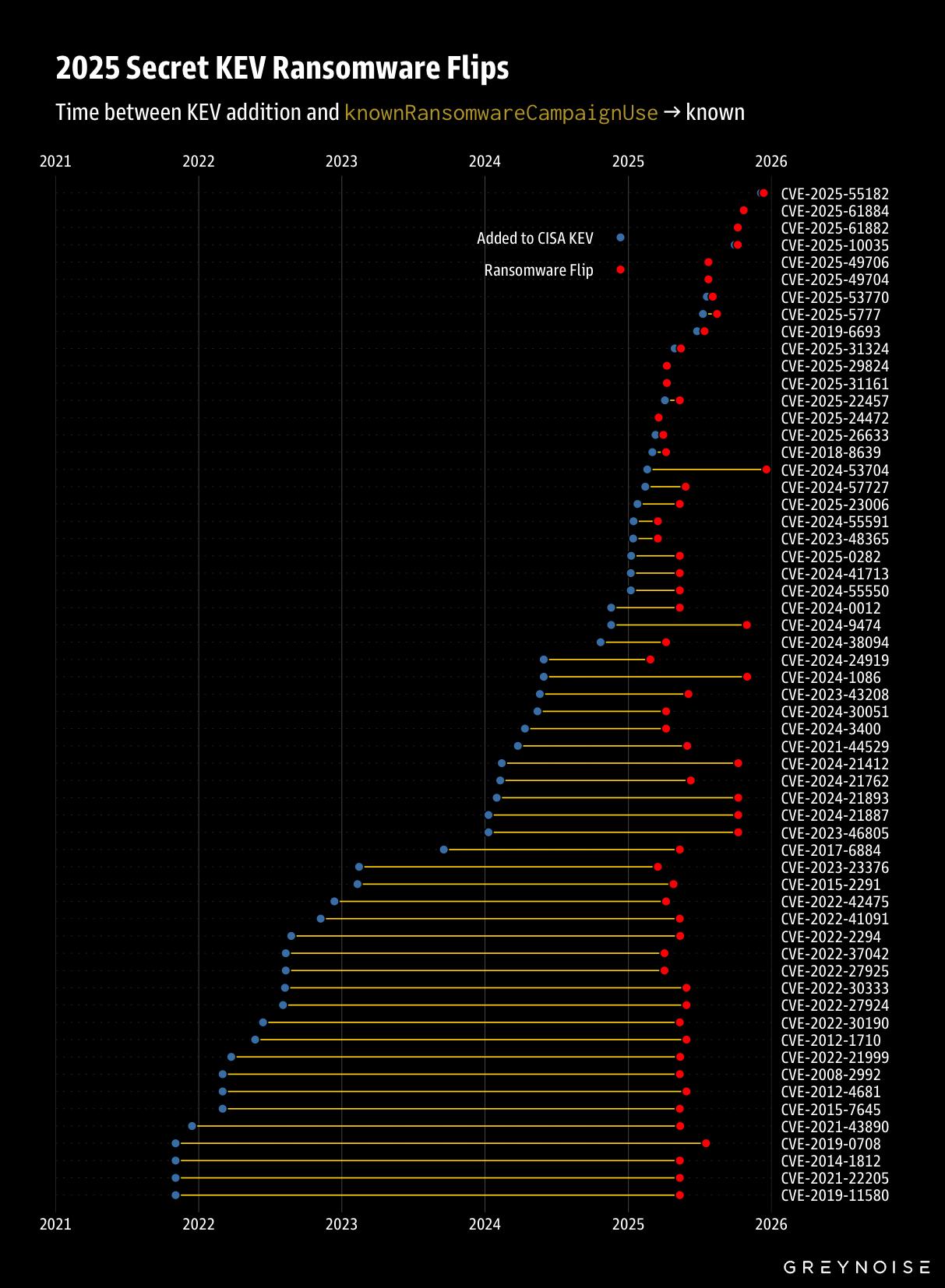
Today, ransomware operators are integrating fresh exploits into their playbooks faster than defenders are patching.
So What Can You Do About the Silent Flips?
Watch knownRansomwareCampaignUse. When it flips from "Unknown" to "Known," reassess, especially if you've been deprioritizing that patch because "it's not ransomware-related yet."
Since my presentation at BSidesLV in 2024, I've hoped to see CISA provide more transparency by releasing a changelog or an RSS feed whenever updates occur, similar to the additions feed they already maintain. After complaining expressing my desires, my boss made encouraged me to create a solution myself.
So here it is:
Subscribe to the RSS feed at https://kev.labs.greynoise.io/kev-ransom-feed.rss
It checks hourly and will notify you whenever a ransomware flag flips. No more silent changes.
Recent Flips (January 28, 2026)
As an aside, the most recent flips occurred just a few days ago:
- CVE-2024-49039 (Unknown → Known) — Microsoft Windows Task Scheduler Privilege Escalation Vulnerability
- CVE-2024-51567 (Unknown → Known) — CyberPanel Incorrect Default Permissions Vulnerability
- CVE-2024-9680 (Unknown → Known) — Mozilla Firefox Use-After-Free Vulnerability
- CVE-2024-30088 (Unknown → Known) — Microsoft Windows Kernel TOCTOU Race Condition Vulnerability
The Bigger Picture
This data dive exposed a blind spot in how we consume threat intelligence. We're good at reacting to new disclosures. Decent at tracking active exploitation. But we're not great at noticing when the characterization of existing threats evolves.
CISA is already tracking these ransomware campaigns, correlating TTPs, and updating assessments. That intelligence only matters if defenders are watching the delta, not just the headlines.
So consider this your heads-up: the tree fell, and it absolutely made a sound. The question is whether your detection was tuned to hear it and whether it will be tomorrow.
Artifacts
The 59 CVEs that silently flipped in 2025:










.png)